Hello everyone!
Preface:
I’m in a process of setting up a test / demo environment to our development team. This test network must include and utilize among other servers and services a working 3 tier PKI topology. For this purpose I’m using the “Best Practices for Implementing a Microsoft Windows Server 2003 Public Key Infrastructure” white paper. I’m using Windows Server 2019 Datacenter editions for all servers’ operating system.
The process done so far:
I’m following the whitepaper, and I’m done with “Example Scenario for Contoso” chapter to install and configure the Stand-alone Offline Root CA.
I have also finished the “Stand-alone Offline Intermediate CA (IntermediateCA1)” chapter. At this point everything seems fine.
I’m skipping the “CorporateSub2CA” installation, because it will be not needed for our testing purposes.
Currently I’m at the “Import ParentCA Certificates and CRLs into Active Directory” section of the Online Enterprise Issuing CAs (CorporateEnt1CA) chapter.
The problem:
I got the following result:

- Figure My result: Failed download from CDP
2. Figure My result: Failed download from AIA
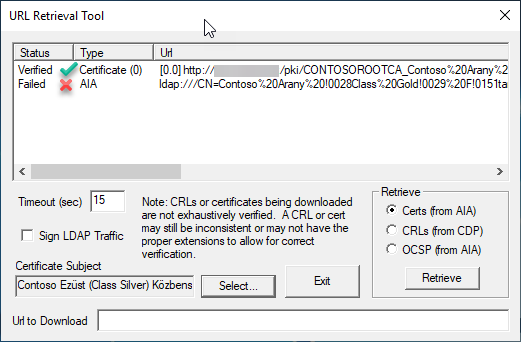
Although I should get the following result, if I complete the steps in this chapter:

3. Figure “Figure 8: URL Retrival Tool” - from the white paper
