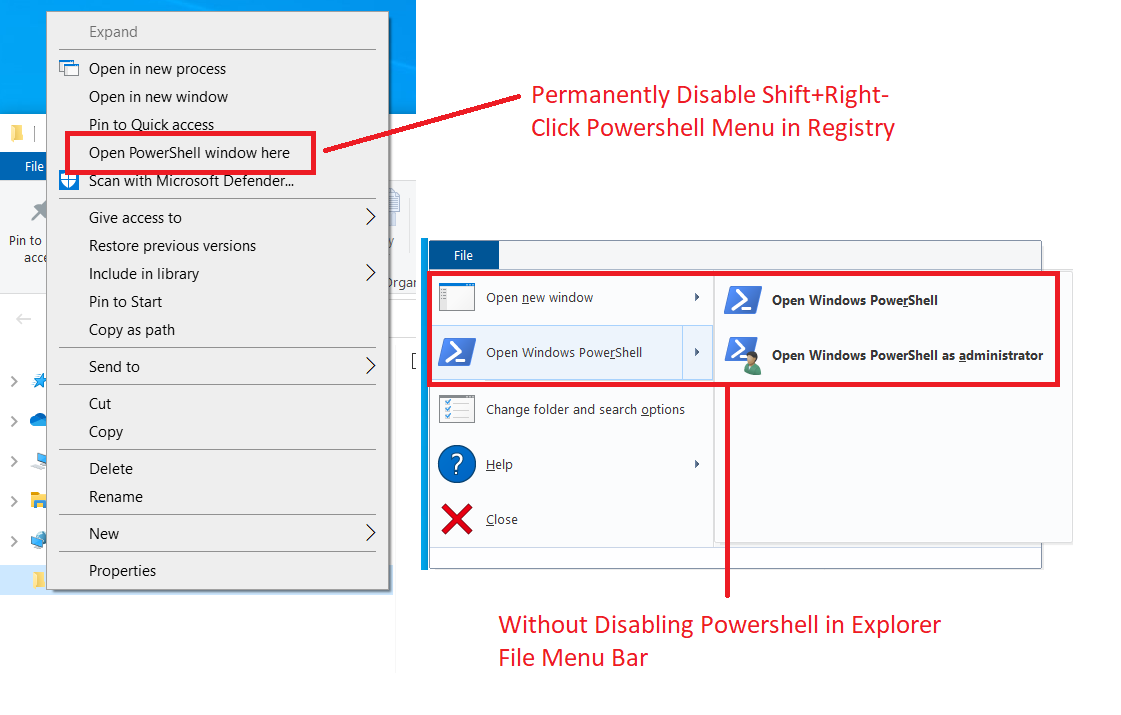
How would one permanently disable Shift+Right-Click "Open PowerShell window here" context menu without simultaneously disabling the PowerShell and Elevated PowerShell Options in the File Explorer File Menu Bar?
More info: For Registry Keys [HKLM\Software\Classes\Directory\shell\PowerShell], [HKLM\Software\Classes\DirectoryBackground\shell\PowerShell], and [HKLM\Software\Classes\Drive\shell\PowerShell] keys, the default Shift+Right-Click "Open with PowerShell window here" context menu can be disabled by adding "LegacyDisable" or "ProgrammaticAccessOnly" strings. Doing so, however, also disables (greys out) the PowerShell and Admin PowerShell Options in Explorer File Menu bar.
What would be the correct string or dword or any registry modification to disable the shift+right-click menu without disabling the Explorer File Menu bar options?
Would the keys above be the correct ones to modify? Perhaps a CLSID key or a key from the window command store? [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell]?
Thanks!
