Hello
We have a problem with RDP service on Windows VMs running on our VxRail cluster.
For some reason, RDP stops working properly and when you try to connect to the VM via RDP, you receive the following error message:
=================================
Remote Desktop Connection
Remote Desktop can't connect to the remote computer for one of these reasons:
- Remote access to the server is not enabled
- The remote computer is turned off
- The remote computer is not available on the network Make sure the remote computer is turned on and connected to the network, and that remote access is enabled.
=================================
When problem is present, the service is running in OS, but when using the "netstat" command, it shows that the server is not listening on port 3389.
To recover, we have two options:
- Reboot affected VM
- Log in to the VM via vCenter Server console, and restart RDP service.
This is taking approx. 20 minutes to complete and we get a following error when service is stopping (screenshot attached) 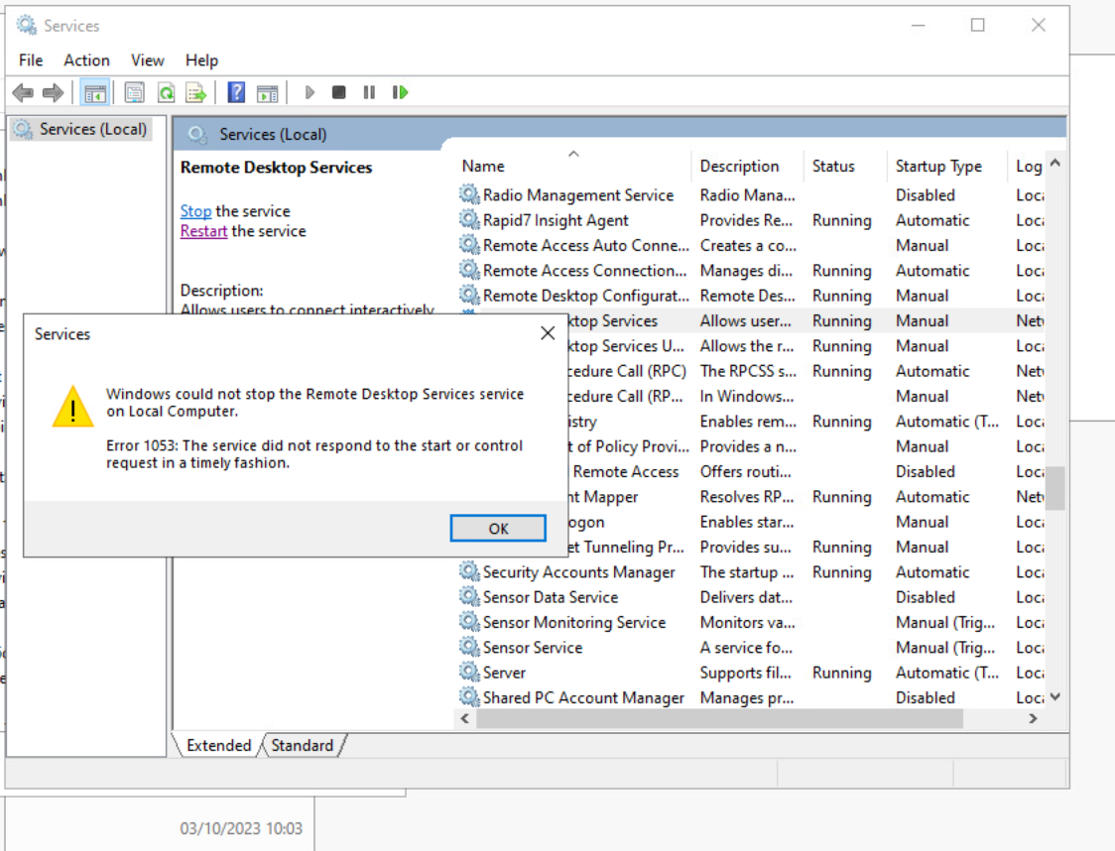
This problems happens a few times per week for each VM, so it means we get several warnings per day.
We can't afford to restart production servers so often, and manually restarting RDP takes time...
VxRail Version: 7.0.452-28152920 (ESXi version: 7.0.3, 21930508)
VMware Tools version 12.3.0.22234872 (but this problem was also observed when running on older versions)
Affected OS version: Windows Server 2022 (We have a few Win 2019 machines and they don't seem to have this problem. We have also several Win 10 VDIs and they don't have this problem either).
Affected VMs: All VMs with Win 2022 seems to be affected.
VMware support checked this issue and asked to engage Microsoft as they do not see any problems with VMware infrastructure.
Any suggestions would be greatly appreciated.

