To get the on-premises attribute in access token, first you will have to sync that particular attribute to Azure AD. If it is custom attribute in on-premises then you will have to use the AD connect directory extension and sync the custom attribute to Azure AD using AD connect.
You can refer below article to sync the custom attribute using AD connect.
Once you have the attribute synced to Azure AD, you will have to create a claim policy in Azure and link the policy to corresponding service principal of the application registered.
In the claim policy you will have to configure the claims which needs to be sent in access token.
You can follow below steps to configure the policy and link it to corresponding service principal.
In below example consider sending attribute "onPremisesSamAccount name" from Azure AD as claim in access token.
you can add the onPremisesSamAccount name to the claims and send it within an access token.
You can follow the steps mentioned below:
- Create an AzureADPolicy.
New-AzureADPolicy -Definition @('{
"ClaimsMappingPolicy": {
"Version": 1,
"IncludeBasicClaimSet": "true",
"ClaimsSchema": [{
"Source": "user",
"ID": "employeeid",
"SamlClaimType": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/employeeid",
"JwtClaimType": "employeeid"
},
{
"Source": "user",
"ID": "mail",
"SamlClaimType": "http://schemas.microsoft.com/identity/claims/emailaddress",
"JwtClaimType": "mail"
},
{
"Source": "user",
"ID": "onpremisessamaccountname",
"SamlClaimType": "samaccountname",
"JwtClaimType": "samAccountName"
},
{
"Source": "user",
"ID": "department",
