Hello all,
I need some help here!
I'm now in charge of the PKI in my society and it was in a mess since years. I sucessfully changed the OCSP server, and now created a Windows 2022 CRL server to replace the old 2012. I also have 3 others Severs, 1 ROOTCA and 2 subordinate CA.
I followed this microsoft link to configure CDP and AIA on my 3 CA : https://learn.microsoft.com/en-us/windows-server/networking/core-network-guide/cncg/server-certs/configure-the-cdp-and-aia-extensions-on-ca1 (So Only with http:// and file:// values).
Then on each republish a crl and copy them to the new CRL server:
certutil –crl
copy C:\Windows\system32\certsrv\certenroll.crt mycrlserver.fr\crlpki
copy C:\Windows\system32\certsrv\certenroll.crl mycrlserver.fr\crlpki
I also restarted certsvc. I requested a new cert, revoked it, republished, recopy, verified his crl access, dowloaded it, everything is working fine with the new server.
By the way here is my time configuration on the 3 CA :
Certutil -setreg CACRLPeriod Days
Certutil -setreg CACRLPeriodUnits 1
Certutil -setreg CACRLDeltaPeriod Hours
Certutil -setreg CACRLDeltaPeriodUnits 1
My only problem is on PKIView.msc, on ROOT I still see the old values of the old AIA and CDP location and the new value. (In Yellow what should be removed)
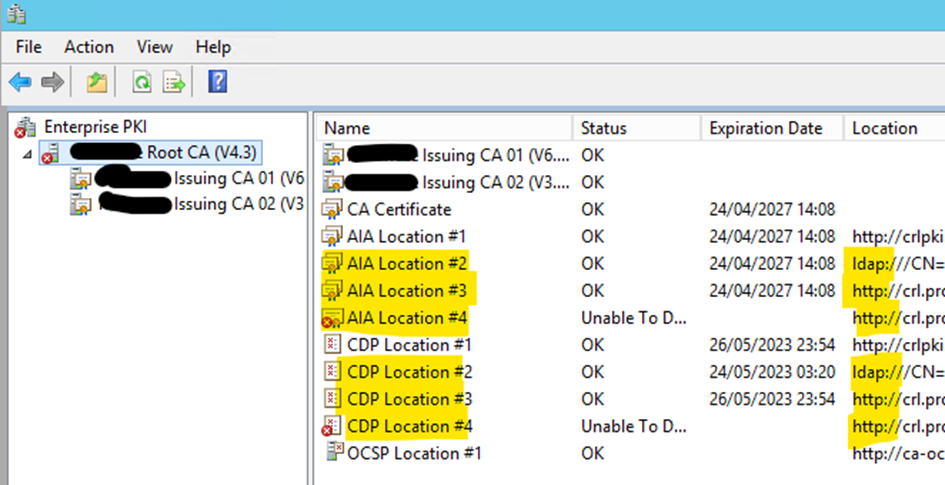
If I develop root and check the subordinate CA, they only show the new values.
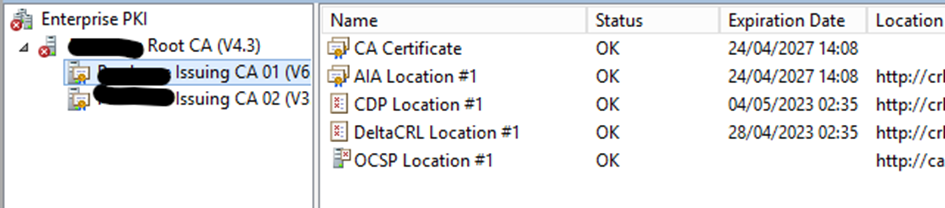
I reverified the extensions tab of the CA properties on each of my 3 CA servers and there is only the new values on CRL and AIA configuration.
I spent a lot of time on internet to find a solution to clean these old values from Root on Pkiview without success.
Here is what I already tried :
Revoke the CA Exchange on the 3 CA and verify there is only the right locations inside (before i did this step they had the wrong values).
Republish my crl (and copy them to the CRL Server) restart certsvc. I verified on each CA certutil -getreg ca\crlpublicationurls and it shows the right informations.
I renewed the issuing ca certificate on my 2 subordinate CA (Renewed with same key), Now I could see only the new values.
I forced an AD réplication.
On Active directory site and service, show service node, Services, Public Key Services I verified all the folders permissions (I can't find back the link bur I copied it for myself)
Enrollment Services container. The CA computer has Read and Write access to its own object.
AIA container. The Cert Publishers group has Full Control access on the AIA container and the CA computer has Full Control access on its own object within the AIA container.
CDP container. The Cert Publishers group has Full Control access on every CA's container under the CDP container, and the CA computer has Full Control access on every certification revocation list (CRL) object in its own container.
Certification Authorities container. The Cert Publishers group has Full Control access on the objects within this ontainer.
C__ertificate Templates container__. The Enterprise Admins and Domain Admins groups (not the CA computer) have Full Control access or Read and Write access to this container and to most objects within it.
KRA container. The CA computer has Full Control access on its own object.
OID container. The Enterprise Admins and Domain Admins groups, not the CA computer, have Full Control access or Read and Write access to this container and to the containers and objects within it.
NTAuthCertificates object. The Enterprise Admins and Domain Admins groups, not the CA computer, have Full Control access or Read and Write access.
Domain Computers and Domain Users containers. The Cert Publishers group has Read and Write permissions on the userCertificate property of each user and computer object in the forest in which AD CS is deployed.
All seems fine!
I also tested the connexion from ROOTCA nltest /sc_verify:mydomain.fr
Answer : Flags: b0 HAS_IP HAS_TIMESERV
Trusted DC Name MyDC.mydomain.fr
Trusted DC Connection Status Status = 0 0x0
NERR_Success
Trust Verification Status = 0 0x0
NERR_Success
The command completed successfully
Also on cmd Admin :
Export ROOTCA cert :
certutil -ca.cert ROOTCA.cer
certutil -ca.cert ISSUING01.cer
certutil -ca.cert ISSUING02.cer
Publish ROOTCA cert in AD :
certutil -f -dspublish ROOTCA.cer RootCA
certutil -f -dspublish ISSUING01.cer SubCA
certutil -f -dspublish ISSUING02.cer SubCA
Nothing Helps!
PLease, have you got any idea to help me to clean this?
Regards,
