Originally posted here: https://answers.microsoft.com/en-us/windows/forum/all/how-to-include-explicit-credentials-in-a-eap-ttls/4ebdbe2d-142e-448a-a60c-64af2733a88f
Hi everyone,
I'm trying to build and install a Passpoint profile for Microsoft.
I'm able to sign the document and install it via the provisioning href as per
https://learn.microsoft.com/it-it/windows/win32/nativewifi/prov-wifi-profile-via-website
I'm trying to authenticate on an external RADIUS server. I'm confident the server itself is correctly configured because I was able to authenticate with Android and Apple devices using the same configuration (EAP-TTLS + MSCHAPv2).
What happens is that the SSL negotation succeeds and then the authentication process stops, when the inner authentication with MSCHAPv2 should start.
This is the last RADIUS exchange I see on the server:
(23653) Received Access-Request Id 74 from 87.19.229.45:58391 to 49.12.32.238:1812 length 466
(23653) User-Name = "anonymous@example.com"
(23653) Framed-MTU = 1400
(23653) EAP-Message = 0x020700a815800000009e160303006610000062610414dc5592499e454cc6f2a1b16b4326c331e6b02124c289137f1b7e1b5ed4f18c58d89d149b057541e0b44c155b65a4112416e59542cc47e37eec2a0c9f1b3e62a43708dd0bbd930f65793aa3e5196080e1a1f870d85d19957328770e624501c314030300010116030300280000000000000000ddd264c0fd7f21caec51e9ee127f0afbb06941c43e0503464e33394a1702e70b
(23653) State = 0x9283287091843dc6ff3f71dc56435ddf
(23653) HS20-AP-Version = 1
(23653) NAS-IP-Address = 192.168.1.38
(23653) Calling-Station-Id = "4C-D5-77-34-76-27"
(23653) NAS-Identifier = "E430-36972B"
(23653) NAS-Port-Id = "Andrea-802.1x"
(23653) NAS-Port-Type = Wireless-802.11
(23653) NAS-Port = 637642944
(23653) Called-Station-Id = "58-C1-7A-36-97-2B:Andrea-802.1x"
(23653) Framed-MTU = 1400
(23653) Acct-Session-Id = "58-C1-7A-36-97-2B-7E-CD-ED-64-4C-D5-77-34-76-27"
(23653) Acct-Multi-Session-Id = "33-05-9A-8D-88-64-DF-04-F2-64-4C-D5-77-34-76-27"
(23653) Message-Authenticator = 0xec7241cb1e641af03ff46e7203c3c417
(23653) session-state: No cached attributes
(23653) # Executing section authorize from file /etc/raddb/sites-enabled/cp-aaa
(23653) authorize {
(23653) [preprocess] = ok
(23653) if (Called-Station-Id == "11-11-11-11-11-11:ssid") {
(23653) if (Called-Station-Id == "11-11-11-11-11-11:ssid") -> FALSE
(23653) eap: Peer sent EAP Response (code 2) ID 7 length 168
(23653) eap: Continuing tunnel setup
(23653) [eap] = ok
(23653) } # authorize = ok
(23653) Found Auth-Type = eap
(23653) # Executing group from file /etc/raddb/sites-enabled/cp-aaa
(23653) authenticate {
(23653) eap: Expiring EAP session with state 0x116e857015fd9073
(23653) eap: Finished EAP session with state 0x9283287091843dc6
(23653) eap: Previous EAP request found for state 0x9283287091843dc6, released from the list
(23653) eap: Peer sent packet with method EAP TTLS (21)
(23653) eap: Calling submodule eap_ttls to process data
(23653) eap_ttls: Authenticate
(23653) eap_ttls: Continuing EAP-TLS
(23653) eap_ttls: Peer indicated complete TLS record size will be 158 bytes
(23653) eap_ttls: Got complete TLS record (158 bytes)
(23653) eap_ttls: [eaptls verify] = length included
(23653) eap_ttls: TLS_accept: SSLv3/TLS write server done
(23653) eap_ttls: <<< recv TLS 1.2 [length 0066]
(23653) eap_ttls: TLS_accept: SSLv3/TLS read client key exchange
(23653) eap_ttls: TLS_accept: SSLv3/TLS read change cipher spec
(23653) eap_ttls: <<< recv TLS 1.2 [length 0010]
(23653) eap_ttls: TLS_accept: SSLv3/TLS read finished
(23653) eap_ttls: >>> send TLS 1.2 [length 0001]
(23653) eap_ttls: TLS_accept: SSLv3/TLS write change cipher spec
(23653) eap_ttls: >>> send TLS 1.2 [length 0010]
(23653) eap_ttls: TLS_accept: SSLv3/TLS write finished
(23653) eap_ttls: (other): SSL negotiation finished successfully
(23653) eap_ttls: TLS - Connection Established
(23653) eap_ttls: TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(23653) eap_ttls: TLS-Session-Version = "TLS 1.2"
(23653) eap_ttls: TLS - got 51 bytes of data
(23653) eap_ttls: [eaptls process] = handled
(23653) eap: Sending EAP Request (code 1) ID 8 length 61
(23653) eap: EAP session adding &reply:State = 0x92832870968b3dc6
(23653) [eap] = handled
(23653) } # authenticate = handled
(23653) Using Post-Auth-Type Challenge
(23653) Post-Auth-Type sub-section not found. Ignoring.
