Azure AD Seamless Login to replace Windows Authentication - Microsoft Identity Web App
Good evening, we had a question on Microsoft Identity authentication we hoped you could help with. Our team is transitioning some of our web applications (hosted on-premise) from using Windows Authentication to Azure AD authentication and we’re running into an issue when the browser cannot detect the user is “Logged in” to their Microsoft Account. This application is a ASP .NET 6 web application and the majority of our users are Windows users logged into their computers with Seamless SSO enabled at the AD level.
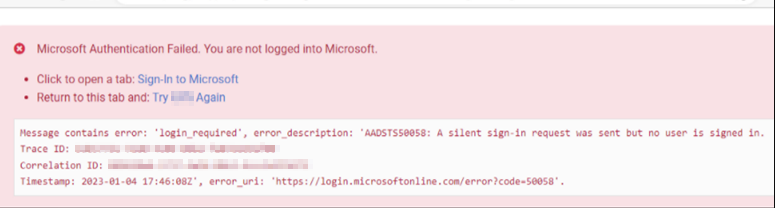
On an intermittent basis, a failure will occur and upon failure, we redirect the user to the below message in RED. "A silent sign-in request was sent but no user is signed in."
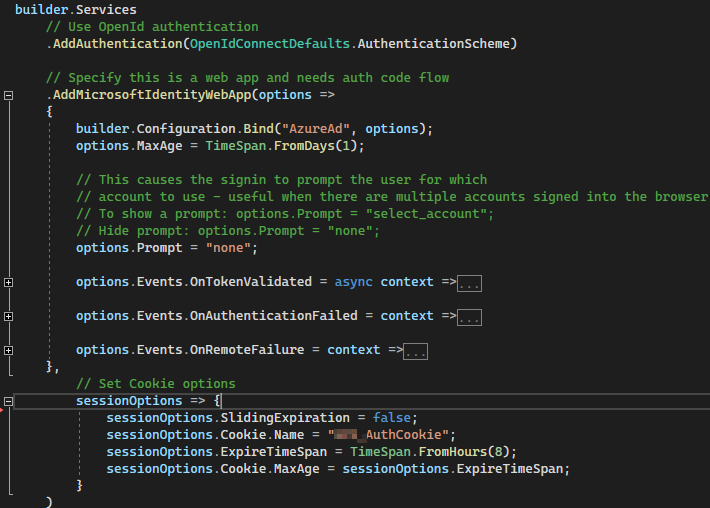
We have identified that the user isn’t sent to a prompt because we’ve set the below option to “none” in Program.cs – for a more seamless experience (similar to Windows Authentication). We realize we can possibly set this to "select_account" as well.
// Specify this is a web app and needs auth code flow
.AddMicrosoftIdentityWebApp(options =>
{
builder.Configuration.Bind("AzureAd", options);
options.MaxAge = TimeSpan.FromDays(1);
// This causes the signin to prompt the user for which
// account to use - useful when there are multiple accounts signed into the browser
// To show a prompt: options.Prompt = "select_account";
// Hide prompt: options.Prompt = "none";
options.Prompt = "none";
I can replicate the current issue if I do the following:
- Clear all my cookies and cache
- Visit the web application, the above error occurs and does not retry auth.
- After successfully authenticating to MS outside of the application
- I refresh the URL and the site allows access
- If I clear all my cookies and cache again, the site rejects authentication and does not retry.
We would like to know if there is a better way to have the application “re-authenticate” the user automatically, without a prompt. Our business users point to Windows Authentication "always working" for them and we'd like to try to best replicate this behavior with Azure AD. We realize we can set “options.Prompt” to “select_account”, but that would that prompt occur on every authentication?
Its previously mentioned to possibly provide login_hint or domain_hint, would this work? Where during the authentication process can that be set and how can I gather the login_hint during the .AddMicrosoftIdentityWebApp() setup process?
Thanks so much for any insight you might have, appreciate your time.