I Created a copy from the Default Domain Policy and added the RootCA’s certificate to the Trusted Root Certification Authorities and the IntermediateCA’s certificate to the Intermediate Certification Authorities.
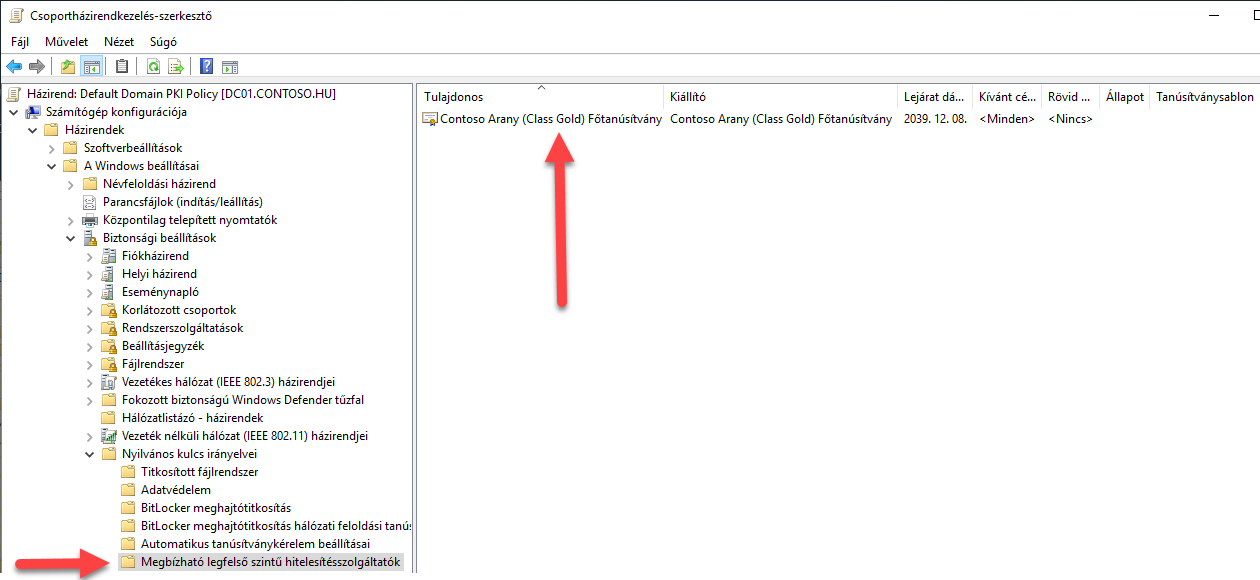
4. Figure GPO setting for RootCA’s cert distribution
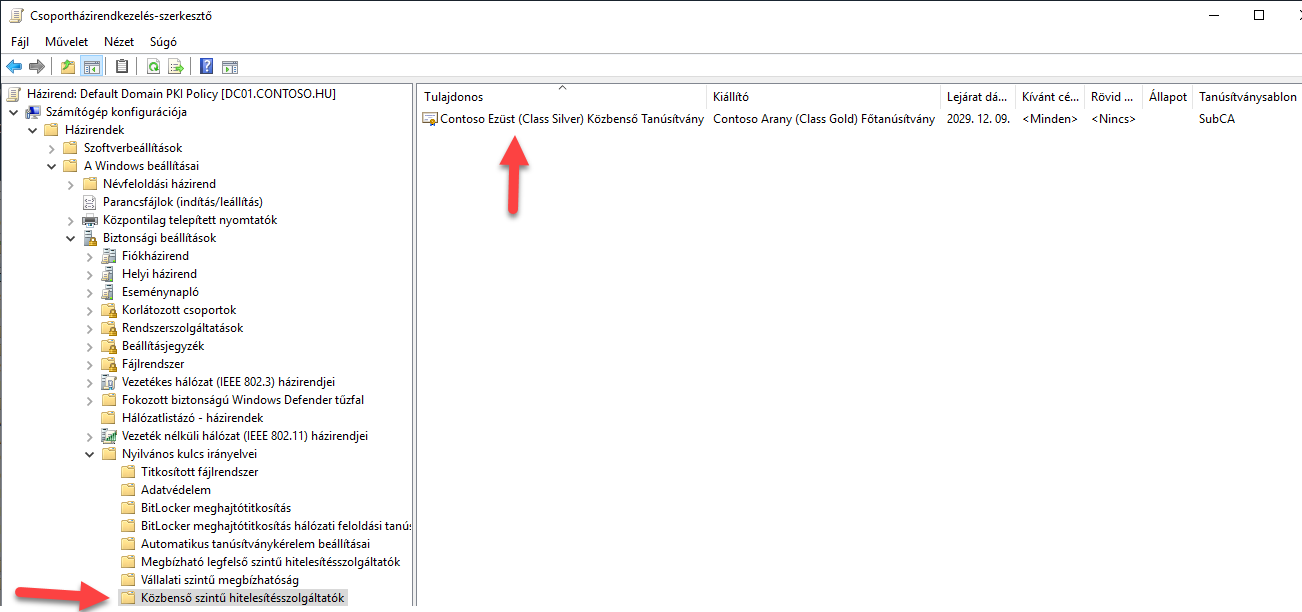
5. Figure GPO setting for intermediate CA's cert distribution
I ran the following commands:
PS C:\Users\Rendszergazda\Documents> certutil -f -dspublish '.\CONTOSOROOTCA_Contoso Arany !0028Class Gold!0029 F!0151tan!00fas!00edtv!00e1ny.crt'
ldap:///CN=Contoso Arany !0028Class Gold!0029 F!0151tan!00fas-49548,CN=Certification Authorities,CN=Public Key Services,CN=Services,CN=Configuration,DC=contoso,DC=hu?cACertificate
Certificate already in DS store.
ldap:///CN=Contoso Arany !0028Class Gold!0029 F!0151tan!00fas-49548,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=contoso,DC=hu?cACertificate
Certificate already in DS store.
CertUtil: -dsPublish command completed successfully.
PS C:\Users\Rendszergazda\Documents> certutil -f -dspublish '.\CONTOSOINTCA1_Contoso Ez!00fcst !0028Class Silver!0029 K!00f6zbens!0151 Tan!00fas!00edtv!00e1ny.crt'
ldap:///CN=Contoso Ez!00fcst !0028Class Silver!0029 K!00f6zben-35707,CN=AIA,CN=Public Key Services,CN=Services,CN=Configuration,DC=contoso,DC=hu?cACertificate
Certificate already in DS store.
CertUtil: -dsPublish command completed successfully.
PS C:\Users\Rendszergazda\Documents> certutil -f -dspublish '.\Contoso Arany !0028Class Gold!0029 F!0151tan!00fas!00edtv!00e1ny.crl' contosorootca
ldap:///CN=Contoso Arany !0028Class Gold!0029 F!0151tan!00fas-49548,CN=contosorootca,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=contoso,DC=hu?certificateRevocationList
Base CRL already in DS store.
CertUtil: -dsPublish command completed successfully.
PS C:\Users\Rendszergazda\Documents> certutil -f -dspublish '.\Contoso Ez!00fcst !0028Class Silver!0029 K!00f6zbens!0151 Tan!00fas!00edtv!00e1ny.crl' contosointca1
ldap:///CN=Contoso Ez!00fcst !0028Class Silver!0029 K!00f6zben-35707,CN=contosointca1,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=contoso,DC=hu?certificateRevocationList
Base CRL added to DS store.
CertUtil: -dsPublish command completed successfully.
After these commands, I checked the AD DS console for the AIA and CDP nodes:
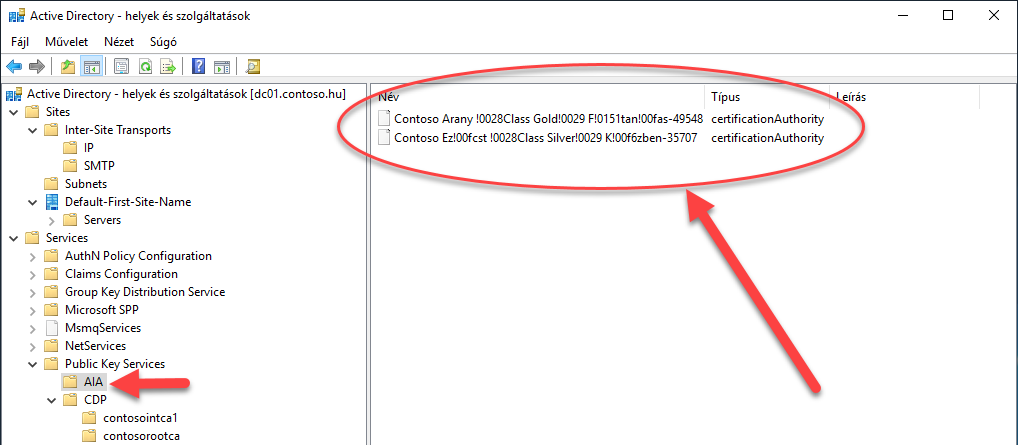
6. Figure The AIA node contains the two Certification Authority
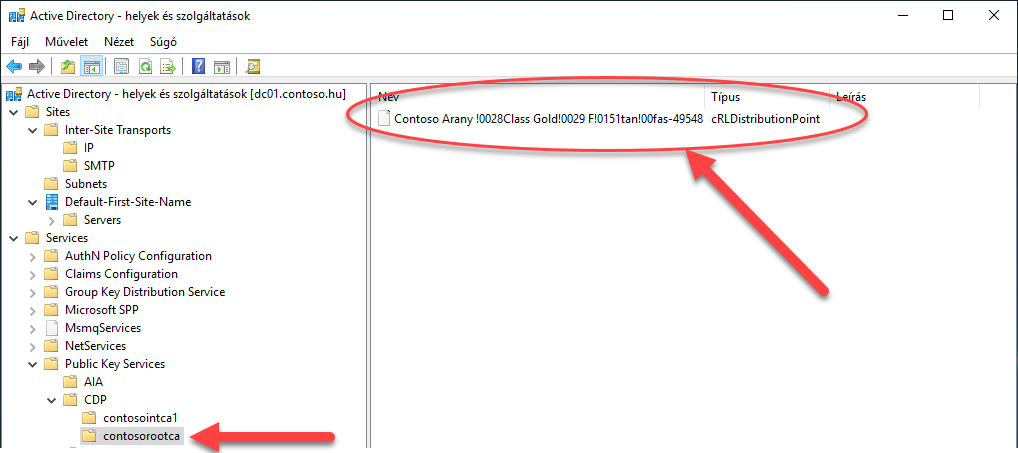
7. Figure The RootCAs' CRL Distribution Point
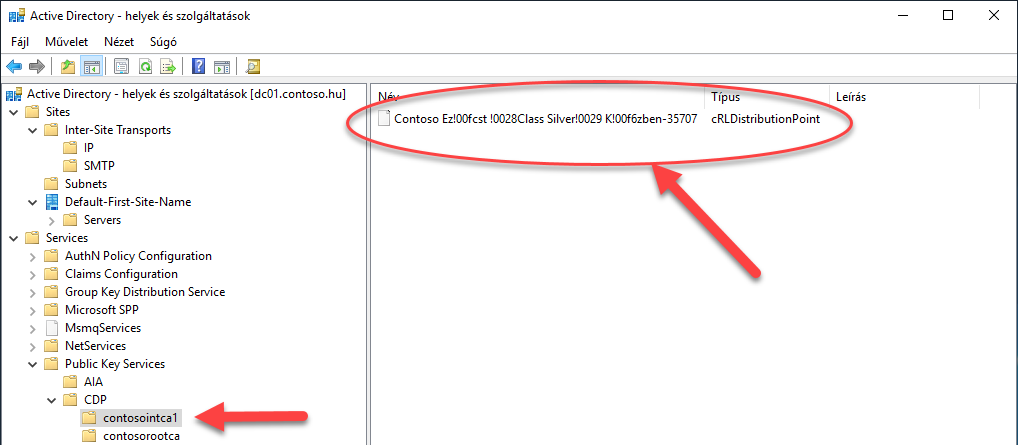
8. Figure The Intermediate CAs' CRL Distribution Point
Here is the intermediate CAs’ certutil.exe -urlfetch -verify output:
PS C:\Users\Rendszergazda\Documents> certutil.exe -urlfetch -verify '.\CONTOSOINTCA1_Contoso Ez!00fcst !0028Class Silver!0029 K!00f6zbens!0151 Tan!00fas!00edtv!00e1ny.crt'
Issuer:
CN=Contoso Arany (Class Gold) Főtanúsítvány
DC=contosorootca
DC=contoso
DC=hu
OU=Tanúsítványkiadók (Certification Services)
O=Contoso Kft.
L=Budapest
C=HU
Name Hash(sha1): 81902e03b1bda55156c42f55123d5067552fd41e
Name Hash(md5): 0477e38ad67ae0ec046950a5acb7f985
Subject:
CN=Contoso Ezüst (Class Silver) Közbenső Tanúsítvány
OU=Tanúsítványkiadók (Certification Services)
O=Contoso Kft.
