I am trying to fetch files from Sharepoint location and load it in Azure Sql Database using ADF. I am trying to use Graog API site.Selected and Managed Identity permission to create the authentication.
I am trying to avoid the ACL approach where we have to generate Bearer token to establish connection. I am able to load data using this approach.
I am following this blog https://pivotalbi.com/copy-files-from-sharepoint-online-using-azure-data-factory-and-the-microsoft-graph-api/
The challenge I am facing is: while trying to give read access to SharePoint Online via the Graph API getting error
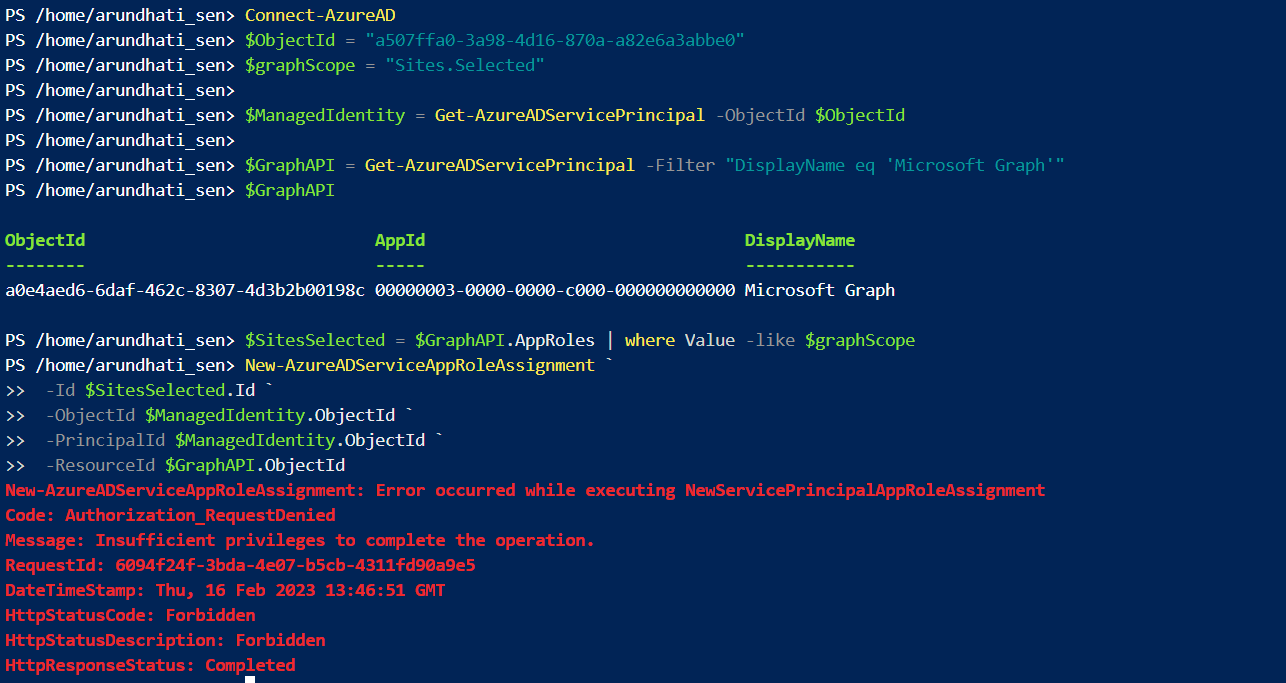
powershell code executed:
Connect-AzureAD
$ObjectId = "a507ffa0-3a98-4d16-870a-a82e6a3abbe0"
$graphScope = "Sites.Selected"
$ManagedIdentity = Get-AzureADServicePrincipal -ObjectId $ObjectId
$GraphAPI = Get-AzureADServicePrincipal -Filter "DisplayName eq 'Microsoft Graph'"
$GraphAPI
$SitesSelected = $GraphAPI.AppRoles | where Value -like $graphScope
New-AzureADServiceAppRoleAssignment `
-Id $SitesSelected.Id `
-ObjectId $ManagedIdentity.ObjectId `
-PrincipalId $ManagedIdentity.ObjectId `
-ResourceId $GraphAPI.ObjectId
Error :
Error occurred while executing NewServicePrincipalAppRoleAssignment
Code: Authorization_RequestDenied
Message: Insufficient privileges to complete the operation.
HttpStatusCode: Forbidden
HttpStatusDescription: Forbidden
HttpResponseStatus: Completed
I am not sure how to solve this, Please help. There is no option to provide any permission at the Managed Identity Level as well.
@RaytheonXie_MSFT

