A bit of context: My goal is to have an app running on Azure that will eventually access SharePoint sites in different tenants. The idea is that once authorized, this app will connect to all tenants using the same app id and secret. A multi-tenant app.
With that said, when I try to use the GraphServiceClient to connect to a SharePoint site I get the following error: Either scp or roles claim need to be present in the token.
For now, all tests are being conducted in the same tenant where the app registration was created.
Here is the code:
var clientId = "[MY_APP_ID]]";
var secret = "[MY_APP_SECRET]";
var tenantId = "common";
var scopes = new[] { "https://graph.microsoft.com/.default" };
var sharePointSiteId = "[SHAREPOINT_SITE_ID]";
var options = new ClientSecretCredentialOptions
{
AuthorityHost = AzureAuthorityHosts.AzurePublicCloud
};
var clientSecretCredential = new ClientSecretCredential(tenantId, clientId, secret, options);
// this was just a test, we do get a token back
var accessToken = await clientSecretCredential.GetTokenAsync(new TokenRequestContext(scopes));
var graphClient = new GraphServiceClient(clientSecretCredential, scopes);
// this line will throw this error:
// Either scp or roles claim need to be present in the token.
var drives = await graphClient.Sites[sharePointSiteId].Drives.GetAsync();
// this is just for testing purposes since our goal is SharePoint
// if I comment the previous line, this one will be reached
// and will throw the following error:
// The identity of the calling application could not be established.
var users = await graphClient.Users.GetAsync();
My setup:
The app is registered as a multi-tenant.
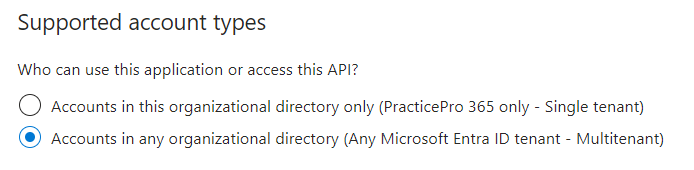
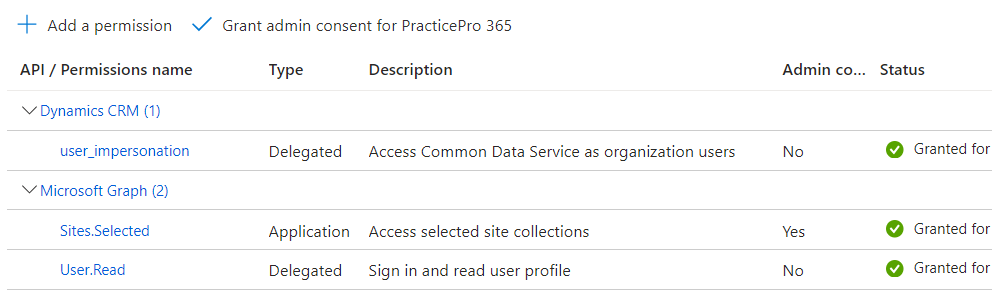
It has the following listed under API Permissions:
Once the app registration was done, I used the following link to get to grant consent (in an attempt to reproduce the steps from future users):
https://login.microsoftonline.com/[MY_TENANT_ID]/adminconsent?client_id=[MY_APP_ID]
I got the expected consent window and it appears to have worked well.
SharePoint Site Permissions
To grant the required permissions to the SharePoint site, I went to:
https://developer.microsoft.com/en-us/graph/graph-explorer
There, I changed to method to POST and used the following URL:
https://graph.microsoft.com/v1.0/sites/[MY_SITE_ID]/permissions
With the request body:
{
"roles": ["read","write"],
"grantedToIdentities": [{
"application": {
"id": "[APP_ID]",
"displayName": "[APP_DISPLAY_NAME]"
}
}]
}
Thanks in advance.
