Hello @Chindanur Channakesa !
So it is On Premises Jira
Do me a favor and verify that the Application is working correct when you try to login to the On Premises URL from the VM that hosts the Application Proxy Connector
Are you using a Custom Domain ? Remember with Appcation Proxy you have to enable first some prerequsisites , for the Connector and then make the Integration
Please go to the Docs carefully and in detail if you have not yet done it!
https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-config-sso-how-to
https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-deployment-plan
https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-add-on-premises-application
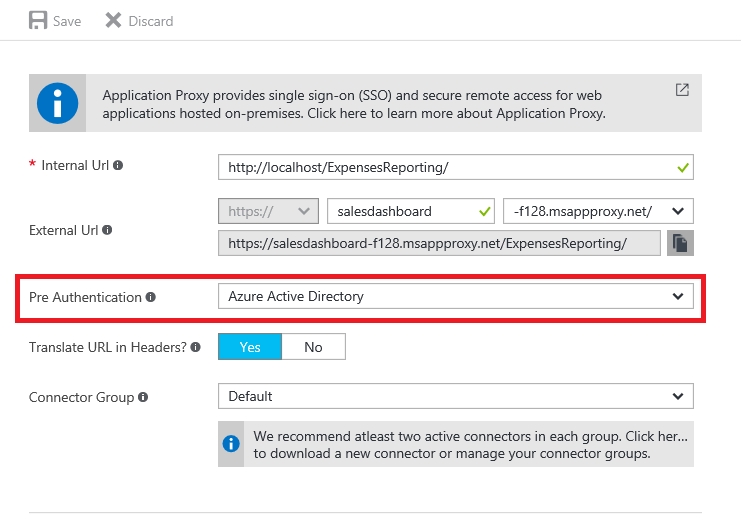
If you change to Pass through, are you presented with the Login Page ?
You need to meet the following prerequisites before beginning your implementation. You can see more information on setting up your environment, including these prerequisites, in this tutorial.
Connectors: Connectors are lightweight agents that you can deploy onto:
Physical hardware on-premises
A VM hosted within any hypervisor solution
A VM hosted in Azure to enable outbound connection to the Application Proxy service.
See Understand Azure AD App Proxy Connectors for a more detailed overview.
Connector machines must be enabled for TLS 1.2 before installing the connectors.
If possible, deploy connectors in the same network and segment as the back-end web application servers. It's best to deploy connectors after you complete a discovery of applications.
We recommend that each connector group has at least two connectors to provide high availability and scale. Having three connectors is optimal in case you may need to service a machine at any point. Review the connector capacity table to help with deciding what type of machine to install connectors on. The larger the machine the more buffer and performant the connector will be.
Network access settings: Azure AD Application Proxy connectors connect to Azure via HTTPS (TCP Port 443) and HTTP (TCP Port 80).
Terminating connector TLS traffic isn't supported and will prevent connectors from establishing a secure channel with their respective Azure App Proxy endpoints.
Avoid all forms of inline inspection on outbound TLS communications between connectors and Azure. Internal inspection between a connector and backend applications is possible, but could degrade the user experience, and as such, isn't recommended.
Load balancing of the connectors themselves is also not supported, or even necessary.
For custom Domain you need the certificate
Also
This table shows requirements for specific attributes in the SAML 2.0 message.
NameIDThe value of this assertion must be the same as the Azure AD user’s ImmutableID. It can be up to 64 alpha numeric characters. Any non-html safe characters must be encoded, for example a “+” character is shown as “.2B”.IDPEmailThe User Principal Name (UPN) is listed in the SAML response as an element with the name IDPEmail The user’s UserPrincipalName (UPN) in Azure AD/Microsoft 365. The UPN is in email address format. UPN value in Windows Microsoft 365 (Azure Active Directory).IssuerRequired to be a URI of the identity provider. Do not reuse the Issuer from the sample messages. If you have multiple top-level domains in your Azure AD tenants the Issuer must match the specified URI setting configured per domain.Important
Azure AD currently supports the following NameID Format URI for SAML 2.0:urn:oasis:names:tc:SAML:2.0:nameid-format:persistent.
Think of it like a 2 step process , Application Proxy Integration and SSO with SAML
I hope this helps!
Kindly mark the answer as Accepted and Upvote in case it helped!
Regards
