I'm working on getting Windows 2022 server deployment using MDT version 8456 with Win11 ADK version 22H2 (with workarounds detailed here: https://www.deploymentresearch.com/notes-from-the-lab-on-windows-adk-for-windows-11-22h2/ - Thanks @Johan Arwidmark !) and BitLocker pre-provisioning working in my test lab first. I'm running Windows 10 with Hyper-V running as my host for my test lab. I can successfully deploy Windows Server 2022 to a VM with MDT but without BitLocker. In my particular scenario I am deploying a workgroup computer so no AD / Group Policies. Here are the properties related to BitLocker I have set for my deployment currently:
SkipBitLocker=YES
BDEInstallSuppress=NO
BdeDriveLetter=S:
BdeDriveSize=2000
BdeInstall=TPM
BdeKeyLocation=\\<myhost>\<myshare>
BdeWaitForEncryption=TRUE <--- this may not be needed with pre-provisioning, but I was seeing if this made a difference (it didn't)
I've also tried variations on a lot of these properties, including using the OSDBitLocker properties instead or in combination with BDE ones with no luck.
I'm also setting the encryption method in the task sequence to XTS-AES 256 as indicated in some other posts I found with this command:
cmd /c reg.exe add HKLM\SOFTWARE\Policies\Microsoft\FVE /v EncryptionMethod /t REG_DWORD /d 7 /f
I have enabled the vTPM for the VM I am deploying to, and in WinPE prior to running the task sequence I get this from the Get-TPM PowerShell command:
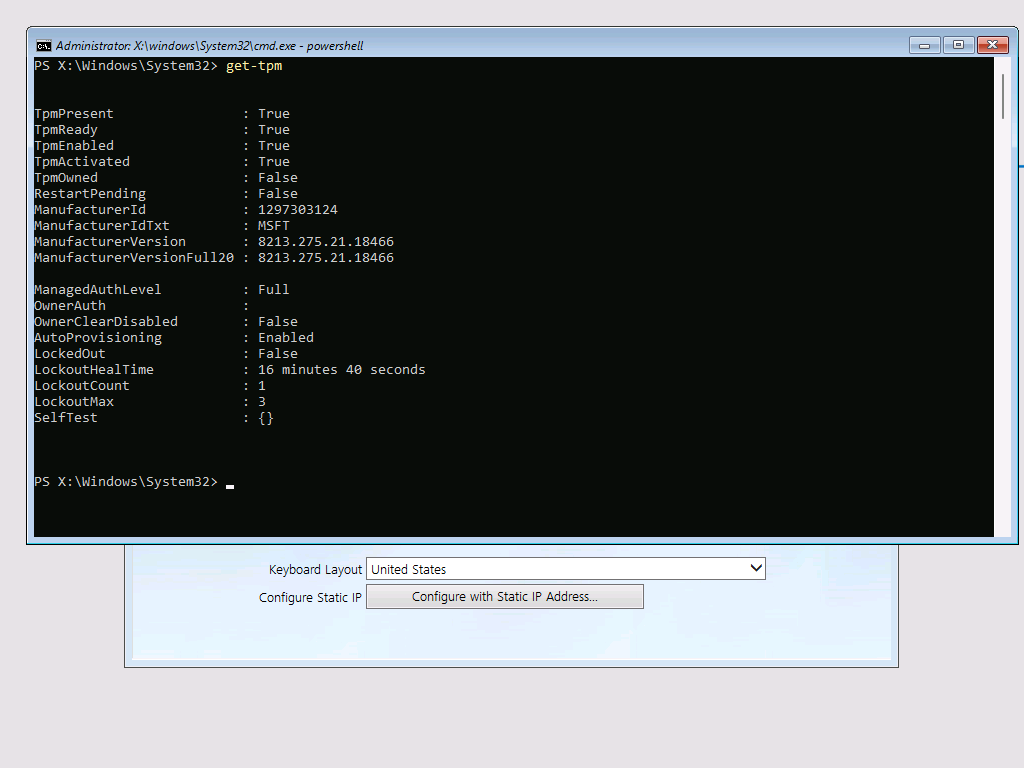
If you're interested in how I was able to add the Trusted Platform Module cmdlets to WinPE, see my comment in this question: https://learn.microsoft.com/en-us/answers/questions/1009077/tpm-check-readiness-for-task-sequence-new-operatin?page=2#answers.
