Hi,
I allow myself to come to you today because I would like to do a RAM analysis of a Windows machine via volatility from Linux. Knowing that the system resulting from the dump was infected I am looking for the anomaly via the RAM memory by Volatility.
So I took several actions.
First the analysis of the image via 'imageinfo' to retrieve the analysis profile. Then perform pslist and pstree to check running processes.
pstree
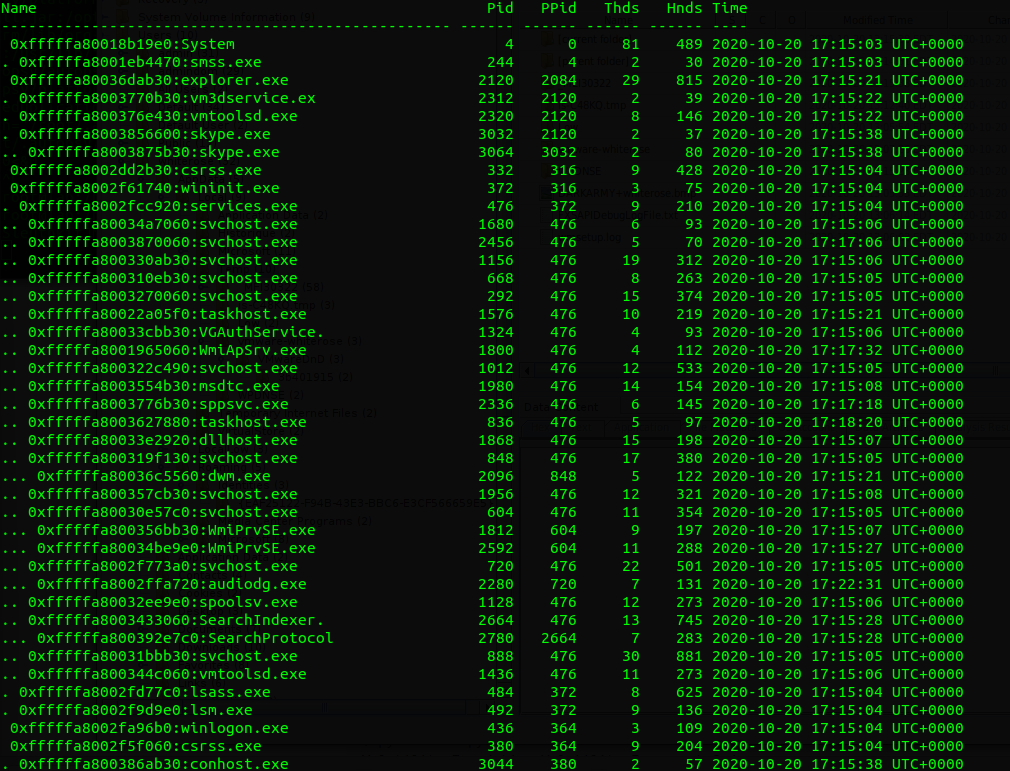
But nothing is very suspicious in my opinion. Or just maybe skype.exe with pid 3064.
I look at network connections from netscan command.
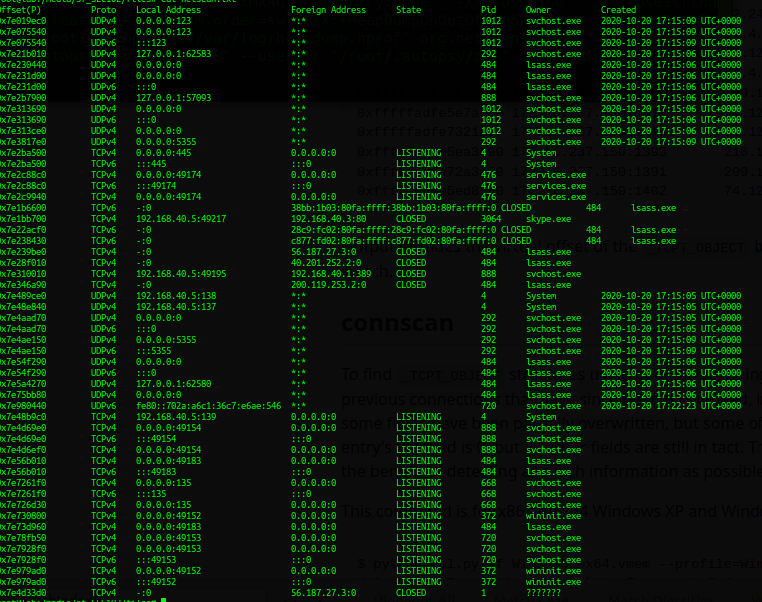
I see here that the skype.exe file has the status 'closed' and that it only points to local ip addresses.
