A good option would be to enable Azure Identity Protection, which allows you to configure sign-in risk policies and user risk policies to target risky users and risky sign-ins. The recommended sign-in policy is to target medium risk sign-ins and require MFA. For User policies it should target high risk users requiring the password change action. Administrators can make a decision based on the risk score signal to enforce organizational requirements. Administrators can choose to block access, allow access, or allow access but require a password change using Azure AD self-service password reset.
Identity Protection has built-in alerts for leaked credentials already, so would be perfect. Credentials are processed immediately after they have been found and deleted shortly after.
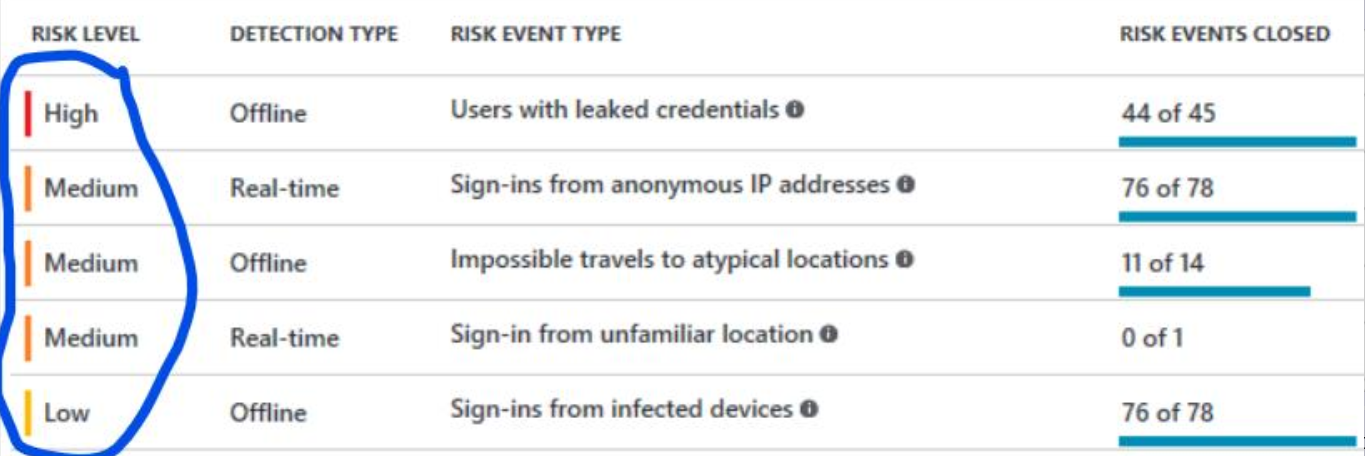
Leaked credentials are classified as "high risk" so would be captured in the risk policies.
Another good option for you would be to enable Azure AD Smart Lockout. Smart lockout can recognize sign-ins that come from valid users and treat them differently than ones of attackers and other unknown sources. Attackers get locked out, while your users continue to access their accounts. Smart lockout will block users after a configurable number of failed sign-in attempts.
The article Rapidly respond to secure identities with Azure AD lists a number of resources that would be useful for your scenario.
If you want want something even more custom to disable accounts you can probably set up something in Powershell using Disable-ADAccount
Hope this helps!