We want to add graph api application permission the Azure AD application and grant API permissions to a client app in Azure Active Directory (Azure AD) programmatic alternative to interactive consent .
Three steps :
First Step:
Create Azure AD application using graph API and it working.
var accessTokenProvider = new BaseBearerTokenAuthenticationProvider(new TokenProvider());
var graphServiceClient = new GraphServiceClient(accessTokenProvider);
var requestBody = new Application
{
DisplayName = "05N",
Description="This app is created from Graph API"
};
var result = await graphServiceClient.Applications.PostAsync(requestBody);
Second Step:
Add API permission into application and it is also working:
var accessTokenProvider = new BaseBearerTokenAuthenticationProvider(new TokenProvider());
var graphServiceClient = new GraphServiceClient(accessTokenProvider);
var requestBody = new Application
{
RequiredResourceAccess = new List<RequiredResourceAccess>
{
new RequiredResourceAccess
{
// Resource Graph API id
ResourceAppId = "00000003-0000-0000-c000-000000000000",
ResourceAccess = new List<ResourceAccess>
{
new ResourceAccess
{
// Permission User.ReadWrite.All : get this Id from Manifest file by adding permission manually and then delete it manually
// then add it by code.
Id = Guid.Parse("741f803b-c850-494e-b5df-cde7c675a1ca"),
Type = "Role" // for application permission : for delegate use scope
},
new ResourceAccess
{
// Permission Tasks.ReadWrite.All : get this Id from Manifest file by adding permission manually and then delete it manually
// then add it by code.
Id = Guid.Parse("44e666d1-d276-445b-a5fc-8815eeb81d55"),
Type = "Role" // for application permission : for delegate use scope
},
new ResourceAccess
{
// Permission MailboxSettings.ReadWrite : get this Id from Manifest file by adding permission manually and then delete it manually
// then add it by code.
Id = Guid.Parse("6931bccd-447a-43d1-b442-00a195474933"),
Type = "Role" // for application permission : for delegate use scope
}
}
}
}
};
// ApplicationId = Object Id of application where permissions added
var result = await graphServiceClient.Applications["e8e65922-4406-4d46-ad97-64efae478972"].PatchAsync(requestBody);
Third Step:
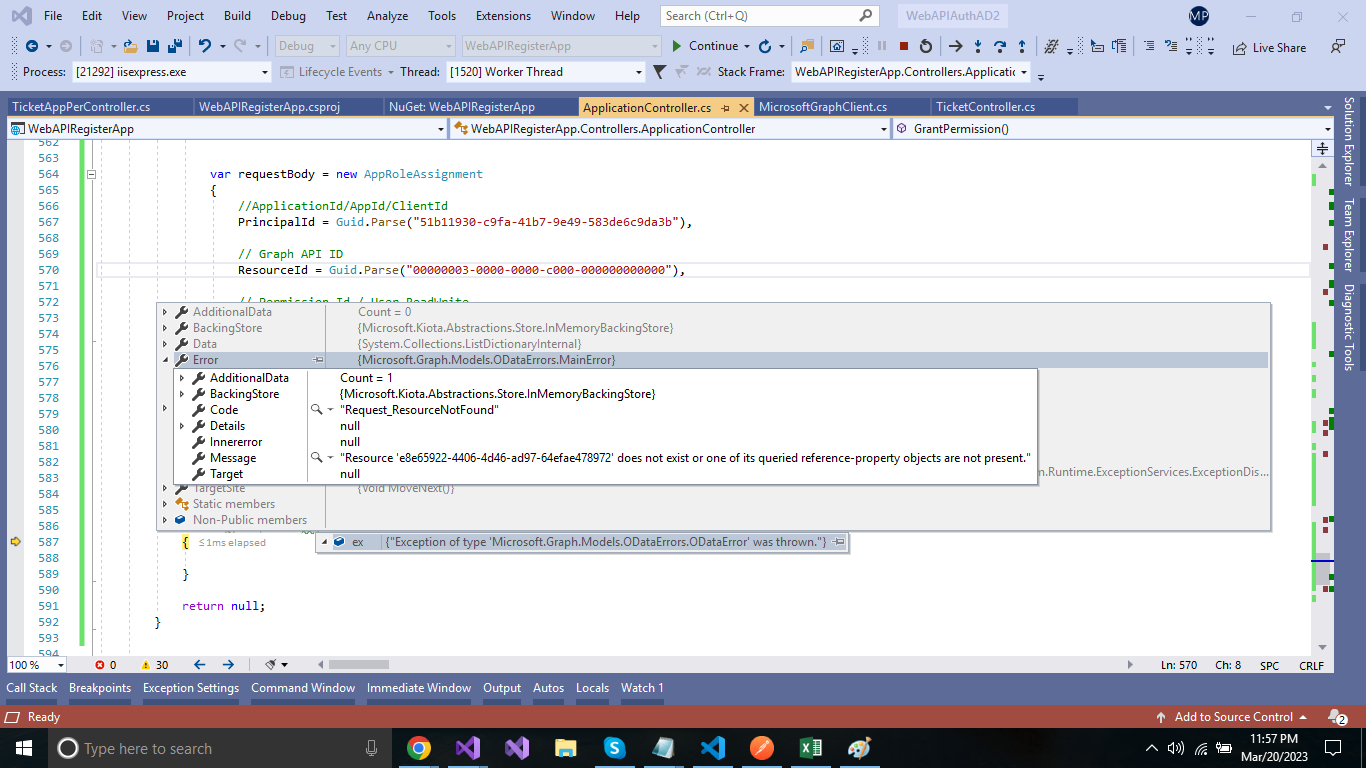
Grant permission: It is not working, the exception is throwing: Am I missing something over step 3,
var requestBody = new AppRoleAssignment
{
//ApplicationId/AppId/ClientId
PrincipalId = Guid.Parse("51b11930-c9fa-41b7-9e49-583de6c9da3b"),
// Graph API ID
ResourceId = Guid.Parse("00000003-0000-0000-c000-000000000000"),
// Permission Id / User.ReadWrite
AppRoleId = Guid.Parse("741f803b-c850-494e-b5df-cde7c675a1ca"),
};
//servicePrincipal-id - ObjectId of the application where permission needs to grant.
var result = await graphServiceClient.ServicePrincipals["e8e65922-4406-4d46-ad97-64efae478972"].AppRoleAssignedTo.PostAsync(requestBody);
exception: