Hi @Ghasem Sherafati ,
Thanks for reaching out.
You are not able to validate the token as the issuer URL specified in the code sample is the issuer of V1.
The issuer value depends on the Access token version.
Also, if you check OIDC metadata endpoint v1 (https://login.microsoftonline.com/common/.well-known/openid-configuration), issuer will be sts.windows.net and
for OIDC metadata endpoint v2 (https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration), issuer will be login.microsoft.com.
To get the V2 access token, update the accessTokenAcceptedVersion value to 2 in the manifest of your registered application .
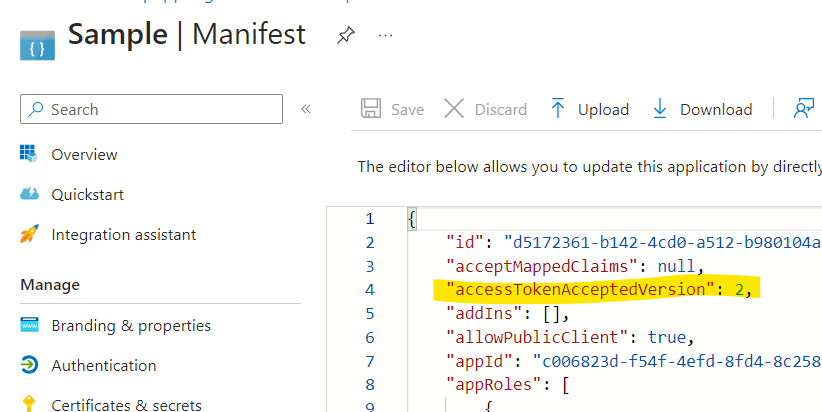
Ideally when validating an access token, the audience, and issuer mostly validated. This validation happens against the OpenId discovery endpoint. Now the issuer value is usually the same as the one mentioned in the OpenID Discovery endpoint.
https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration
Update the line 104, the value of issuer to
https://login.microsoftonline.com/{tenantid}/v2.0
along with accessTokenAcceptedVersion to 2 to validate the access token.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.