We enabled Windows LAPS on our Azure tenant for around 142 Windows 11 Business Azure AD-Joined machines. They appear to be working fine initially. But encountered some issues in these few days. Let me explain.
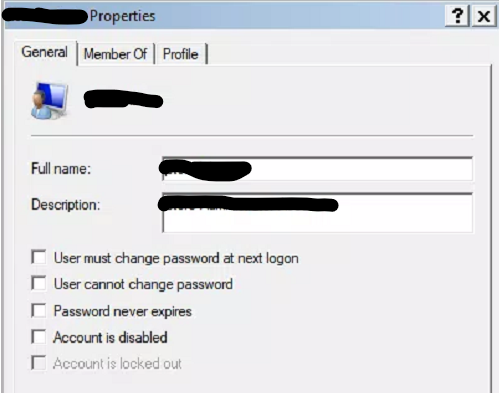
Here is what we did. First of all, we used an Intune PS script to create an extra local admin account with a name for all the machines (Note: This task is the requirement specified in the explanation of one of the Windows LAPS configurations. Not me created!). Regardless, the account was created without any password policy set (all checkboxes were left unchecked).
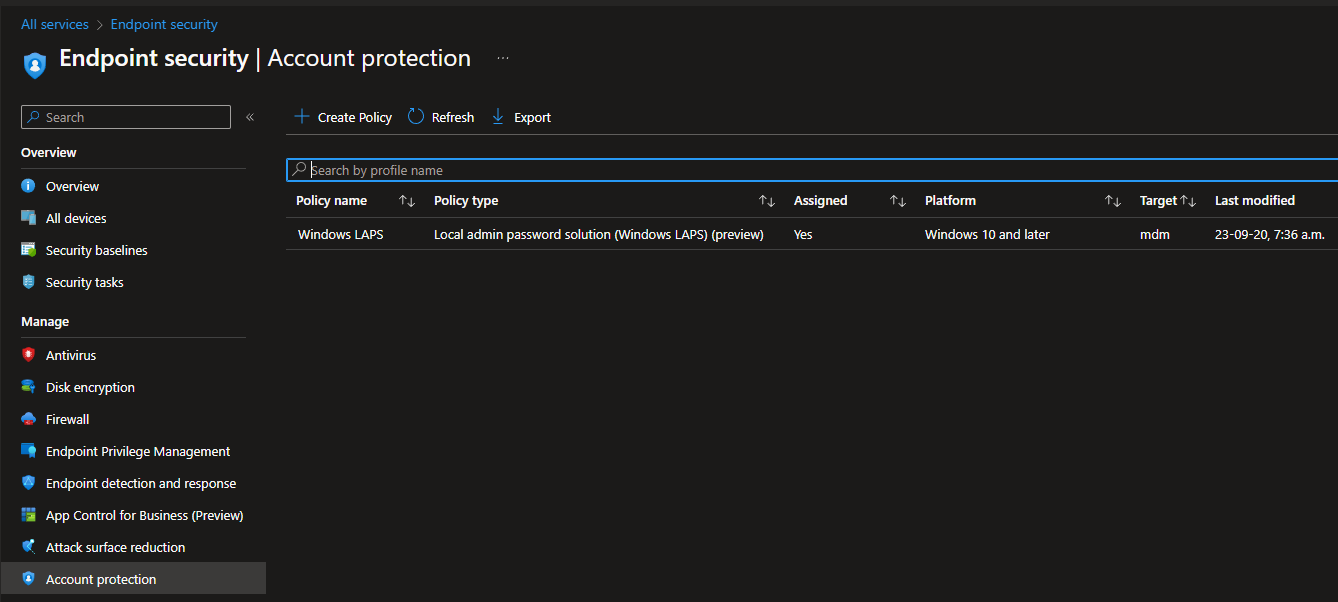
Secondly, we created a Windows LAPS policy in Intune.
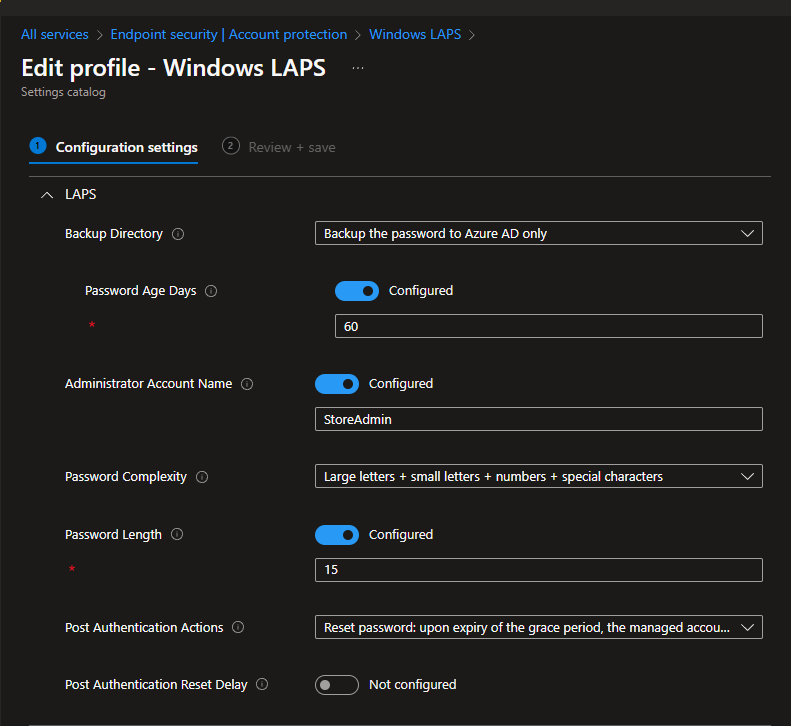
with respective configurations.
Today, we encountered a message on one of the Windows sign-on screens saying "The password has expired. Please change the password...." or something like that.
So, does the password expiry completely rely on new Windows LAPS now, or does it still depend on the local account's password expiry settings to notify users about the password expiry?
For any local account created without specifying any options like the first image provided above, will the system default settings of password policy continue to apply even though the new Windows LAPS has been enabled for the machine? I think the local system default expiry is 60 or 90 days. Is that correct?
Here is the thing. If the system defaults for the local password policy continues to apply even with the new Windows LAPS enabled with the machine, who will take precedence or both will take effect?
That is something we are confused. For the local admin account managed by the new Windows LAPS, we don't it to expire. We only want Windows LAPS to automatically rotate the password as it doing now.
Please advise what we should do. If the local system defaults still have an effect on its expiry, should I just set them all with "Password never expires"? By doing that, will it affect the new Windows LAPS not being able to rotate the password accordingly?
Please advise.
Appreciated.
WC

