Hi, Community. I have a Problem with Conditional Access.
The organization has devices that Azure Ad Joined and complianed. However, users use not Azure AD account to enter the system, but use local accounts. There are also terminal servers that Hybrid Joined in Azure AD. Users use domain accoutns for logon.
The problem is that I need to create Compliance Policy. Which allows not require second factor for such devices (AD joined and hybrid), but requires second factor or even block access from devices that are not complianed or not Azure Joined.
It shouldn't be difficult. For example, such a policy.
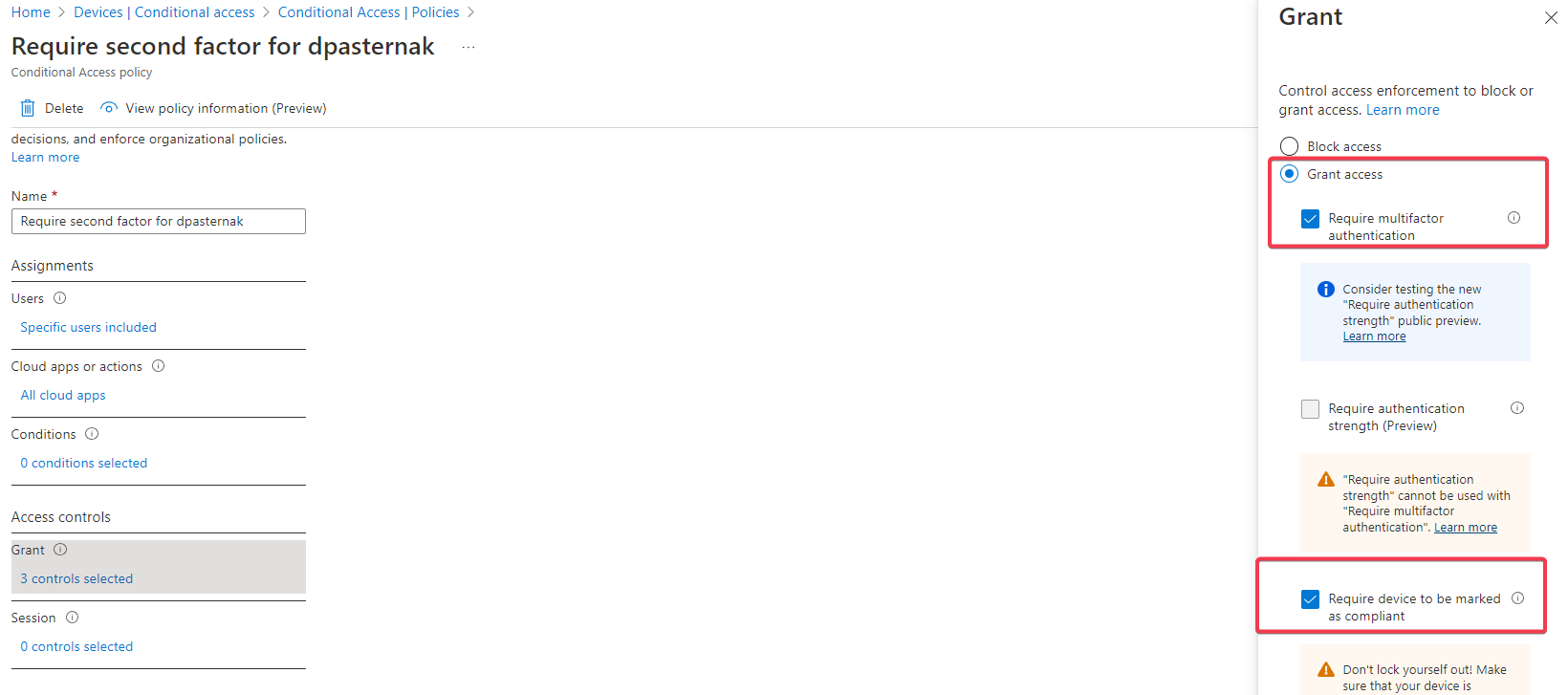
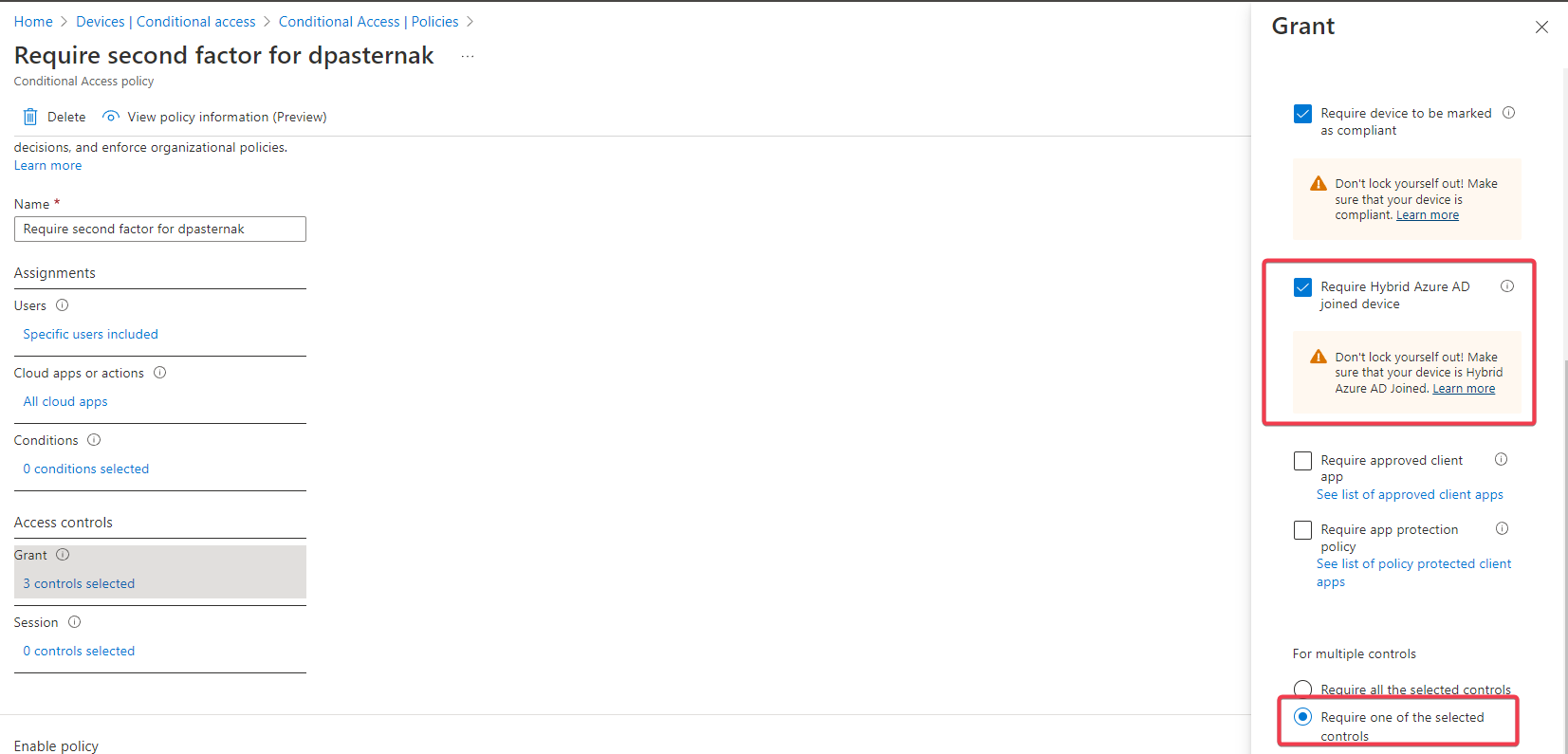
But it seems that the device will not be recognized as compliance or Azure Joined if the user logon with local account and opens OneDrive or SharePoint using Azure account. Because in this case, the second factor will be required. But as soon as I enter the system using Azure AD account. The second factor is not required and I can open application without a password and 2FA (only during logon ask setup PIN and require 2FA, but it can be skiped).
I tried to create a block policy. In order to understand how politics is recognizes the type of device. This policy is triggered for all devices if I use a local account and open office.com using Azure account.
Access to applications is rejected. But if I enter the device with Azure Ad account, I can open the applications.
- The rule explicitly blocks access for the user. From any location, from any device. It works.
- In this rule, I add an exception location, namely the IP address of the machine from which I open office.com.
It works.
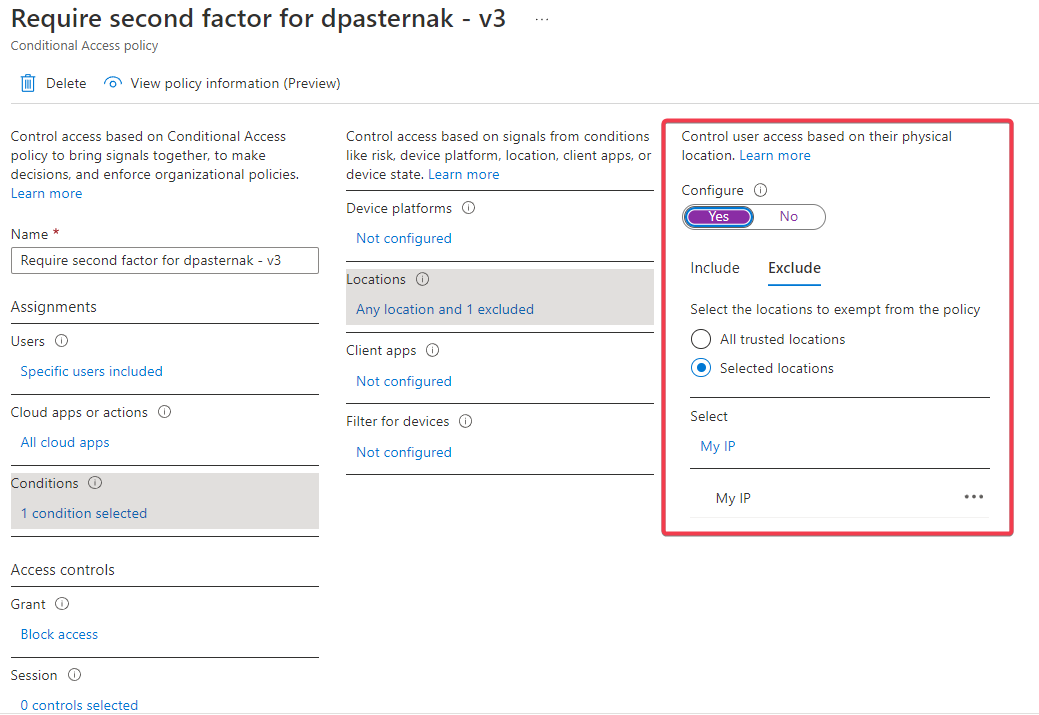
- In this rule, I remove the location condition. And I exlude device AD joined from this rule. This does not work. While the device is AD Joined.
