
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi all,
A couple years ago I setup a PKI with an offline root, enterprise CA, and a web-based NDES server all on Server 2016. We're using it for device authentication on our Wi-Fi.
Mac clients use SCEP and connect with the web-based NDES server. There is a Digicert SSL on this server. I believe that was part of the instructions on the guide I used to set this up. I use my MDM (Jamf) to deploy this to MacOS and iOS. This is working.
For my Windows clients I use Active Directory to first install the root certificate and then request a certificate on the enterprise CA. This was working until recently the Digicert SSL was renewed and installed on the web-based NDES server. Ever since then, everything is working except Windows clients getting new certificates from the enterprise CA.
Here's the messages I get on the Enterprise CA:
Event 22, CertificationAuthority
Active Directory Certificate Services could not process request 1265 due to an error: Cannot archive private key. The certification authority could not verify one or more key recovery certificates. 0x8009400b (-2146877429 CERTSRV_E_NO_VALID_KRA). The request was for OES\DELLLAT13-708$. Additional information: Error Archiving Private Key
Here's the messages I get on the Windows 10 client:
Event 13, CertificateServicesClient-CertEnroll
Certificate enrollment for Local system failed to enroll for a OESWorkstationAuthentication certificate with request ID N/A from entca.oes.edu\OES Enterprise Certificate Authority (Cannot archive private key. The certification authority could not verify one or more key recovery certificates. 0x8009400b (-2146877429 CERTSRV_E_NO_VALID_KRA)).
Event 6, CertificateServicesClient-AutoEnrollment
Automatic certificate enrollment for local system failed (0x8009400b) Cannot archive private key. The certification authority could not verify one or more key recovery certificates.
Can someone help me troubleshoot this?

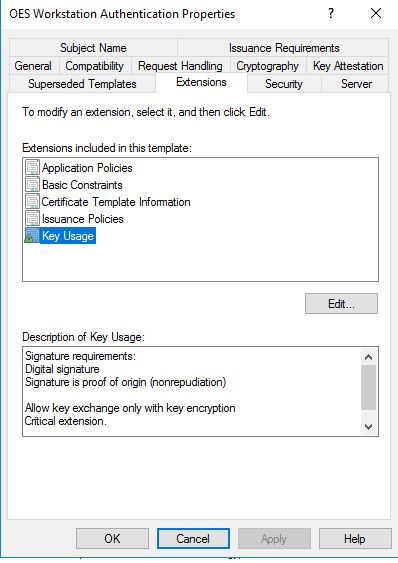
Your template is configured for client private key archival in CA database (not sure for what reason) and all Key Recovery Agent certificates are expired.
You have two options:
Thanks for the reply.
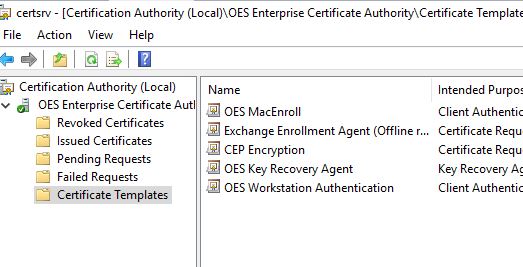
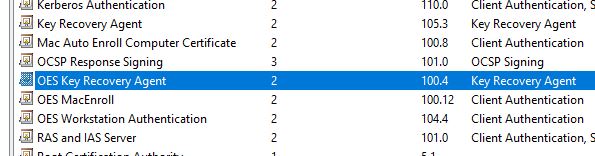
So I've tried on two new computers. It's still not working, but the error is different. Now what is happening is Event viewer doesn't log anything. Nothing on the CA and nothing on the client. No request or failed request logged on the CA at all. On the client, it is getting the network profile from AD now. But no certificate.
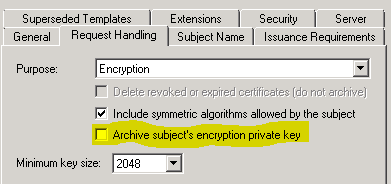
I made a little progress. I found that if I check the box that you had checked, "Include symmetric algorithms allowed by the subject" then the client is now able to get a certificate. But now it's being rejected by the Radius server. I now get this error.
RADIUS EAP-TLS: fatal alert by server - unsupported_certificate
TLS Handshake failed in SSL_read with error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed
eap-tls: Error in establishing TLS session