@Robert D. Crane
Thank you for your post and I apologize for the delayed response!
Error Message:
Caller is missing required playbook triggering permissions on playbook resource '/subscriptions/..../resourceGroups/.../providers/Microsoft.Logic/workflows/...', or Microsoft Sentinel is missing required permissions to verify the caller has permissions.
From your issue, I understand that you created a custom Sentinel Playbook and when trying to manually run your Playbook through the Sentinel Incident, you're receiving the error message above.
I reproduced your issue and will share some troubleshooting steps below to hopefully point you in the right direction.
Note: If you're still having issues, please feel free to reach out to myself or Givary using the azcommunity email
Findings: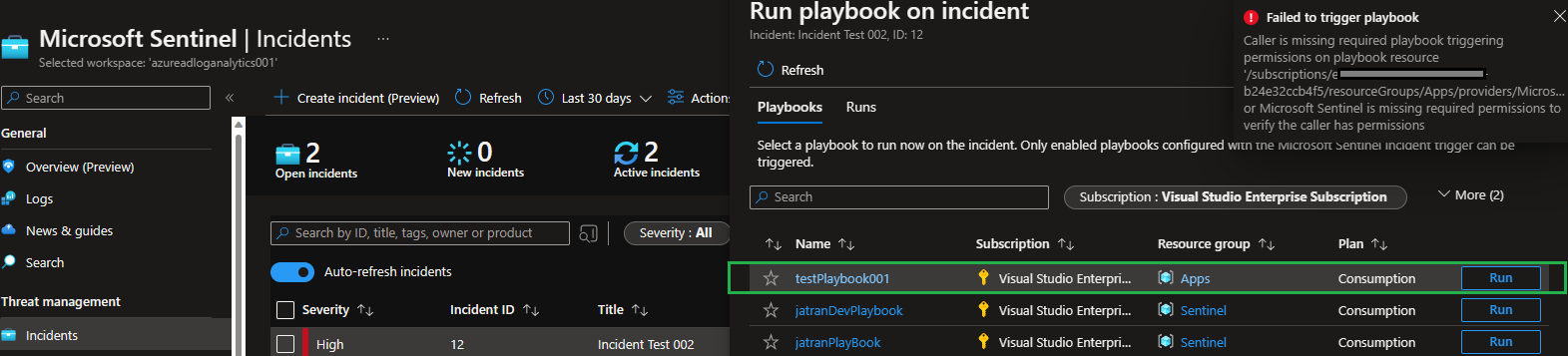
From your previous comments, I understand that you added your Resource Group (mms-seau) to the Sentinel Playbook Permissions Setting, and also confirmed the Microsoft Sentinel Responder role assignment was inherited.
Troubleshooting:
From your error, this still looks like a Permissions issue, so can you confirm the following:
- From your Resource Group (
mms-seau), Select Access Control (IAM), confirm your resource group has the Microsoft Sentinel Automation Contributor role assigned to Azure Security Insights. Additionally, make sure that your user has the Logic App Contributor and Owner role assigned.
- Note: You yourself must have Owner permissions on any resource group to which you want to grant Microsoft Sentinel permissions, and you must have the Logic App Contributor role on any resource group containing playbooks you want to run.
