Of course you do, they're simply packaged as Access Control Policies: https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/operations/access-control-policies-in-ad-fs
ADFS 2019 allow sign in from specific IP for specific users
Hi,
We have an ADFS 2019 and ADFS 2019 Proxy servers to have SSO with Office 365.
For a specific group in our AD we only want to allow the signin from a specific IP or a computer that is joined in our domain.
All other users can sign in from everywhere.
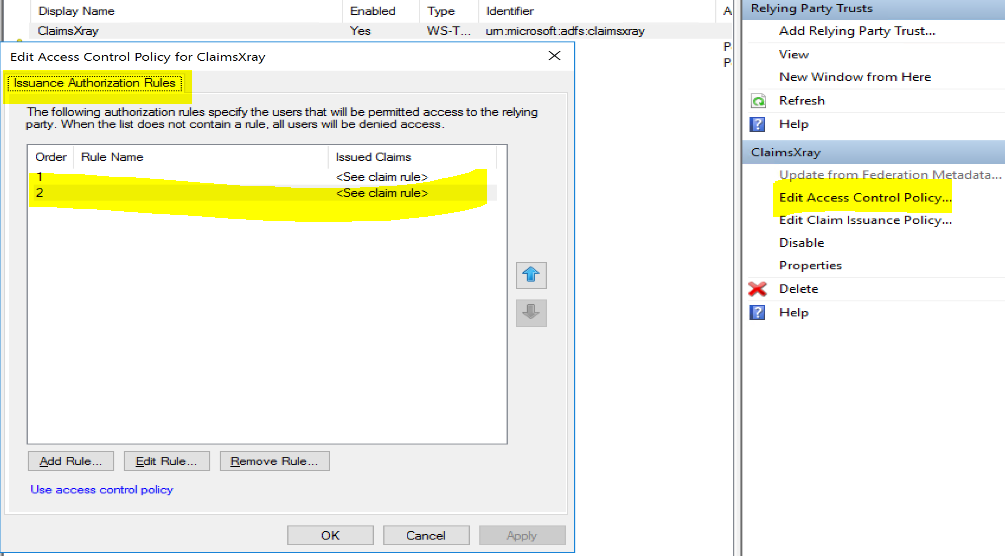
When I search on internet I can only find documentation about ADFS 2012 and I need to create Issuance Authorization Rules.
But in ADFS 2019 I don't have Issuance Authorization Rules.
How can I achieve my goal?
2 answers
Sort by: Most helpful
-
-
 Pierre Audonnet - MSFT 10,166 Reputation points Microsoft Employee
Pierre Audonnet - MSFT 10,166 Reputation points Microsoft Employee2020-10-15T00:22:55.93+00:00 Like @Vasil Michev says you can use Access Control Policies.
Let say you want to allow all users but if the user is a member of the group TESTG then you allow the connection only if the IP is 1.2.3.4. You will have the following policy:
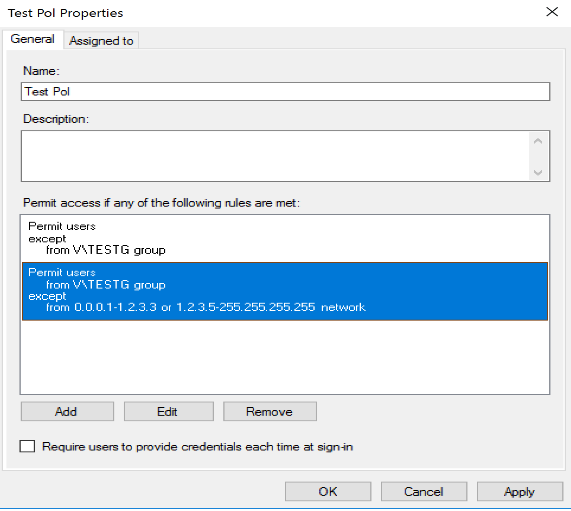
The first part allow all users as long as they are not member of the group.
If they are member of the group then we allow them as long as the IP is not between 0.0.0.0 and 1.2.3.3 and not between 1.2.3.6 and 255.255.255.255. In other word we allow only if the if IP is 1.2.3.4.Also, you can still use the "old school" issuance authorization rules in Windows Server 2019 ADFS. To do so, set the policy of your relying party to $null, example:
Set-AdfsRelyingPartyTrust -TargetName ClaimsXray -AccessControlPolicyName:$nullThen check the GUI and you'll see your policy has been converted into an old school one :)