Without WINRM QC, everything works under the built-in administrator. It works with the new administrator only after WINRM QC.
Please remember that there is a lot that I don't know about how your machines have been configured. If you have some policy set that restricts access to your admin user, there is no way that I would know about it. So when you ask why something "didn't work" or got "access denied", the simple answer is that I just don't know. The best that I can offer is try to help you troubleshoot the problem.
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn579255(v=ws.11)?redirectedfrom=MSDN
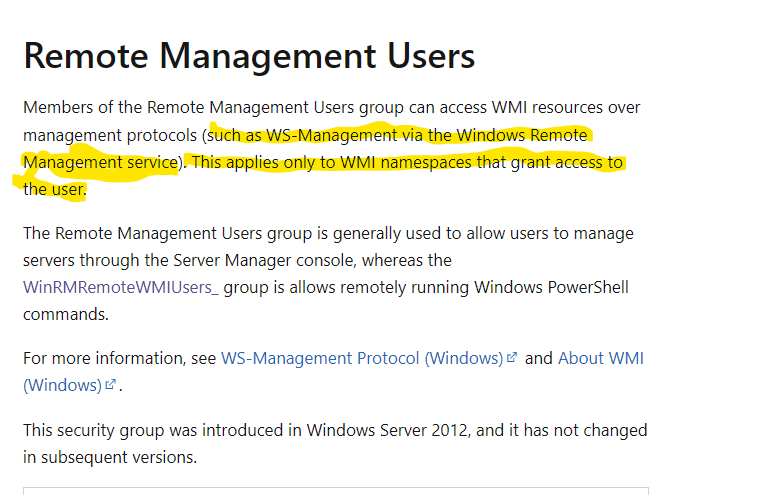
That says that adding a user to that group does not automatically grant access to everything, you also would need to resolve "This applies only to WMI namespaces that grant access to the user."
At least for now, I would recommend that you put the issue of the Remote Management group aside, and focus on getting Administrator group members to work.
On my test VM I stopped and disabled the Windows Remote Management service. That should effectively simulate a WinRM that has not been QC'd.
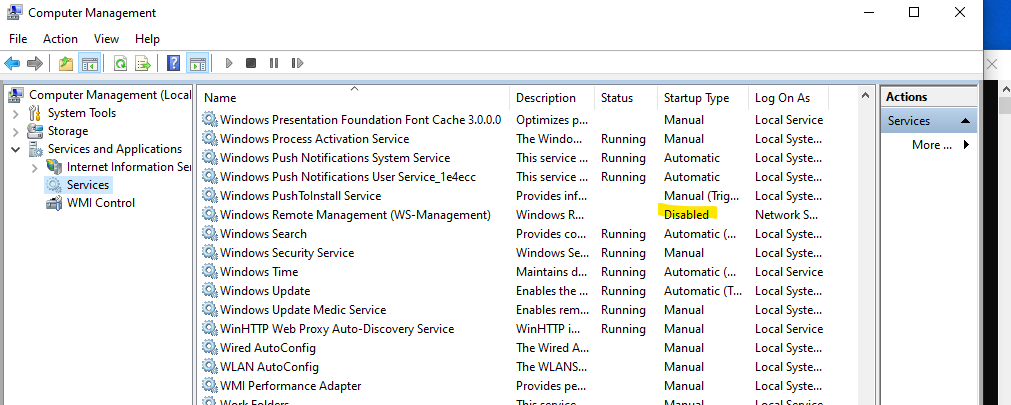
After doing that, my CimSession calls fail, but straight WMI calls, including WMIC.exe and Get-Hotfix still work.
cls
$computer = "test10"
$User = ".\admin"
$pswd = "admin"
$PWord = ConvertTo-SecureString -String $pswd -AsPlainText -Force
$Credential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $User, $PWord
"-----Testing get-wmiobject------"
Get-WmiObject -ComputerName $computer -Credential $Credential -Class WIN32_OperatingSystem | Format-Table
"-----Testing wmic------"
wmic.exe /node:$computer /user:$user /password:$pswd os get name
"-----Testing get-hotfix------"
Get-HotFix -ComputerName $computer -Credential $Credential | Select-Object -First 2 | Format-Table
"-----Testing CimSession------"
$sess = New-CimSession -ComputerName $computer -Credential $Credential
if ($sess) {
Get-CimInstance -CimSession $sess -class WIN32_Product | Format-Table
Remove-CimSession -CimSession $sess
}
"-----List administrator group members to verify that the admin user is a member------"
$group = Get-WmiObject -ComputerName $computer -Credential $Credential win32_group -filter 'Name = "Administrators"'
$group.GetRelated('Win32_UserAccount') | Format-Table
Produces this output.
-----Testing get-wmiobject------
SystemDirectory Organization BuildNumber RegisteredUser SerialNumber Version
--------------- ------------ ----------- -------------- ------------ -------
C:\Windows\system32 19045 Admin 00330-80000-00000-AA859 10.0.19045
-----Testing wmic------
Name
Microsoft Windows 10 Pro|C:\Windows|\Device\Harddisk1\Partition3
-----Testing get-hotfix------
Source Description HotFixID InstalledBy InstalledOn
------ ----------- -------- ----------- -----------
TEST10 Update KB5029919 NT AUTHORITY\SYSTEM 9/14/2023 12:00:00 AM
TEST10 Update KB5028951 NT AUTHORITY\SYSTEM 8/16/2023 12:00:00 AM
-----Testing CimSession------
New-CimSession : WinRM cannot complete the operation. Verify that the specified computer name is valid, that the
computer is accessible over the network, and that a firewall exception for the WinRM service is enabled and
allows access from this computer. By default, the WinRM firewall exception for public profiles limits access to
remote computers within the same local subnet.
At line:14 char:9
+ $sess = New-CimSession -ComputerName $computer -Credential $Credent ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ConnectionError: (:) [New-CimSession], CimException
+ FullyQualifiedErrorId : HRESULT 0x80338126,Microsoft.Management.Infrastructure.CimCmdlets.NewCimSessionCom
mand
+ PSComputerName : test10
-----List administrator group members to verify that the admin user is a member------
AccountType Caption Domain SID FullName Name
----------- ------- ------ --- -------- ----
512 TEST10\Administrato TEST10 S-1-5-21-3672446222-1547575315-356276567-500 Administrato
512 TEST10\Admin TEST10 S-1-5-21-3672446222-1547575315-356276567-1001 Admin
Hopefully that resolves the issue of "I don't want to run winrm quickconfig". Is your testing successful?
When you run that script using the Administrator account, does it show that the Admin user is a member of the group?