There is no error in the deployment logs. Here are the entries from ZTIBDE:
System drive is: X: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
The deployment method is not using ConfigMgr. ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
We are in a Windows PE environment, checking to see if Windows PE supports Offline BitLocker tasks. ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Determining if WinPE supports pre-provisioning ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Found Offline BitLocker Tools. ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Checking to see if OS supports Offline Bitlocker. ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
OS build supports Offline BitLocker. ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
OSDTargetDriveCache was determined earlier : E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Property OSDTargetDriveCache is now = E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Property OSDisk is now = E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Pre-provisioning BitLocker on drive E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
OSDTargetDriveCache was determined earlier : E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Property OSDTargetDriveCache is now = E: ZTIBDE 9/14/2023 9:11:45 AM 0 (0x0000)
Property OSDisk is now = E: ZTIBDE 9/14/2023 9:11:46 AM 0 (0x0000)
About to run command: "X:\windows\system32\Manage-bde.exe" -on E: -used ZTIBDE 9/14/2023 9:11:46 AM 0 (0x0000)
Command has been started (process ID 15460) ZTIBDE 9/14/2023 9:11:46 AM 0 (0x0000)
ZTI Heartbeat: command has been running for 0 minutes (process ID 15460) ZTIBDE 9/14/2023 9:11:46 AM 0 (0x0000)
Event 41003 sent: ZTI Heartbeat: command has been running for 0 minutes (process ID 15460) ZTIBDE 9/14/2023 9:11:46 AM 0 (0x0000)
Return code from command = 0 ZTIBDE 9/14/2023 9:11:47 AM 0 (0x0000)
Property IsBDEPreProvisioned is now = True ZTIBDE 9/14/2023 9:11:47 AM 0 (0x0000)
ZTIBDE processing completed successfully. ZTIBDE 9/14/2023 9:11:47 AM 0 (0x0000)
Event 41001 sent: ZTIBDE processing completed successfully. ZTIBDE 9/14/2023 9:11:47 AM 0 (0x0000)
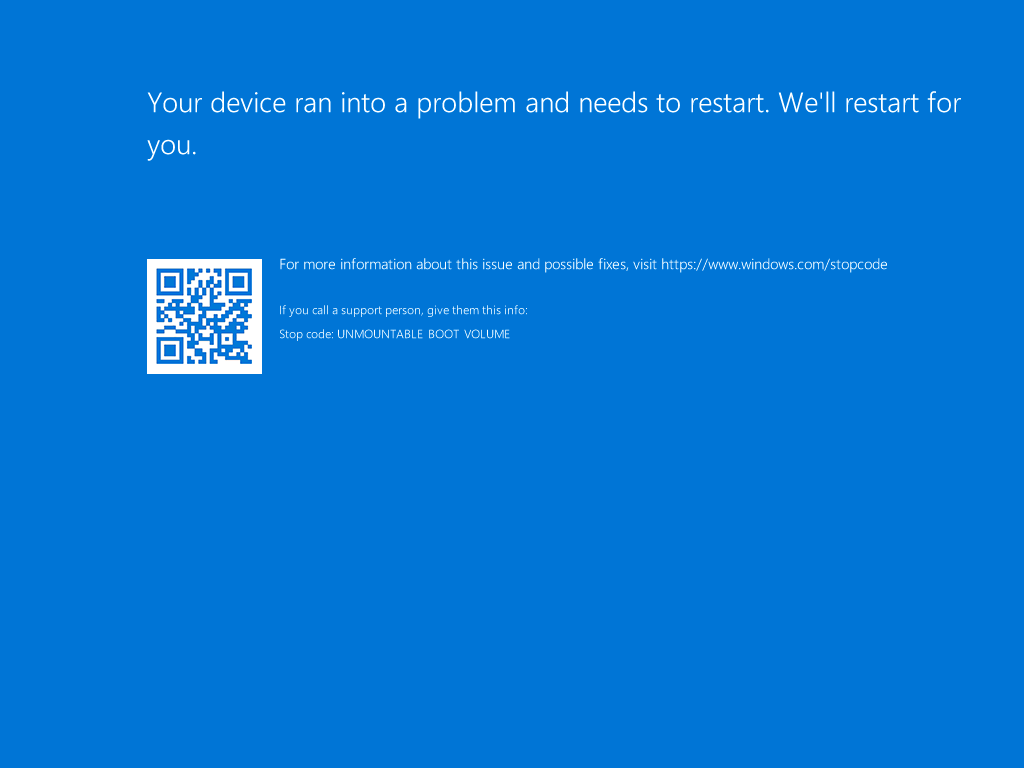
Upon the first reboot after WinPE lays down the OS, it goes into a blue screen and infinite reboot cycle:
What is interesting is that if I go back into WinPE, it can read the disk just fine:
