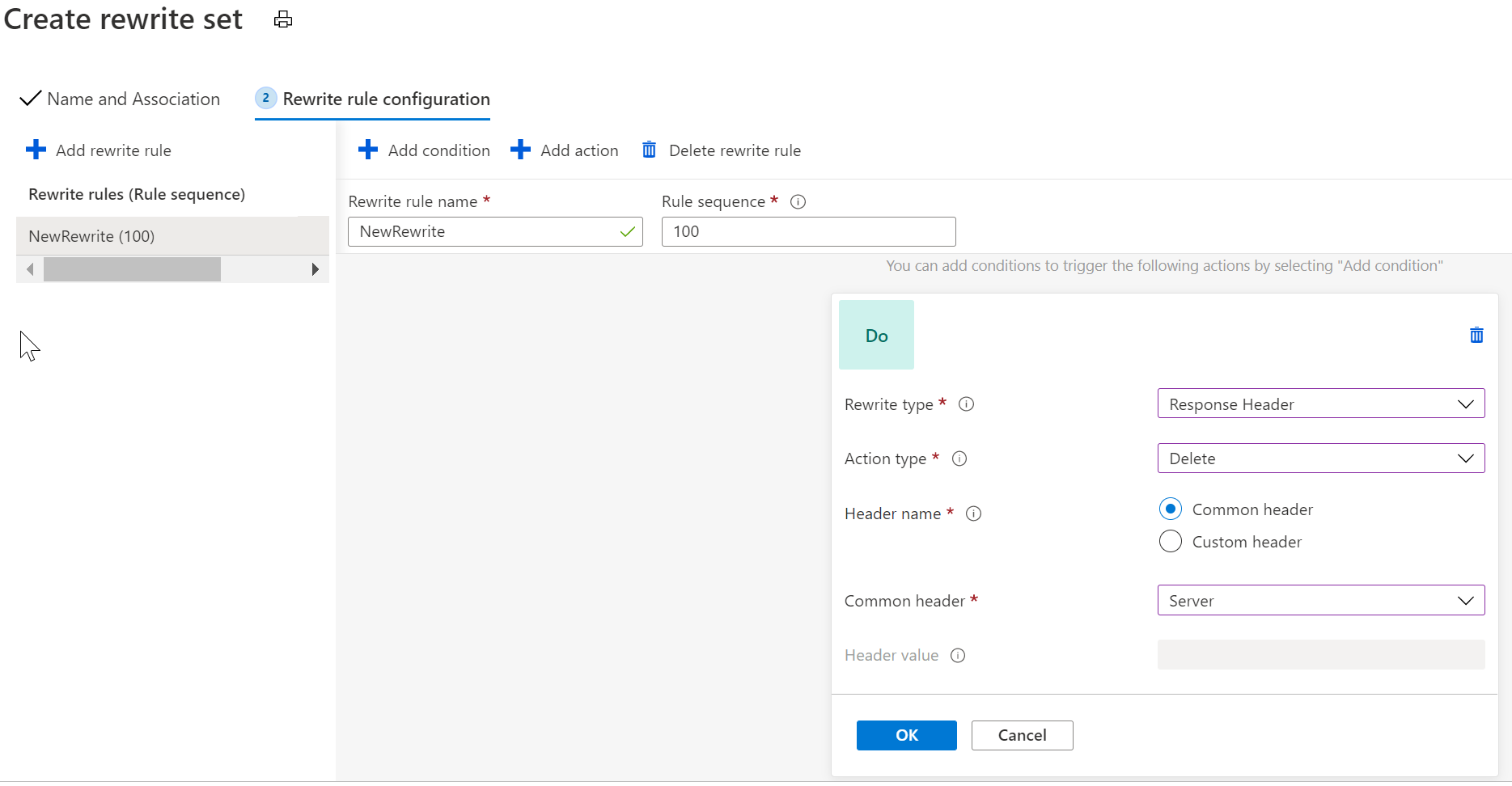
It is possible to remove this header from Application Gateway responses using Header ReWrites.
If the 'Server' header is the one you would like to remove, create a rewrite action that removes that header:
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
The Azure Application Gateway WAF V2 is vulnerable to Sensitive Data Exposure, because it responds with the Server header equal to Microsoft-Azure-Application-Gateway/v2 if it is invoked with the http TRACE method and Max-Forwards header = 0. This information helps a potential attacker to determine
as described in OWASP.
Is there any way to avoid this and thus be owasp compliant?

It is possible to remove this header from Application Gateway responses using Header ReWrites.
If the 'Server' header is the one you would like to remove, create a rewrite action that removes that header:
