Hi @A ngel ,
I understand that you are trying to address security vulnerabilities in the Azure portal.
If you are referring specifically to the vulnerability assessments from Microsoft Defender for Cloud, you can go to view and remediate these findings by following these steps:
- From Defender for Cloud's menu, open the Recommendations page.
- Select the recommendation Machines should have vulnerability findings resolved.
Defender for Cloud shows you all the findings for all VMs in the currently selected subscriptions. The findings are ordered by severity.
[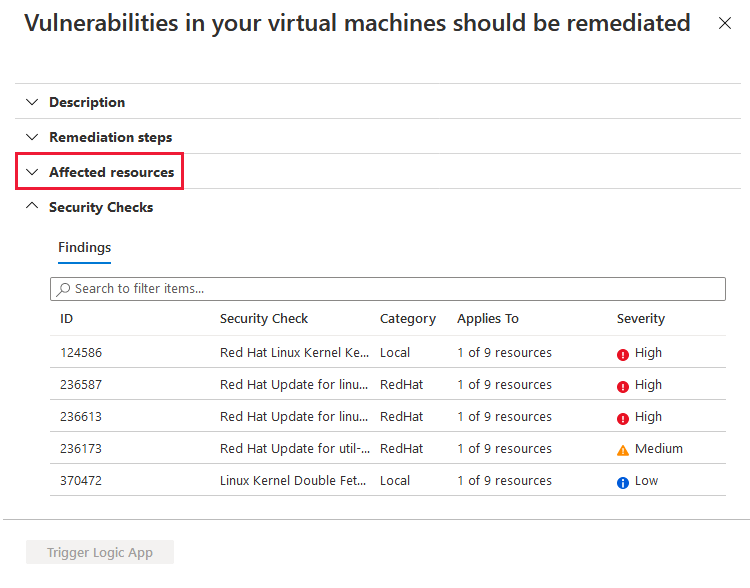
- To filter the findings by a specific VM, open the "Affected resources" section and click the VM that interests you. Or you can select a VM from the resource health view, and view all relevant recommendations for that resource.
Defender for Cloud shows the findings for that VM, ordered by severity.
- To learn more about a specific vulnerability, select it.
[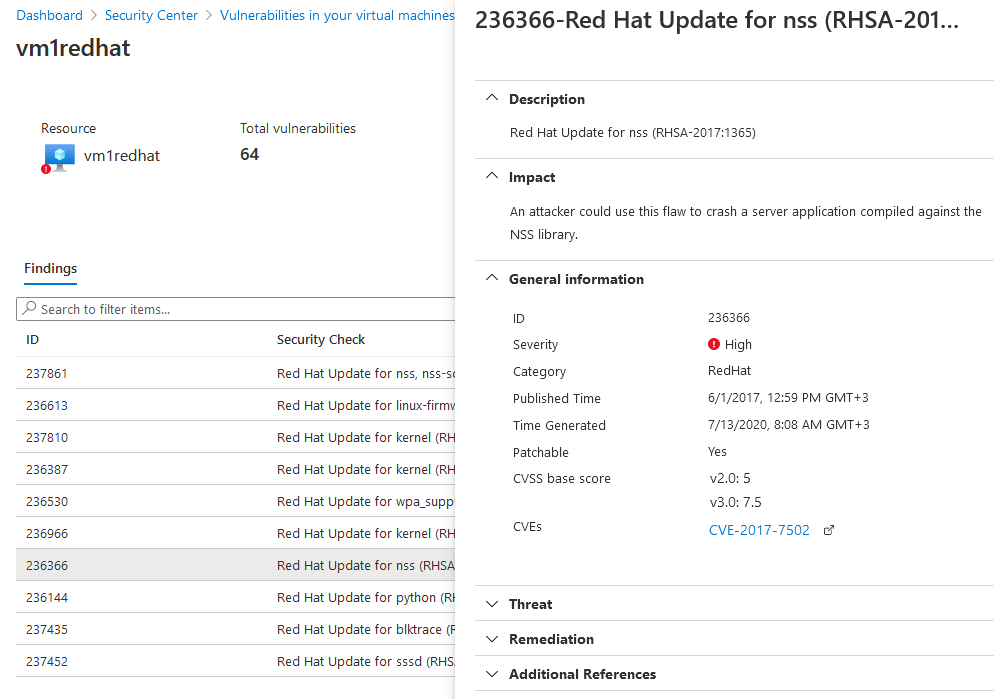
The details pane that appears contains extensive information about the vulnerability, including:
- Links to all relevant CVEs (where available)
- Remediation steps
- Any additional reference pages
- Remediation steps
- To remediate a finding, follow the remediation steps from this details pane.
If your goal is to address vulnerabilities more generally and maintain security best practices, you can monitor and respond to threat activity using the Microsoft Defender for Cloud and Microsoft Defender for Endpoint's recommendations, as well as the other security portals listed here.
I recommend reviewing the security best practices and patterns guide here, as well as the Azure Operational Security best practices guide here.
In addition, as general guidance for avoiding vulnerabilities, I would recommend the following best practices:
- Use Identity and Access Management and Role-Based Access Control to ensure that only authorized users have access to resources, and assign access using the principal of least privilege.
- Use Conditional Access to enforce security policies for accessing your resources.
- Use Azure Monitor to monitor your resources and detect security threats.
- Keep your resources updated with the latest security patches.
Let me know if this addresses your question and if you have further concerns. I'm not sure if your question was more specifically focused on the logistics of addressing Microsoft Defender for Cloud vulnerabilities, or about security best practices to avoid vulnerabilities in general. I tried to address both questions.
If the information helped you, please Accept the answer. This will help us and improve discoverability for others in the community who may be researching similar questions. Otherwise let us know if you have further concerns.