Feb 1: User's account was checked in Active Directory to "User must change password at next logon".
Every day since then the user had the following entry in Sign-Ins in AAD
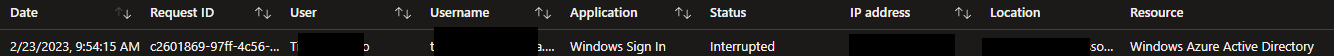

AND
The user's password is expired, and therefore their login or session was ended. They will be offered the opportunity to reset it, or may ask an admin to reset it via
- User was still able to get into Outlook and send emails, use SSO'd apps etc. User has MFA enforced on the account, etc.
- The laptop is an Azure AD Joined machine provisioned by Auto Pilot just like any other device.
There's no foul play here, I just can't wrap my head around how besides using Windows Hello for Business to get into her laptop that she was still able to access email, and other SSO'd apps without ever authenticating again. She sent multiple emails yesterday no issue. Yet I don't even see a login INTO Office or anything for yesterday for her. I don't even see the Windows Sign In entry for yesterday at all and due to CA policies that I know for a fact work, she couldn't use email from any other device besides this one.
As we speak I took a test computer with a test user identical to this user and when I log into it with Windows Hello, I have yet to get the Windows Sign In entry. Not to mention I flipped the user in AD to the same "Usesr must change password at next logon"
We have writeback and SSPR and it works.
Does Windows Hello for Business just extend the authentication token thus allowing the end user to continue to access Office and other SSO'd apps? Could this person in theory have just kept on keeping on this way indefinitely or in 30 days from Feb 1 would it finally of come to a halt?


