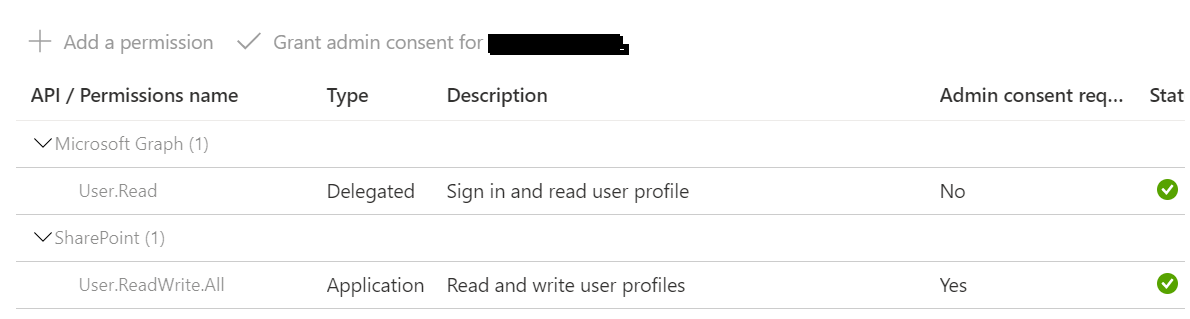
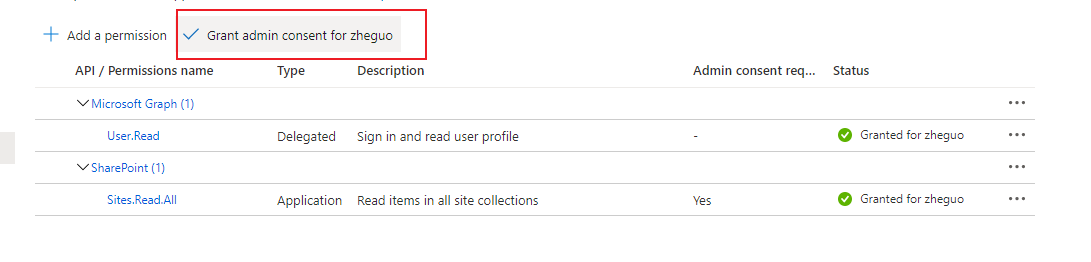
Hello! I'm running into a permissions issue when attempting to access SharePoint site data using the v1 api. I have an application registered in the Azure portal that has the SharePoint/Sites.Read.All permission granted to it. I'm using the OAuth2 flow to obtain an access token, and I've confirmed using the token decoding tool that those permission scopes are granted to the token that's returned. However, I always receive a 401 Unauthorized response from the API, and I cannot figure out where I'm going wrong with provisioning the access token.
