Hi
it seems a proxy or firewall issue that generated this error.
You can follow the link below to check if required URL still reachable:
Please don't forget to mark helpful reply as answer
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi There,
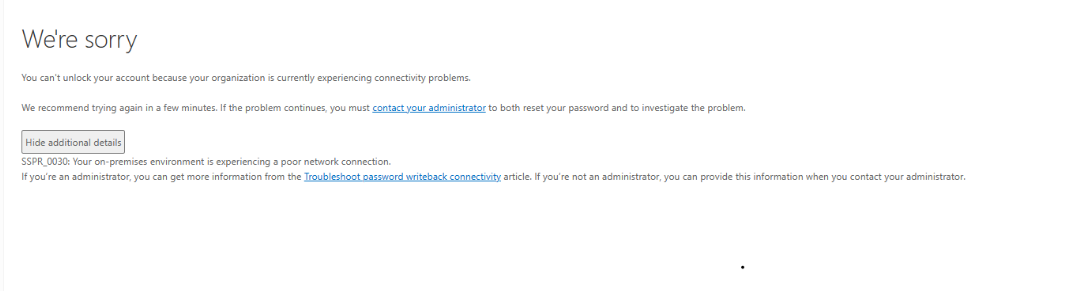
Our users are intermittently seeing the attached screenshot when resetting their password.
We have on-prem AD synchronising to Azure AD and can confirm password writeback is enabled.
A few months ago we did attempt to disabled TLS 1.2 on the on-prem AD server through here https://learn.microsoft.com/en-us/troubleshoot/azure/active-directory/enable-support-tls-environment?tabs=azure-monitor and here https://learn.microsoft.com/en-us/troubleshoot/azure/active-directory/enable-support-tls-environment?tabs=azure-monitor
After running these steps it was working very consistently until recently.
I found this site (https://learn.microsoft.com/en-us/azure/active-directory/authentication/troubleshoot-sspr-writeback) but cannot figure out where I am supposed to see these errors or where the logs are supposed to appear. Event viewer? Somewhere in Azure?
Can I get some assistance on this please?
Hi
it seems a proxy or firewall issue that generated this error.
You can follow the link below to check if required URL still reachable:
Please don't forget to mark helpful reply as answer
@Winston Tran Thank you for reaching out to us, add to the above steps
If the above suggestions, doesn't help to isolate the issue, we can connect offline for deeper investigation.
Please remember to "Accept Answer" if answer helped, so that others in the community facing similar issues can easily find the solution.
Hello,
Yes, the errors would appear in Azure. To retrieve them you need to follow the next steps:
1.Sign in to the Azure AD Connect server and start the Synchronization Service Manager by selecting Start > Synchronization Service.
2.Under the Connectors tab, select the on-premises Active Directory Domain Services connector, and then select Properties.
3.In the pop-up window, select Connect to Active Directory Forest and make note of the User name property. This property is the AD DS account used by Azure AD Connect to perform directory synchronization.
4.For Azure AD Connect to perform password writeback, the AD DS account must have reset password permission. You check the permissions on this user account in the following steps.
5.Sign in to an on-premises domain controller and start the Active Directory Users and Computers application.
6.Select View and make sure the Advanced Features option is enabled.
7.Look for the AD DS user account you want to verify. Right-click the account name and select Properties.
8.In the pop-up window, go to the Security tab and select Advanced.
9.In the Advanced Security Settings for Administrator pop-up window, go to the Effective Access tab.
10.Choose Select a user, select the AD DS account used by Azure AD Connect, and then select View effective access.
--If the reply is helpful, please Upvote and Accept as answer--