Hello @Hithesh Chowdary , I did some more research and it looks like an issue of illicit consent.
This issue happens because of something called Risk-based Step-up consent.
Risk-based step-up consent helps reduce user exposure to malicious apps making illicit consent requests. If Microsoft detects a risky end-user consent request, the request will require a "step-up" to admin consent instead. This capability is enabled by default, but it will only result in a behavior change when end-user consent is enabled.
When a risky consent request is detected, the consent prompt will display a message indicating that admin approval is needed.
So it is expected that this will happen to some apps if they meet our criteria. This is documented as one of the "unexpected consent errors" here: https://learn.microsoft.com/en-us/azure/active-directory/manage-apps/application-sign-in-unexpected-user-consent-error#requesting-not-authorized-permissions-error
• AADSTS90093: <clientAppDisplayName> is requesting one or more permissions that you are not authorized to grant. Contact an administrator, who can consent to this application on your behalf.
• AADSTS90094: <clientAppDisplayName> needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it.
That said if this is a valid, non-malicious app we do want to make sure the developer is not blocked on this going forward
In order to get them unblocked immediately, the consent request can be sent to an admin for review and potential approval
References: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/detect-and-remediate-illicit-consent-grants?view=o365-worldwide
https://learn.microsoft.com/en-us/azure/active-directory/manage-apps/application-sign-in-unexpected-user-consent-error#requesting-not-authorized-permissions-error
I am looking for some more insights on this and I will keep you posted with the next set of details. For now, you can try two things:
- Try to make the app verified, by adding a verified domain to your tenant
- Try enabling the option:
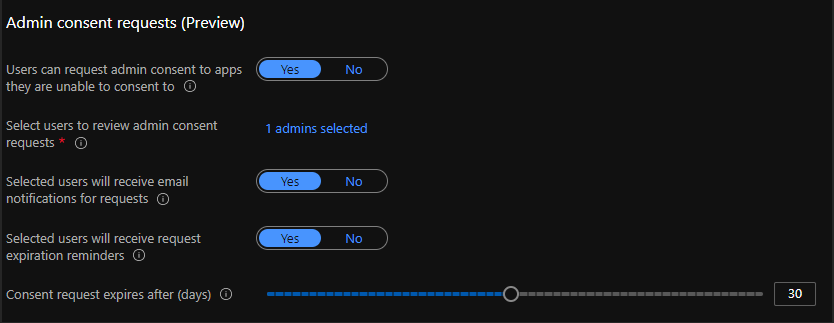
Option 2 is a tedious join for the admin to keep providing consent for the users, but if your user-base is a fixed one, then it would be a one-time thing for the admin. Moreover, the admin would only get a notification that someone is trying to access the app, and based on the justification, the admin can authorize that user’s access.
For now, I have these options in hand. I will share more insights with you once I can get hands-on those.


