Hello, @Sachithya Gamage !
Why am I having connectivity issues with my ingress controller after an upgrade?
I reached out to an AKS specialist and am confirming what @Manu Philip has said and wanted to add a bit more information from the release notes:
https://github.com/Azure/AKS/blob/master/CHANGELOG.md#release-notes-1
Behavioral Changes
For Kubernetes 1.24+ the services of type LoadBalancer with appProtocol HTTP/HTTPS will switch to use HTTP/HTTPS as health probe protocol (while before v1.24.0 it uses TCP). And / will be used as the default health probe request path. If your service doesn’t respond 200 for /, please ensure you're setting the service annotation service.beta.kubernetes.io/port_{port}_health-probe_request-path or service.beta.kubernetes.io/azure-load-balancer-health-probe-request-path (applies to all ports) with the correct request path to avoid service breakage.
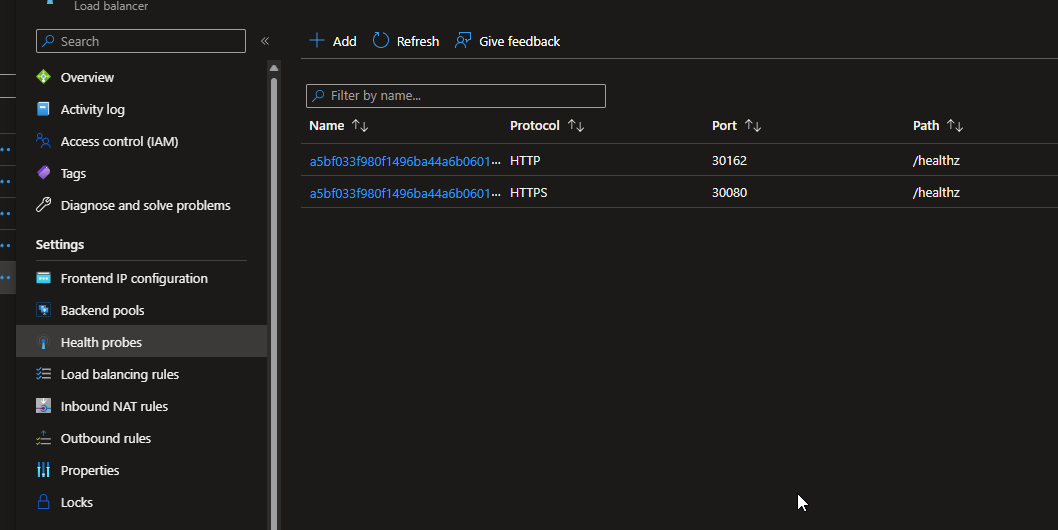
The most common scenario with the nginx ingress controller is where the default path for the probe is /healthz. As you can see from the release notes, prior to the upgrade the health probe would be using TCP so you wouldn't run into the issue. After the upgrade, the health probe would start using HTTP/s on the / path which would cause it to fail.
To resolve this issue, you would add the following annotation to the affected load balancer service to point it to the correct path:
service.beta.kubernetes.io/azure-load-balancer-health-probe-request-path: "/healthz"
You can also see this in the portal:
Before:
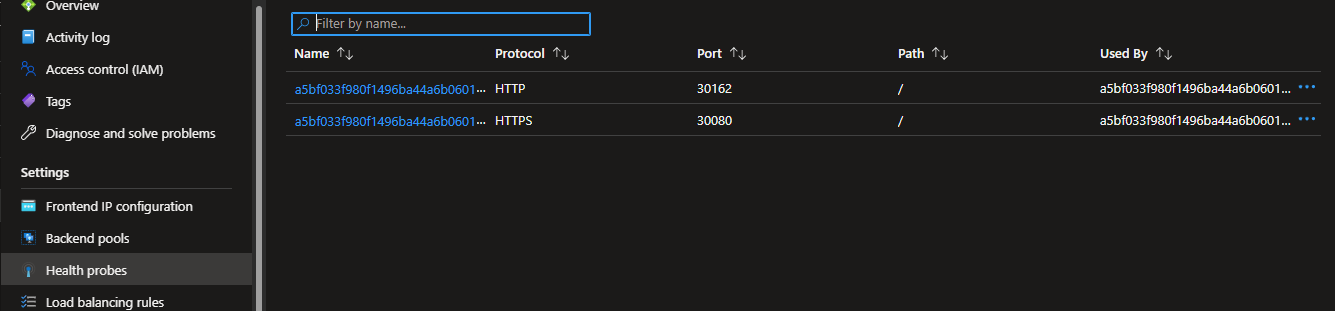
After: