NSG in case S2S vnets
Hello ,
we are in this situation :
an onpremise offices is connected to vnet A with S2S connection ( vpn gateway A and Local firewall )
and vnet A is conected to vnet B with S2S connection ( we don't need to use peering for our situation , so we create a vpn gateway B and create connection S2S with vpn gateway A )
in onpremise Firewall , i have added the both vnet A and B as network destination when i parameter the vpn
also , in local network gateway B , i have added the both privates networks for vnet A and local network ( onpremise network )
this is the situation :
Onpremise Office <---s2s--->vnetA<---s2s---->vnetB
My question ,
i need user in onpremise office connect to vm in vnet B,how many NSG should create in this case ?
i have already create a rule in local FW to authorize local network to connect to VM in vnet B, and i have created ainbound rule for the VM to authorize all the flow coming from local network
but when i check , i can't connect to this VM
could you help ?
Regards
Azure VPN Gateway
Azure Virtual Network
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-06T09:40:45.983+00:00 Hello @APTOS ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
- How are you trying to connect to VM in Vnet B from Office A and what is the error message you are receiving?
- Is the issue only with this particular VM or other VMs as well in Vnet B?
Regards,
Gita -
APTOS 221 Reputation points
2023-01-06T10:14:48.693+00:00 Hello @GitaraniSharma-MSFT
i have allowed ICMP and RDP to connect to this VM but i can't ping or do a remote session .i have disabled the windows firewall for the VM to be sure .
May be i have to add Something to route Traffic in my scenario !! how traffics coming from onpremise network to vNet B throught vNet A work ? may be if i undestand this could resolve my issue!
Thanks and any suggestions to resolve this
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-06T11:15:24.11+00:00 Hello @APTOS ,
Looks like we were working on a Vnet peering issue in another thread and the proposed end setup was:
Office C<------>S2S<------>VnetC<------>S2S<------>VnetA<------>S2S<------>Vnet B<------>S2S<------>Office BYou confirmed that the below part worked for you:
Office C<------>S2S<------>VnetC<------>S2S<------>VnetA
Could you confirm again if the above setup is working for you?Now you are testing the remaining part and facing issue:
VnetA<------>S2S<------>Vnet B<------>S2S<------>Office BMaybe you have changed the naming convention in this thread i.e. OfficeA <---s2s--->vnetA<---s2s---->vnetB
- Could you please confirm if you are able to reach office A from a VM in Vnet B?
- Also, I would request you to check the effective routes of the VM in Vnet B to see if you have a route to Office B?
Refer : https://learn.microsoft.com/en-us/azure/virtual-network/diagnose-network-routing-problem#diagnose-using-azure-portal
Regards,
Gita -
APTOS 221 Reputation points
2023-01-06T13:23:27.323+00:00 Maybe you have changed the naming convention in this thread i.e. OfficeA <---s2s--->vnetA<---s2s---->vnetB -> Yes :)
Could you please confirm if you are able to reach office A from a VM in Vnet B? --> Yes
I would request you to check the effective routes of the VM in Vnet B to see if you have a route to Office B? --> Yes n exist
should i have to creates rule in vNet A to forw
-
APTOS 221 Reputation points
2023-01-06T13:25:33.873+00:00 Maybe you have changed the naming convention in this thread i.e. OfficeA <---s2s--->vnetA<---s2s---->vnetB -> Yes :)
Could you please confirm if you are able to reach office A from a VM in Vnet B? --> Yes
I would request you to check the effective routes of the VM in Vnet B to see if you have a route to Office B? --> Yes n exist
should i have to create rules in vNet A to forward traffic to subnet in vnet B ? or by default the forward is enabled
-
APTOS 221 Reputation points
2023-01-06T13:39:53.283+00:00 Maybe you have changed the naming convention in this thread i.e. OfficeA <---s2s--->vnetA<---s2s---->vnetB -> Yes
Could you please confirm if you are able to reach office A from a VM in Vnet B? --> Yes
I would request you to check the effective routes of the VM in Vnet B to see if you have a route to Office B? --> Yes n exist
should i have to create rules in vNet A to forward traffic to subnet in vnet B ? or by default the forward is enabled
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-06T13:58:06.137+00:00 Hello @APTOS ,
Thank you for the details.
No, you don't need any other rules.
Could you please re-check the configuration again?
1) Local network gateways on both Vnet sides (Vnet A & Vnet B) as below:
- LNG of Vnet A should have address space for both Vnet B and on-prem office A
- LNG of Vnet B should have address space for Vnet A & on-prem Office A
VPN device of Office A has address space of both Vnet A and Vnet B.
2) Are there any UDRs on the gateway subnets of Vnet A or Vnet B?
Regards,
Gita -
APTOS 221 Reputation points
2023-01-06T14:21:20.5+00:00 yes i confirm this :
LNG of Vnet A should have address space for both Vnet B and on-prem office A
- LNG of Vnet B should have address space for Vnet A & on-prem Office A
- VPN device of Office A has address space
Are there any UDRs on the gateway subnets of Vnet A or Vnet B? no there is no route tables
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-06T14:51:56.967+00:00 Hello @APTOS ,
Could you please try to do a IP flow verify test using Azure Network watcher between the local machine (VM in Vnet B) and remote machine (machine in on-prem Office A) to see if access is allowed?
To check IP flow verify on the VM of Vnet B from Office A:
- Go to Network Watcher.
- Click on IP flow verify tab.
