Hi,
When creating exclusions in a AFD Premium WAF policy, you have the choice out of 5 different Matchvariables: RequestHeaderNames, RequestCookieNames, QueryStringArgNames, RequestBodyPostArgNames, RequestBodyJsonArgNames (see https://learn.microsoft.com/en-us/azure/templates/microsoft.network/frontdoorwebapplicationfirewallpolicies?pivots=deployment-language-bicep#managedruleexclusion).
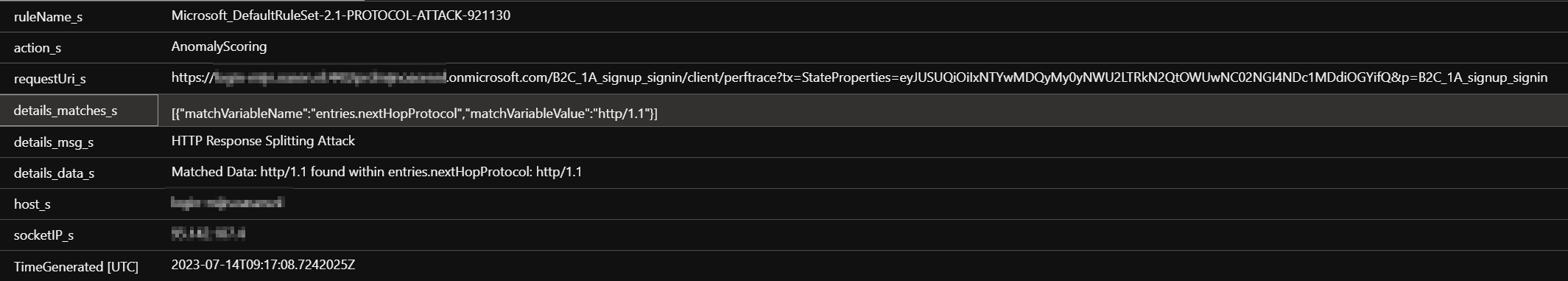
Now I have a false positive coming from Azure B2C where the Matchvariablename is "entries.nextHopProtocol" (see attached image). This false positive is coming from this AB2C login request: https://myURL:443/mytenant.onmicrosoft.com/B2C_1A_signup_signin/client/perftrace?tx=StateProperties=eyJUSUQiOiIxNTYwMDQyMy0yNWU2LTRkN2QtOWUwNC02NGI4NDc1MDdiOGYifQ&p=B2C_1A_signup_signin
This triggers on rule Microsoft_DefaultRuleSet-2.1-PROTOCOL-ATTACK-921130 and it triggers a subsequent BLOCK! for [{"matchVariableName":"entries.nextHopProtocol","matchVariableValue":"http/1.1"}]. How can I exclude this one when it does not fit any of the 5 Matchvariables?
Regards