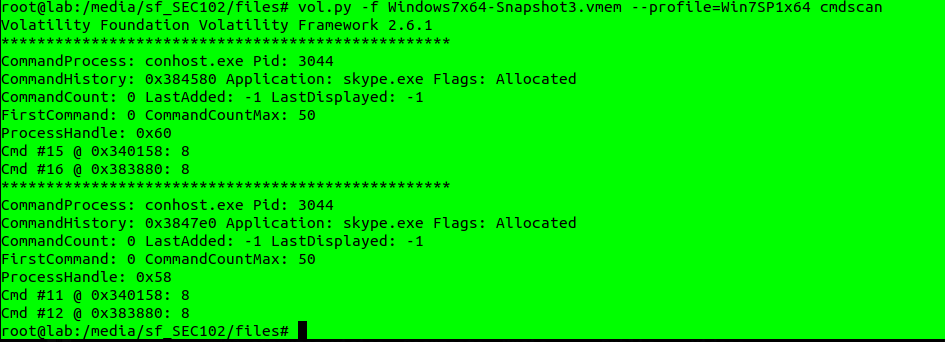
With the cmdline and cmdscan command, I see that the skype.exe file has been installed by the user, launches conhost.exe, but is this normal or not ?
**
dlllist**
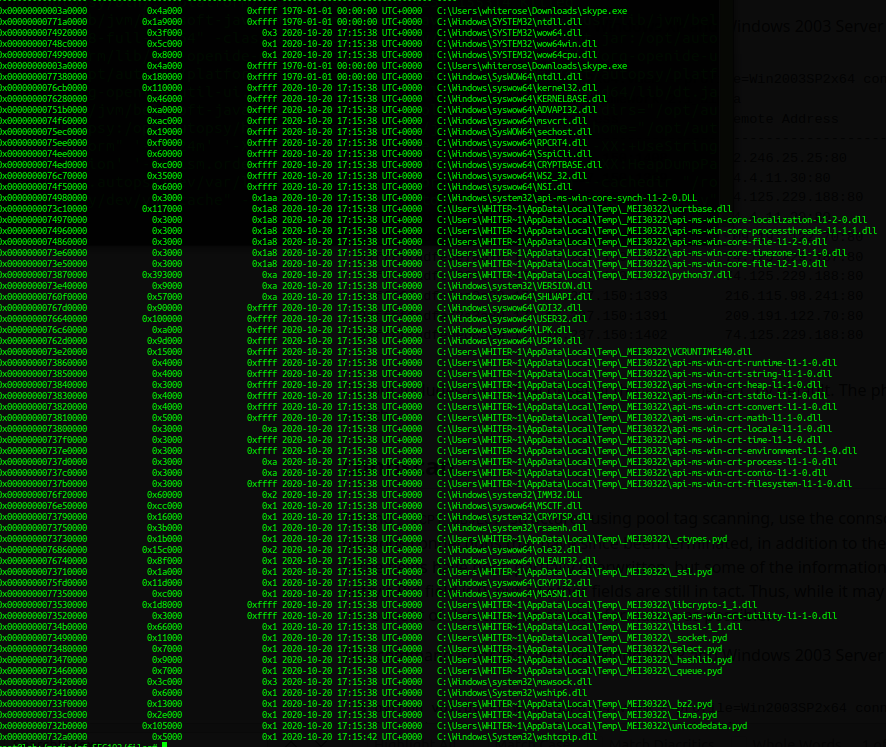
The malfind command give me just "explorer.exe" process, and "svchost"
I am a beginner in the field and would like to understand, and know what to be wary of knowing that here I know that the pc has been infected. The malfind
I thank you in advance for your attention and your more than precious feedback.