"SamlClaimType": "http://schemas.microsoft.com/identity/claims/department",
"JwtClaimType": "department"
}
]
}
}') -DisplayName "CustomClaimsPolicy1" -Type "ClaimsMappingPolicy"
- Attach the newly created AzureADPolicy to a specific AzureAD App's Serviceprincipal for which the token would be requested for.
Add-AzureADServicePrincipalPolicy -Id {object id of service principal} -RefObjectId {object id of policy}
- To check if the policy is successfully added to the ServicePrincipal or not:
Get-AzureADServicePrincipalPolicy -Id "{object id of service principal}"
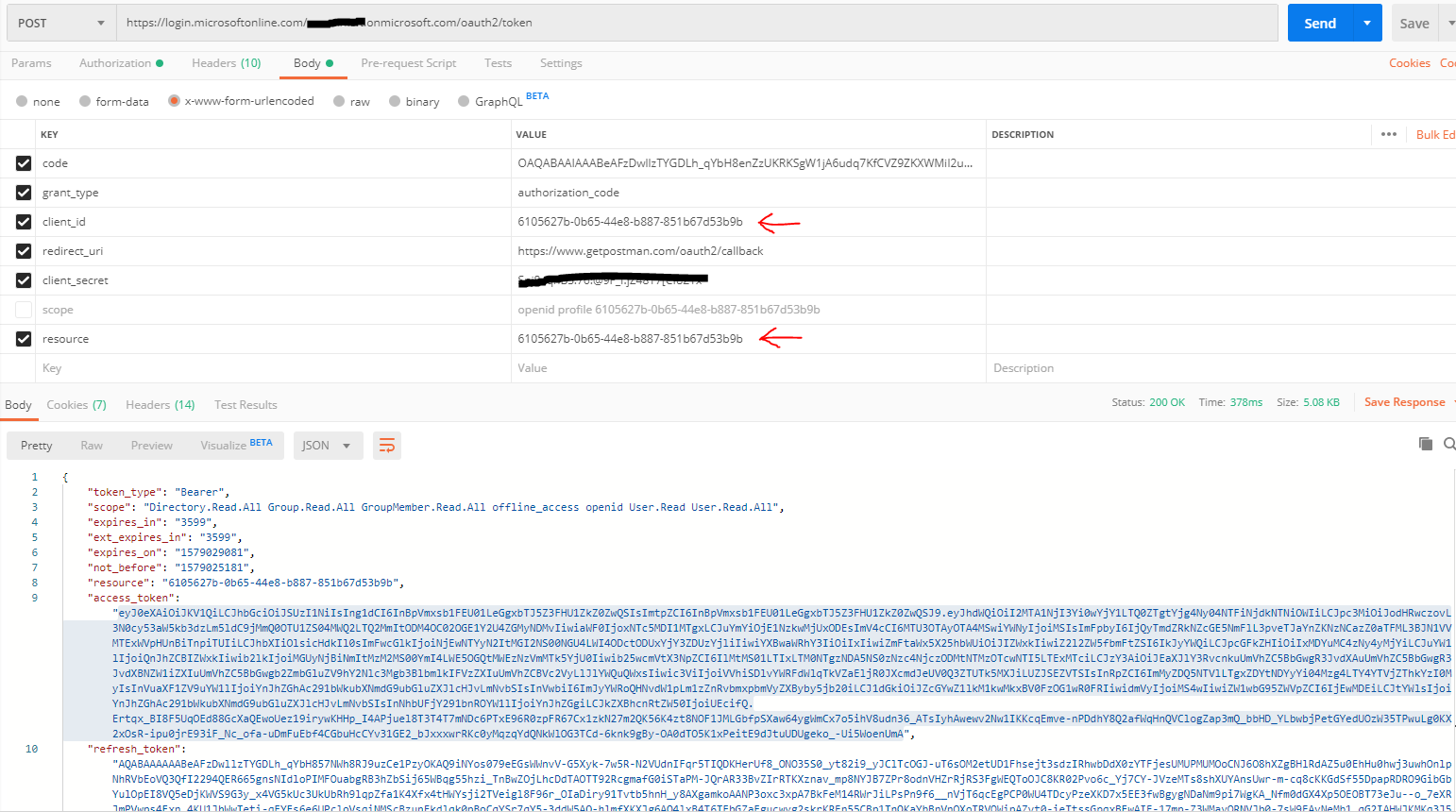
- Next you can use the Authorization Code flow of OAuth2.0 and request for a code from AAD.
- Once you have the code, use the code to request for an access token from AAD for the above app on whose ServicePrincipal the AzureADPolicy was added. [I used POSTMAN tool to test the same]
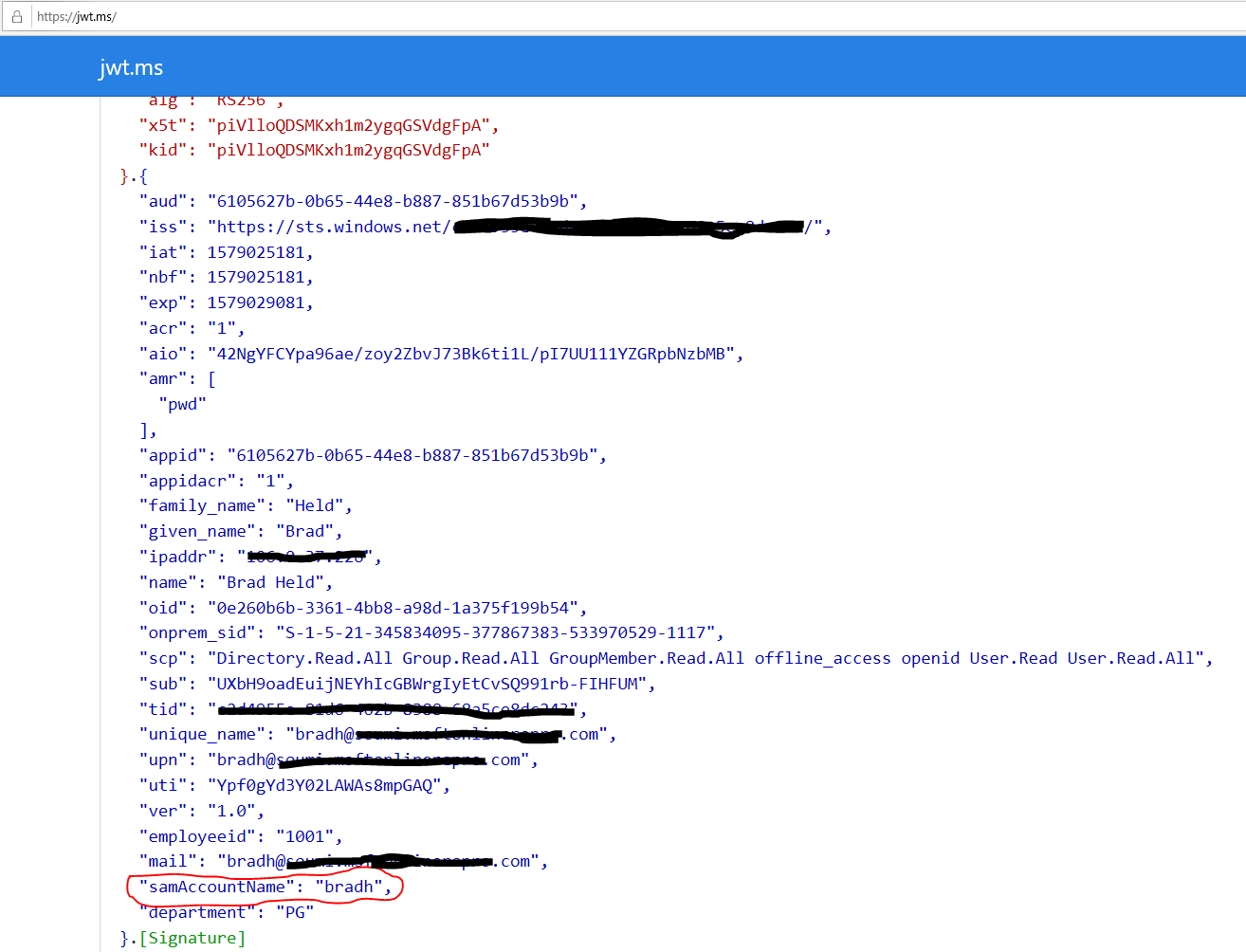
- Once you get the Access Token use https://jwt.ms to see the decoded JWT and you should see the SamAccountName listed in it as claims.
 you can add the onPremisesSamAccount name to the claims and send it within an access token. You can follow the steps mentioned below:
you can add the onPremisesSamAccount name to the claims and send it within an access token. You can follow the steps mentioned below:
1. Create an AzureADPolicy. New-AzureADPolicy -Definition @('{ "ClaimsMappingPolicy": { "Version": 1, "IncludeBasicClaimSet": "true", "ClaimsSchema": [{ "Source": "user", "ID": "employeeid", "SamlClaimType": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/employeeid", "JwtClaimType": "employeeid" }, { "Source": "user", "ID": "mail", "SamlClaimType": "http://schemas.microsoft.com/identity/claims/emailaddress", "JwtClaimType": "mail" }, { "Source": "user", "ID": "onpremisessamaccountname", "SamlClaimType": "samaccountname", "JwtClaimType": "samAccountName" }, { "Source": "user", "ID": "department", "SamlClaimType": "http://schemas.microsoft.com/identity/claims/department", "JwtClaimType": "department" } ] } }') -DisplayName "CustomClaimsPolicy1" -Type "ClaimsMappingPolicy" 1. Attach the newly created AzureADPolicy to a specific AzureAD App's Serviceprincipal for which the token would be requested for. ***Add-AzureADServicePrincipalPolicy -Id {object id of service principal} -RefObjectId {object id of policy}*** 1. To check if the policy is successfully added to the ServicePrincipal or not: ***Get-AzureADServicePrincipalPolicy -Id "{object id of service principal}"*** 1. Next you can use the Authorization Code flow of OAuth2.0 and request for a code from AAD. 1. Once you have the code, use the code to request for an access token from AAD for the above app on whose ServicePrincipal the AzureADPolicy was added. [I used POSTMAN tool to test the same]  1. Once you get the Access Token use [https://jwt.ms](https://jwt.ms/) to see the decoded JWT and you should see the **SamAccountName** listed in it as claims.  Let me know if you have any further questions on this.
- Once you get the Access Token use https://jwt.ms to see the decoded JWT and you should see the SamAccountName listed in it as claims.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.