(23653) session-state: Saving cached attributes
(23653) TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(23653) TLS-Session-Version = "TLS 1.2"
(23653) Sent Access-Challenge Id 74 from 49.12.32.238:1812 to 87.19.229.45:58391 length 0
(23653) EAP-Message = 0x0108003d15800000003314030300010116030300280c203ea1b8efb5f36e257e99733f980c6e9987279b7229f6d9588c395816cc96bcc603b4c4ee0bbf
(23653) Message-Authenticator = 0x00000000000000000000000000000000
(23653) State = 0x92832870968b3dc6ff3f71dc56435ddf
(23653) Finished request
And on the laptop I see "Can't connect to this network".
If I go to the Event Viewer, in the WLAN-AutoConfig section, I see the following error:
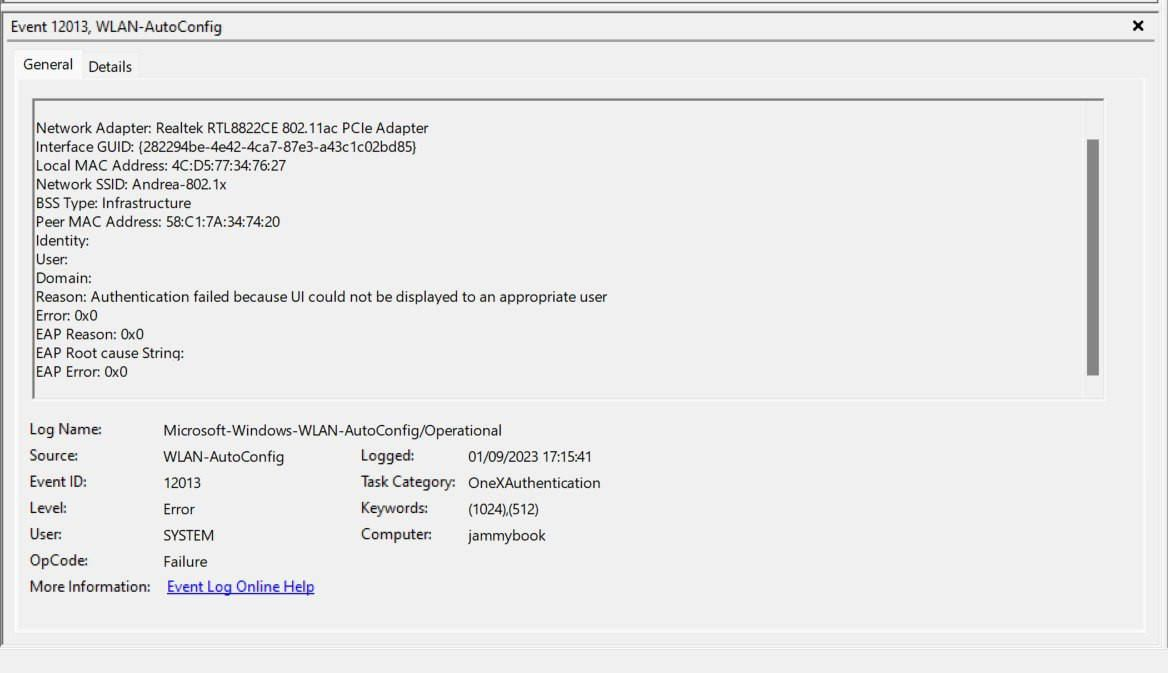
EventID: 12013
Task Category: OneXAuthentication
Authentication failed because the UI could not be displayed to an appropriate user
Now, normally when you try to connect with EAP-TTLS to a network, Windows prompts for a username and a password. But in the Passpoint profile examples provided at the link I mentioned before, there is an entire section to insert explicit credentials to be used. So that's what I'm doing in my profile:
<?xml version="1.0" encoding="UTF-8"?>
<CarrierProvisioning xmlns="http://www.microsoft.com/networking/CarrierControl/v1" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<Global>
<CarrierId>{00000000-0000-0000-0000-000000000000}</CarrierId>
<SubscriberId>1234567890</SubscriberId>
</Global>
<WLANProfiles>
<WLANProfile xmlns="http://www.microsoft.com/networking/CarrierControl/WLAN/v1">
<name>Android configuration</name>
<SSIDConfig>
<SSID>
<name>Hotspot2.1</name>
</SSID>
</SSIDConfig>
<Hotspot2>
<DomainName>[REDACTED]</DomainName>
<NAIRealm>
<name>[REDACTED]</name>
</NAIRealm>
<RoamingConsortium>
<OUI>[REDACTED]</OUI>
</RoamingConsortium>
</Hotspot2>
<MSM>
<security>
<authEncryption>
<authentication>WPA2</authentication>
<encryption>AES</encryption>
<useOneX>true</useOneX>
</authEncryption>
<PMKCacheMode>enabled</PMKCacheMode>
<PMKCacheTTL>720</PMKCacheTTL>
<PMKCacheSize>128</PMKCacheSize>
<preAuthMode>disabled</preAuthMode>
<OneX xmlns="http://www.microsoft.com/networking/OneX/v1">
<authMode>user</authMode>
<EAPConfig>
<EapHostConfig xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<EapMethod>
