Hi,
I've discovered Windows 10 sends unauthenticated SMB requests to my server and this causes logs to be written on either sides.
According to this article, Windows 10 should not send unauthenticated (GUEST) requests, but it happens.
To my understanding, these calls are done when the system is performing some actions on my behalf. I've identified:
- Antivirus (Avira) scanning for network paths while I am browsing them
- Windows File History when accessing and backing up files.
I can use my file shares without issues, but there are a ton of logs that are reported either sides and that's very annoying.
Windows Side:
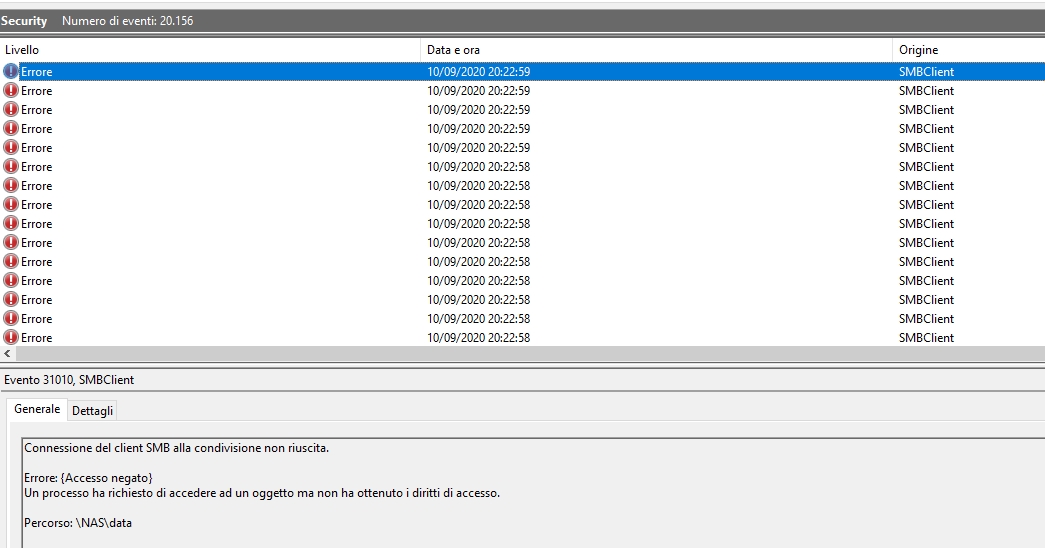
Windows Event Viewer logs errors under SMB-Client.
The error says:
Error: {Access Denied}
A process has requested access to an object, but has not been granted those access rights.
Path: \nas\data
Error code: 31010
Samba Side
Samba side, verbose logging
Mapping user []\[] from workstation
attempting to make a user_info for ()
made a user_info for ()
check_ntlm_password: Checking password for unmapped user []\[]@[PC-OLIVER] with the new password interface
check_ntlm_password: mapped user is: []\[]@[PC-OLIVER]
auth_check_ntlm_password: anonymous authentication for user [] succeeded
Auth: [SMB2,(null)] user []\[] at [Thu, 10 Sep 2020 19:47:59.018110 CEST] with [(null)] status [NT_STATUS_OK] workstation [PC-OLIVER] remote host [ipv4:192.168.0.100:49239] became [NAS]\[nobody] [S-1-5-21-1308971618-3954224730-4125826118-501]. local host [ipv4:192.168.0.101:445]
check_ntlm_password: guest authentication for user [] -> [] -> [nobody] succeeded
Successful AuthZ: [SMB2,NTLMSSP] user [NT AUTHORITY]\[ANONYMOUS LOGON] [S-1-5-7] at [Thu, 10 Sep 2020 19:47:59.018445 CEST] Remote host [ipv4:192.168.0.100:49239] local host [ipv4:192.168.0.101:445]
Non verbose logging
create_connection_session_info: guest user (from session setup) not permitted to access this share (data)
create_connection_session_info failed: NT_STATUS_ACCESS_DENIED
I also turned on Wireshark and confirmed that my PC is indeed sending empty AuthN requests:
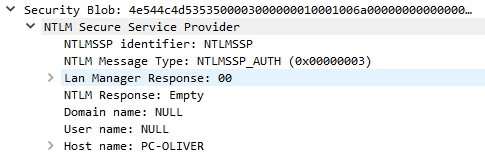
I tried to edit settings that are already enabled by default and should not allow anonymous requests over the network.
secpol.msc > local policies > security options:
- Network access: do not allow anonymous enumeration of SAM accounts: ENABLED
- Network access: do not allow anonymous enumeration of SAM accounts and shares: ENABLED
I also tried deleting credentials from Credential Manager, removing all shares with the command
net use */Delete
and then using something like
net use z: \\servername\path /USER:username
Additional details:
I've replicated this issue using Windows 10 2004 and 1903 fresh installs with two Samba servers: an existing one and another configured from scratch just for this scenario.
- Server: Linux, Debian 10, Samba 4.9.5
- Client: Windows 10 2004
When accessing the share for the first time I am prompted from credentials and I enable the option to save them in Credentials Manager.


