Hi All,
I'm adding here an eventual solution to this.
Note this is a mere suggestion on how to create a set of policies that cover scenarios described, note sure if any changes on Azure/AKS ARM end could break functionality of these in the future.
Essentially there are 2 scenarios to cover.
First - Creation of AKS cluster must have Node Labels
Policy checks if,
- Type is of “Managed Clusters”
- Count for node labels is not equals to ‘0’ (zero) – Counts if,
- “Node Labels” field from a node pool doesn’t exist on incoming ARM template
- “Node Labels” field from a node pool is empty on incoming ARM template
And denies Cluster creation if Count for node labels is not equals to ‘0’ (zero)
Adding some explanation to how point 2.b) is working, since is the one that seems to be giving the most headaches, please understand that we have taken a look into ARM templates that are generate when az cli commands for cluster creation are executed,
Example,
$ az aks create -g $RSG -n $AKS_NAME -c 1 --nodepool-labels "" --debug
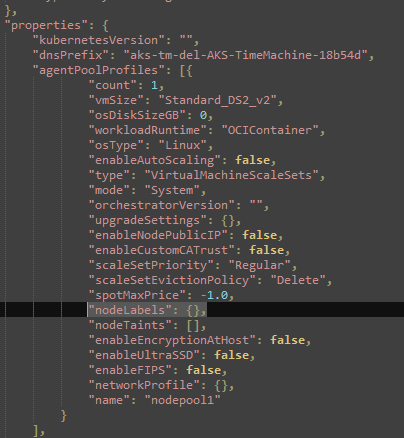
And found that “nodeLabels” field from an “agentPoolProfiles” object is filled with “{}”. Since “nodeLabels” field is an array/list the direct string you will find when empty will be “[{}]”.
Then due to how Language used by Policies works we need to escape “[” character by adding another “[“ before, otherwise it will be read as a different directive.
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.ContainerService/managedClusters"
},
{
"count": {
"field": "Microsoft.ContainerService/managedClusters/agentPoolProfiles[*]",
"where": {
"anyOf": [
{
"field": "Microsoft.ContainerService/managedClusters/agentPoolProfiles[*].nodeLabels",
"exists": "false"
},
{
"value": "[string(field('Microsoft.ContainerService/managedClusters/agentPoolProfiles[*].nodeLabels'))]",
"equals": "[[{}]"
}
]
}
},
"notEquals": 0
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {}
}
Second - Node Pools being added must have Node Labels
Policy checks if,
- “Node Label” does not exists
- Value of “nodeLabel” field from a node pool is empty on incoming ARM template
And denies Node Pool creation/Addition when one any od above conditions is meet (i.e. is True)
On point 2) we check if value is equal to “{}”.
{
"mode": "All",
"policyRule": {
"if": {
"anyOf": [
{
"not": {
"field": "Microsoft.ContainerService/managedClusters/agentPools/nodeLabels",
"exists": "true"
}
},
{
"value": "[string(field('Microsoft.ContainerService/managedClusters/agentPools/nodeLabels'))]",
"equals": "{}"
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {}
}