<Type xmlns="http://www.microsoft.com/provisioning/EapCommon">21</Type>
<VendorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorId>
<VendorType xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorType>
<AuthorId xmlns="http://www.microsoft.com/provisioning/EapCommon">311</AuthorId>
</EapMethod>
<Config>
<EapTtls xmlns="http://www.microsoft.com/provisioning/EapTtlsConnectionPropertiesV1">
<Phase2Authentication>
<MSCHAPv2Authentication>
<UseWinLogonCredentials>false</UseWinLogonCredentials>
</MSCHAPv2Authentication>
</Phase2Authentication>
<Phase1Identity>
<IdentityPrivacy>true</IdentityPrivacy>
<AnonymousIdentity>anonymous@example.com</AnonymousIdentity>
</Phase1Identity>
</EapTtls>
</Config>
</EapHostConfig>
</EAPConfig>
</OneX>
<EapHostUserCredentials xmlns="http://www.microsoft.com/provisioning/EapHostUserCredentials" xmlns:baseEap="http://www.microsoft.com/provisioning/BaseEapMethodUserCredentials" xmlns:eapCommon="http://www.microsoft.com/provisioning/EapCommon">
<EapMethod>
<eapCommon:Type>21</eapCommon:Type>
<eapCommon:AuthorId>311</eapCommon:AuthorId>
</EapMethod>
<Credentials>
<EapTtls xmlns="http://www.microsoft.com/provisioning/EapTtlsUserPropertiesV1">
<Username>[REDACTED]</Username>
<Password>[REDACTED]</Password>
</EapTtls>
</Credentials>
</EapHostUserCredentials>
</security>
</MSM>
</WLANProfile>
</WLANProfiles>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/TR/2001/REC-xml-c14n-20010315" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<ds:Reference URI="">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<ds:DigestValue>92FK69e/p7UIxu9Q2obsnwHX2pI=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue></ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>VALIDCERT</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
</CarrierProvisioning>
Based on the error, I'm assuming the configuration is ignoring my credentials, tries to prompt the user for them and fails for some reason.
I've tried different variations on this profile configuration but they all fail with the same error.
How am I supposed to pass the credentials to the profile without any prompt?
Thanks to everyone for your time.
EDIT: Scroll down in the comment section of the accepted answer to find the solution.