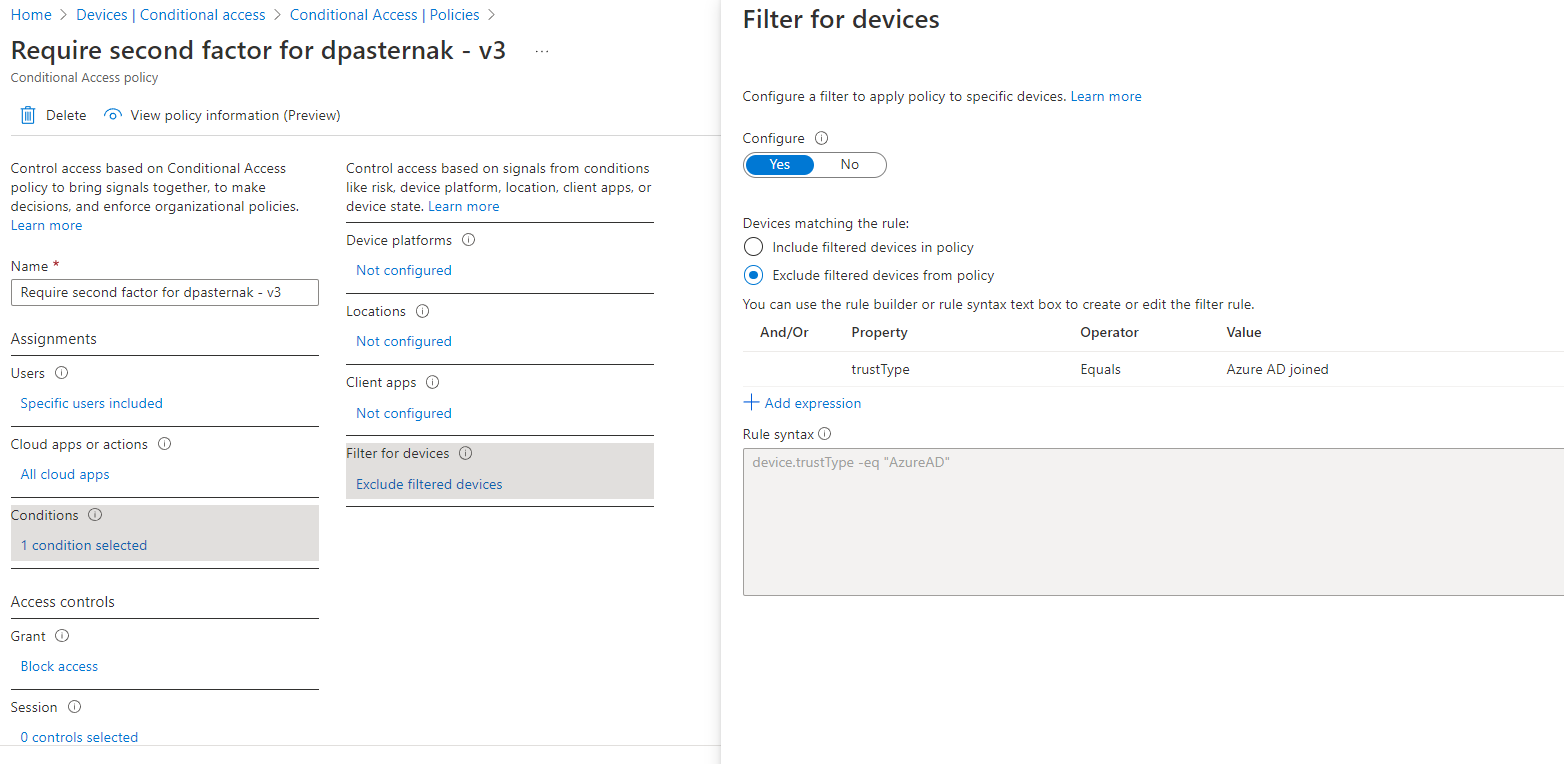
- I am logon on this device with Azure account (for which the rule applies) and can open office.com. Works only if I logon using AD account.
In general, the problem is that the user must be included in the system with Azure Ad Account, so that the rule would work?
Thank you.