The access token request I'm sending (I've tried client_id both with and without the @<tenant-id> included):
new Request({
url: 'https://login.microsoftonline.com/<co-domain>/oauth2/token',
method: 'POST',
header: 'Content-Type: application/x-www-form-urlencoded',
body: client_id=<client_id>@<tenant-id>
&client_secret=<client-secret>
&grant_type=client_credentials
&resource=00000003-0000-0ff1-ce00-000000000000/<co-domain>.sharepoint.com@<tenant-id>
&scope=https://<co-domain>.sharepoint.com/.default`,
})
The token returned has this value for permissions:
"roles": [
"Sites.Read.All"
],
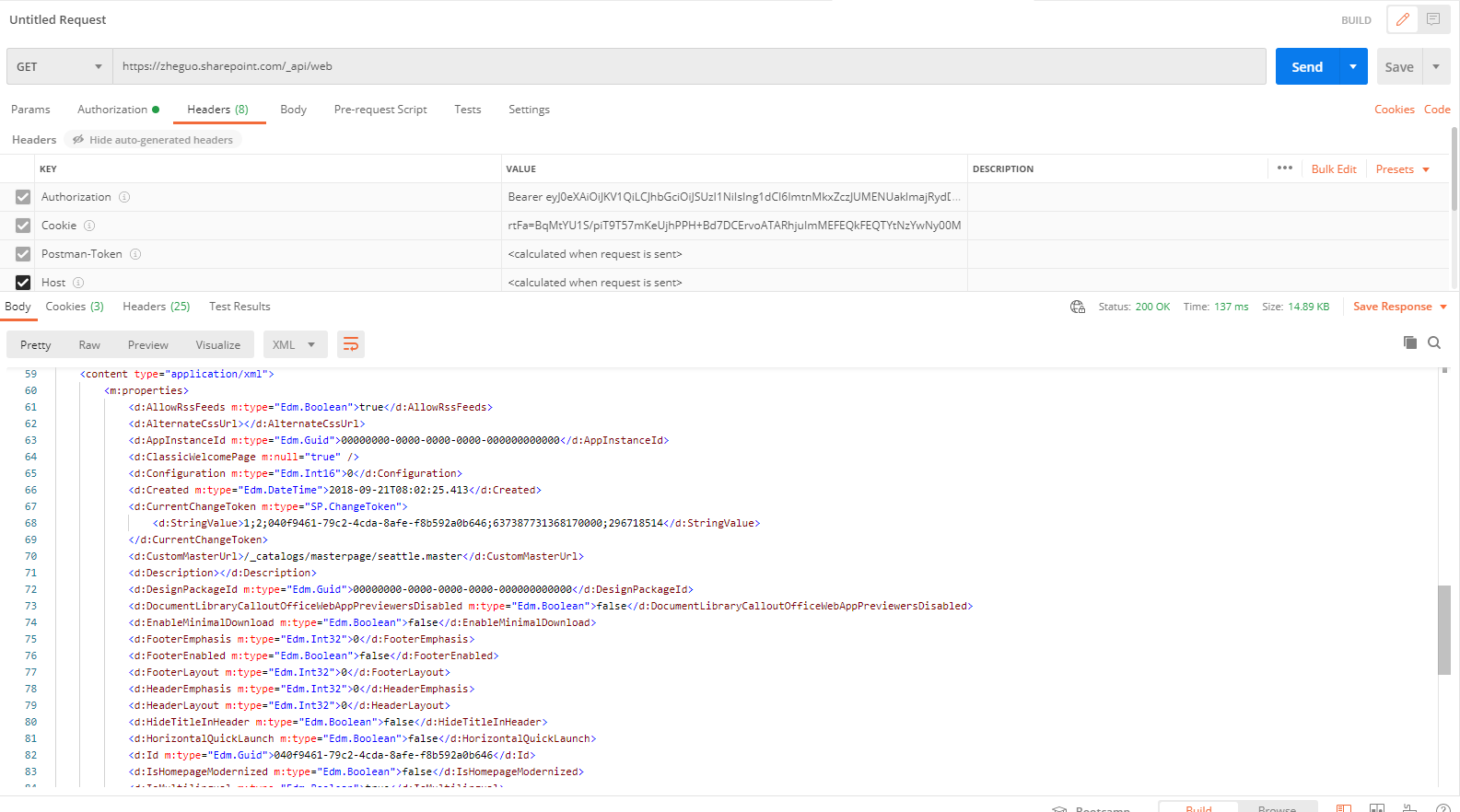
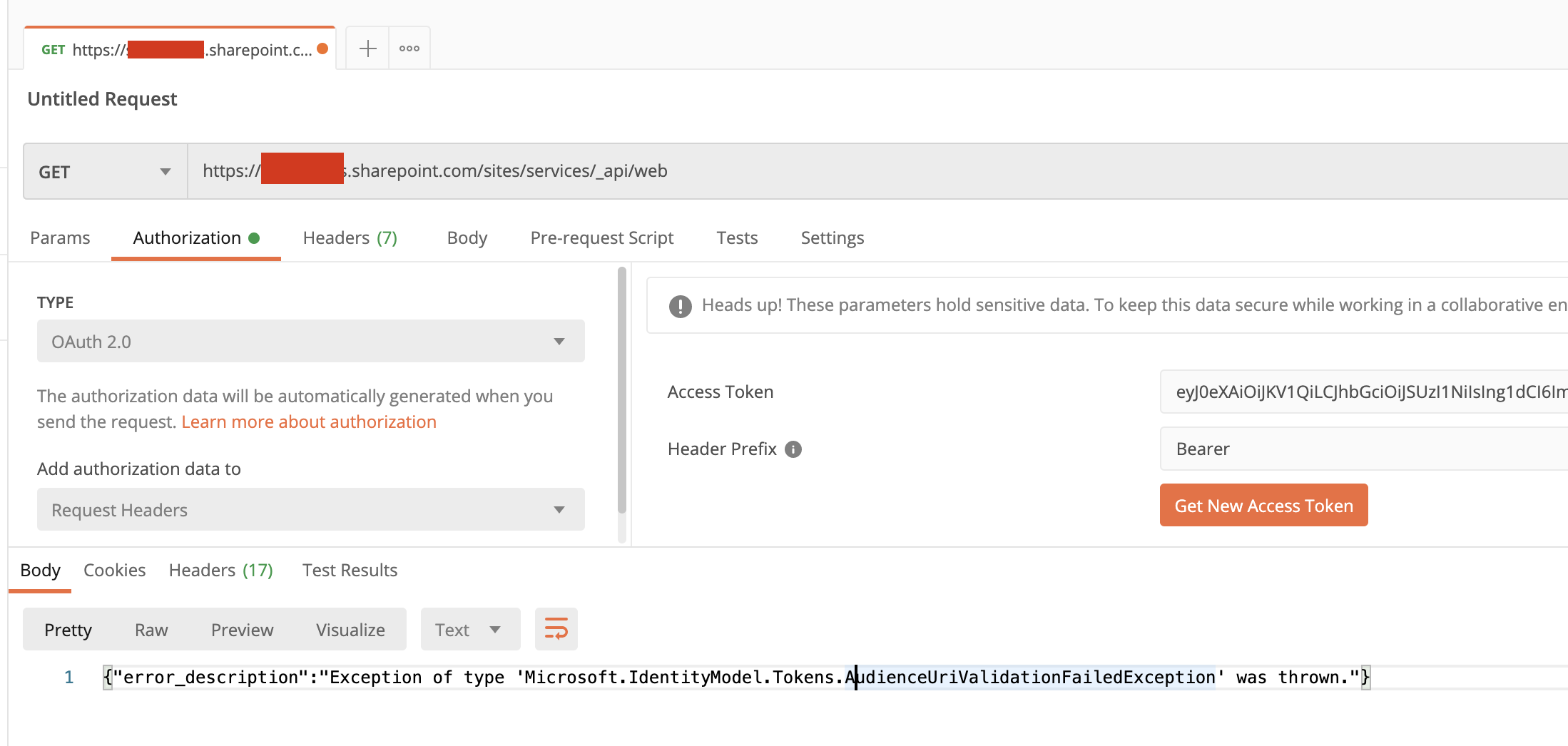
I then hit the API endpoint https://<co-domain>.sharepoint.com/sites/<site-name>/_api/web and receive this response:
{
"error": {
"code": "-2147024891, System.UnauthorizedAccessException",
"message": {
"lang": "en-US",
"value": "Access denied. You do not have permission to perform this action or access this resource."
}
}
}
Can anyone help point me in the right direction as to what I'm doing wrong and how I can properly provision an access token for reading data from the v1 SharePoint API?
Also, a note: I cannot use Microsoft Graph because that api does not return the information I need (site page metadata and useful things like thumbnails and page descriptions). This data is available only in the v1 api.