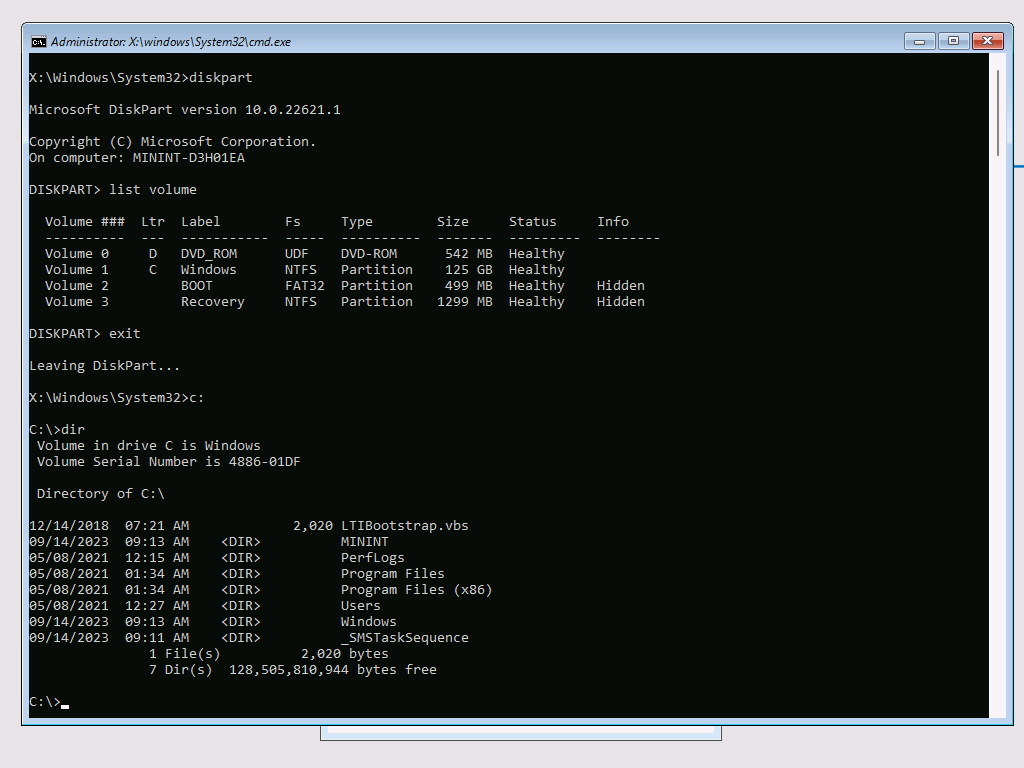
Even if I assign a drive letter to the boot partition, it can read the files:
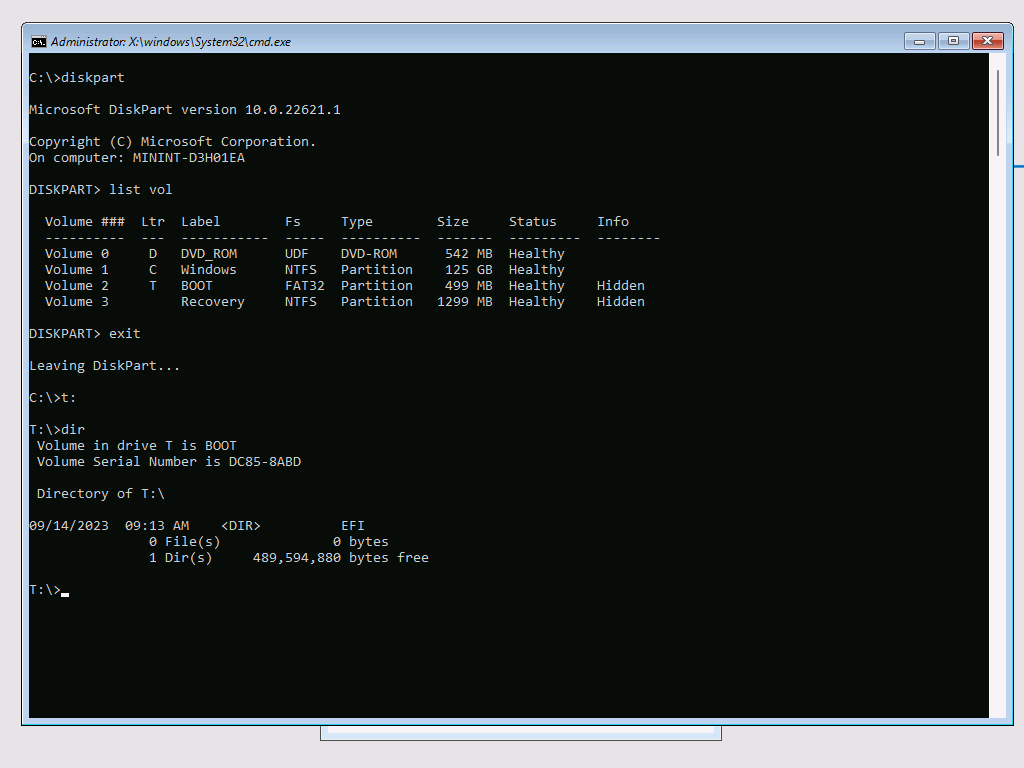
The BitLocker and vTPM status at this point:
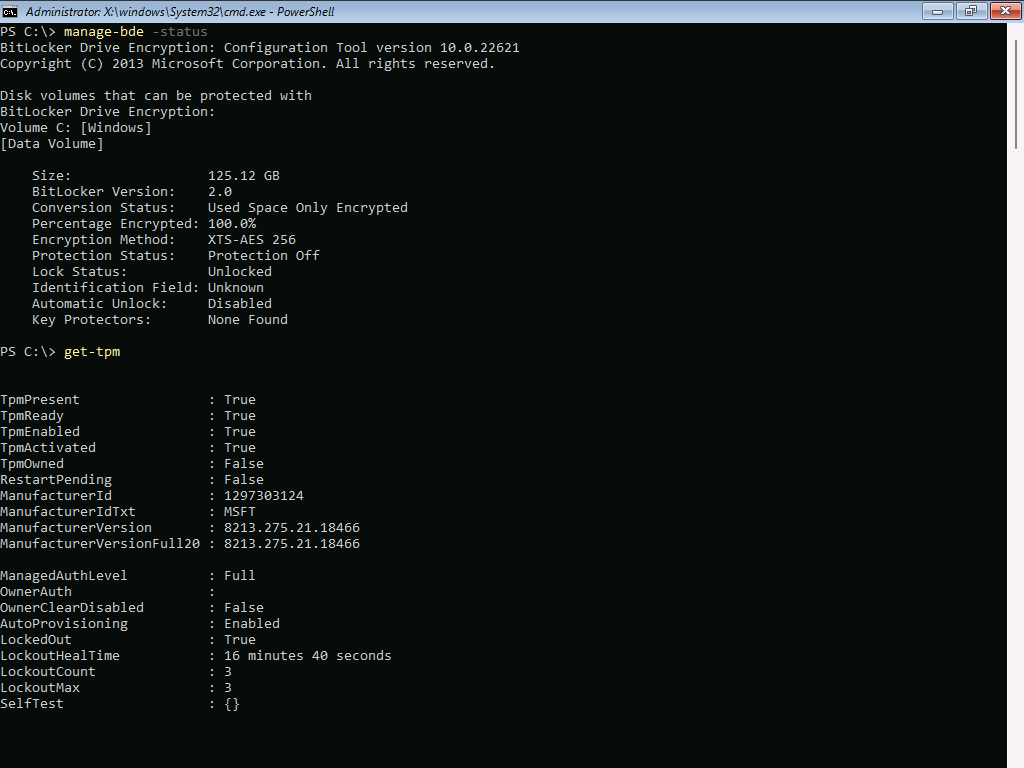
In a pre-provisioning scenario, it's not entirely clear to me on what should happen when with the vTPM and the encryption, and I haven't been able to find any clear documentation on that. I think that the vTPM should not be owned until the OS first boots so that it can take ownership, is that correct? When should the key protector be set to the vTPM and protection turned on - after pre-provisioning or after 2nd BitLocker step that occurs after the deployed OS is active? Could Automatic Unlock being disabled or AutoProvisioning being enabled be a factor (I tried disabling AutoProvisioning but still had the issue)? Or is there something completely different that I'm overlooking? I'm also wondering if pre-provisioning is normally tricky to get working and the default task sequence just doesn't work out of the box or if I am completely missing something basic.
Your assistance is greatly appreciated.