- Choose your subscription, resource group, Virtual machine B & NIC (in case there are multiple nics). If the VM don't have multiple NICs, then NIC info will be auto-populated along with the local IP address.
- Protocol : TCP
- Direction : Inbound
- Local IP is the VM B IP (which should be auto-populated) and Local port = 3389
- Remote IP address = type the on-prem Office A IP address and remote port = 60000
- And click Check.
Screenshot for reference:
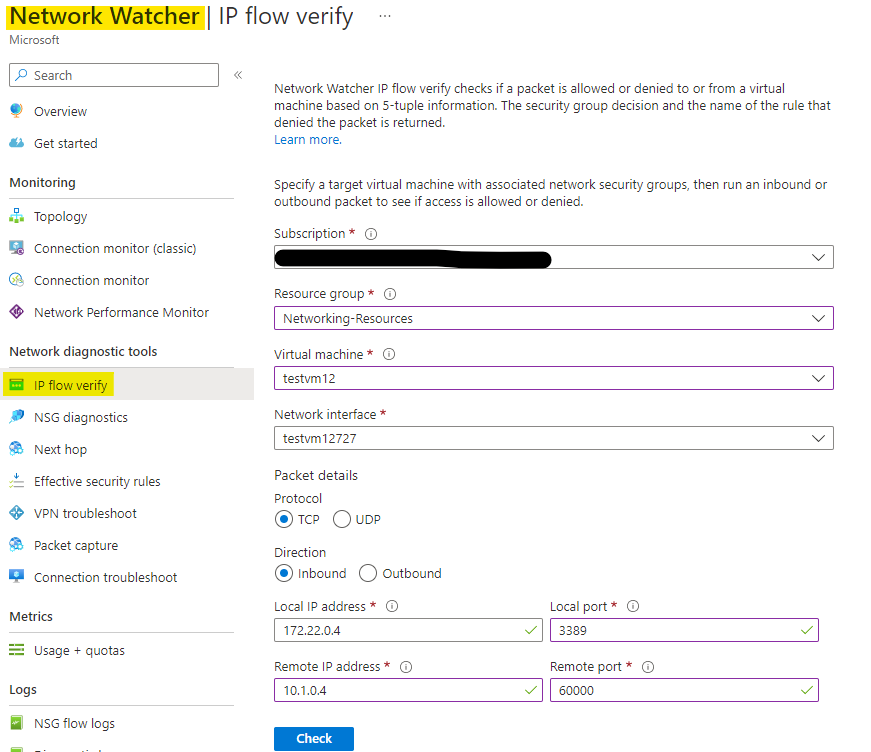
Regards,
Gita -
APTOS 221 Reputation points
2023-01-06T15:58:24.693+00:00 i checked and is allowed
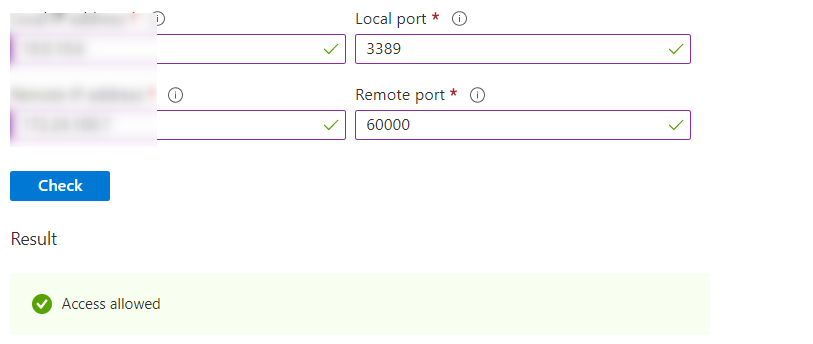
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-09T16:20:55.423+00:00 Hello @APTOS ,
Apologies for the delay in response.
It looks like everything is allowed on Azure end and the traffic should reach the VM B from Office A.
But since this is not happening, I suspect some issue with the on-prem VPN firewall device.
It would better to do a packet capture on your on-prem A VPN device while performing a continuous ping from a machine in office A to VM B and check if the traffic is leaving your VPN device firewall or getting blocked for some reason.Regards,
Gita -
Bas Pruijn 946 Reputation points
2023-01-09T16:30:37.167+00:00 Even though this set-up probably will work, the big question remains: why use all these VPN connections when just a simple network peering would automatically solve your issues? Furthermore, network peering is far cheaper than setting up VPN connections, has better performance and (with al the custom routing) is far more easy to maintain.
So, even though I like a technical challenge, I doubt this is the best solution.
-
APTOS 221 Reputation points
2023-01-09T16:45:32.433+00:00 Hi ,
with peering , it's not working in my network topology ( i can use only one remote gateway for peered vnets )
Regards
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-10T15:55:04.177+00:00 Hello @APTOS ,
Could you please provide an update on this post?
Since the effective routes exists and the traffic is allowed on Azure, the RDP should work.
You also confirmed that you are able to reach office A from a VM in Vnet B.
So, the next step would be to collect packet captures on your on-prem VPN device and Azure VPN gateways, while performing a continuous ping from a machine in office A to VM B and check if the traffic is getting blocked anywhere. Refer : https://learn.microsoft.com/en-us/azure/vpn-gateway/packet-capture#start-packet-capture---portal
Regards, Gita
-
 GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee
GitaraniSharma-MSFT 47,416 Reputation points • Microsoft Employee2023-01-12T13:41:45.95+00:00 Hello @ali ali ,
Could you please provide an update on this post and share the current status of the issue?
Regards,
Gita
Sign in to comment