
To start - emails from @accountprotection.microsoft.com are legitimately from Microsoft:
Also, I'm guessing that your clients are B2B guests? If so, all anyone needs to start the authentication is to supply their email address in your tenancy. MSFT then just sends a one-time passcode to their email and waits for them to enter in the passcode.
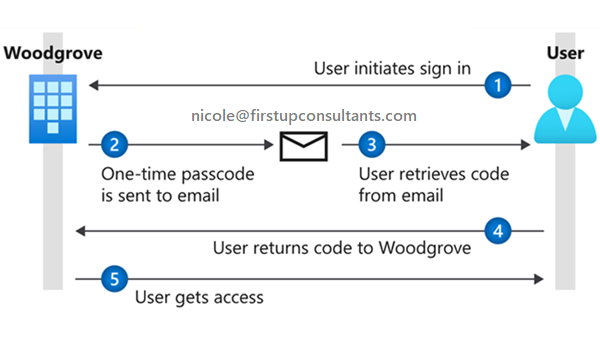
Question: have you examined your Azure/M365 audit logs? You should see the auth/sign in requests that mirror the OTP codes being sent.
I'm guessing you'll see a status of interaction_required because the requester didn't enter one in. However, I would specifically look at the origin IP or location/country.
If its some kind of password spraying event, you'll see the orgin country from all over the globe..
Since the OTP is sent upon supplying a registered email, what you could do is filter it with a conditional access policy with restrictions such as:
- Geofencing
- Blocking of non-standard/non-corporate standards (Example: blocking of Windows Phone; Linux, Chromebooks etc.
Hope that helps