L=Budapest
DC=contosointca1
DC=contoso
DC=hu
C=HU
Name Hash(sha1): 7086737ac01a7fb916796b4c29399e1c2620d2c0
Name Hash(md5): 6031e780d142a025573bfd052a54dff6
Cert Serial Number: 280000000216e88751d5893e67000000000002
dwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)
dwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)
ChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN_EXCLUDE_ROOT (0x40000000)
HCCE_LOCAL_MACHINE
CERT_CHAIN_POLICY_BASE
-------- CERT_CHAIN_CONTEXT --------
ChainContext.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
ChainContext.dwRevocationFreshnessTime: 61 Days, 25 Minutes, 53 Seconds
SimpleChain.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
SimpleChain.dwRevocationFreshnessTime: 61 Days, 25 Minutes, 53 Seconds
CertContext[0][0]: dwInfoStatus=102 dwErrorStatus=0
Issuer: CN=Contoso Arany (Class Gold) Főtanúsítvány, DC=contosorootca, DC=contoso, DC=hu, OU=Tanúsítványkiadók (Certification Services), O=Contoso Kft., L=Budapest, C=HU
NotBefore: 2019. 12. 09. 17:15
NotAfter: 2029. 12. 09. 17:25
Subject: CN=Contoso Ezüst (Class Silver) Közbenső Tanúsítvány, OU=Tanúsítványkiadók (Certification Services), O=Contoso Kft., L=Budapest, DC=contosointca1, DC=contoso, DC=hu, C=HU
Serial: 280000000216e88751d5893e67000000000002
Template: SubCA
Cert: 64084ec5ddcaea610182ca37f3344d13be037fd2
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
Verified "Certificate (0)" Time: 0 b7263457736504319e1da84b24bea1aff84b98da
[0.0] http://***.******.***/pki/CONTOSOROOTCA_Contoso%20Arany%20!0028Class%20Gold!0029%20F!0151tan!00fas!00edtv!00e1ny.crt
Failed "AIA" Time: 0 (null)
Error retrieving URL: A rendszer nem találja a megadott fájlt. 0x80070002 (WIN32: 2 ERROR_FILE_NOT_FOUND)
ldap:///CN=Contoso%20Arany%20!0028Class%20Gold!0029%20F!0151tan!00fas-49548,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=contosorootca,DC=contoso,DC=hu?cACertificate?base?objectClass=certificationAuthority
---------------- Certificate CDP ----------------
Verified "Base CRL (06)" Time: 0 dd934cbbb2449f22b40baa68960db8d1e9e22033
[0.0] http://***.******.***/pki/Contoso%20Arany%20!0028Class%20Gold!0029%20F!0151tan!00fas!00edtv!00e1ny.crl
Failed "CDP" Time: 0 (null)
Error retrieving URL: A rendszer nem találja a megadott fájlt. 0x80070002 (WIN32: 2 ERROR_FILE_NOT_FOUND)
ldap:///CN=Contoso%20Arany%20!0028Class%20Gold!0029%20F!0151tan!00fas-49548,CN=CONTOSOROOTCA,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=contosorootca,DC=contoso,DC=hu?certificateRevocationList?base?objectClass=cRLDistributionPoint
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0 (null)
--------------------------------
CRL 06:
Issuer: CN=Contoso Arany (Class Gold) Főtanúsítvány, DC=contosorootca, DC=contoso, DC=hu, OU=Tanúsítványkiadók (Certification Services), O=Contoso Kft., L=Budapest, C=HU
ThisUpdate: 2020. 09. 01. 14:42
NextUpdate: 2021. 09. 02. 3:02
CRL: dd934cbbb2449f22b40baa68960db8d1e9e22033
CertContext[0][1]: dwInfoStatus=10c dwErrorStatus=0
Issuer: CN=Contoso Arany (Class Gold) Főtanúsítvány, DC=contosorootca, DC=contoso, DC=hu, OU=Tanúsítványkiadók (Certification Services), O=Contoso Kft., L=Budapest, C=HU
NotBefore: 2019. 12. 08. 22:38
NotAfter: 2039. 12. 08. 22:48
Subject: CN=Contoso Arany (Class Gold) Főtanúsítvány, DC=contosorootca, DC=contoso, DC=hu, OU=Tanúsítványkiadók (Certification Services), O=Contoso Kft., L=Budapest, C=HU
Serial: 258d42a413a714884737f0cb909f9207
Cert: b7263457736504319e1da84b24bea1aff84b98da
Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)
Element.dwInfoStatus = CERT_TRUST_IS_SELF_SIGNED (0x8)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate CDP ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0 (null)
--------------------------------
Exclude leaf cert:
Chain: b048fa5fe1a3e410f77f5881e714aaa9eb403216
Full chain:
Chain: f002a6b69975f9ca3411ac1fd74839f6c38f6b8e
------------------------------------
Verified Issuance Policies: All
Verified Application Policies: All
Cert is a CA certificate
Leaf certificate revocation check passed
CertUtil: -verify command completed successfully.
So, this is the story so far.
Can anyone give me any idea how to solve this problem? I have no clue.