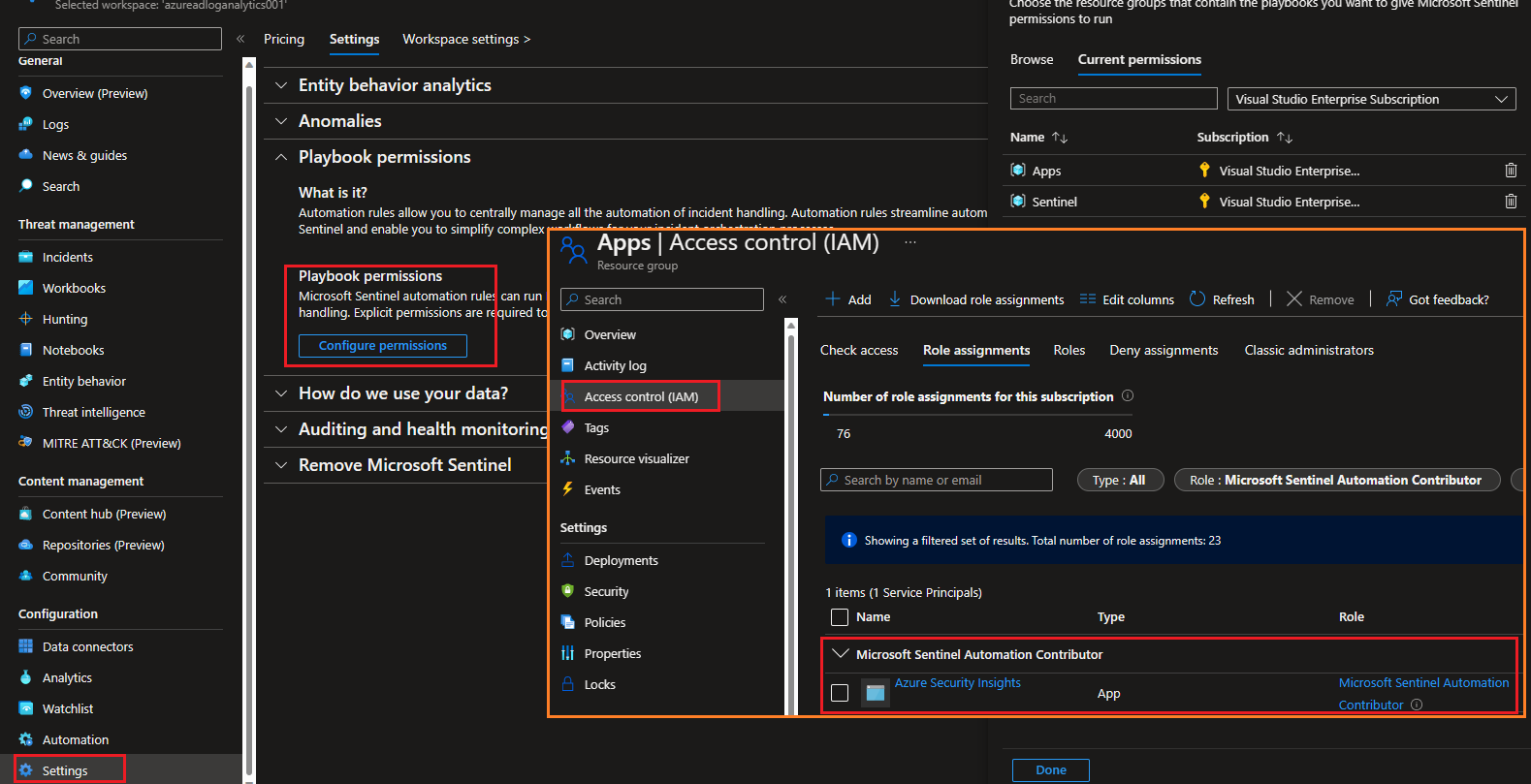
To run a playbook based on the incident trigger, whether manually or from an automation rule, Microsoft Sentinel uses a service account specifically authorized to do so. This account must be granted explicit permissions (taking the form of the Microsoft Sentinel Automation Contributor role) on the resource group where the playbook resides.
- If your Resource Group has the correct permissions, we can try to see if there are any issues when creating a Test Automation rule. If a playbook appears "grayed out" in the drop-down list, it means Sentinel doesn't have permission to that playbook's resource group. To resolve the issue, you'll have to click the Manage playbook permissions link to assign permissions.
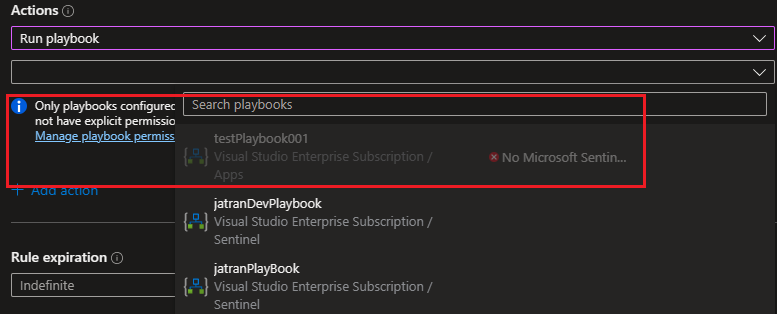
I hope this helps!
If you're still having issue, please let us know and we'd be happy to continue working with you on this issue. Thank you for your time and patience throughout this issue.


