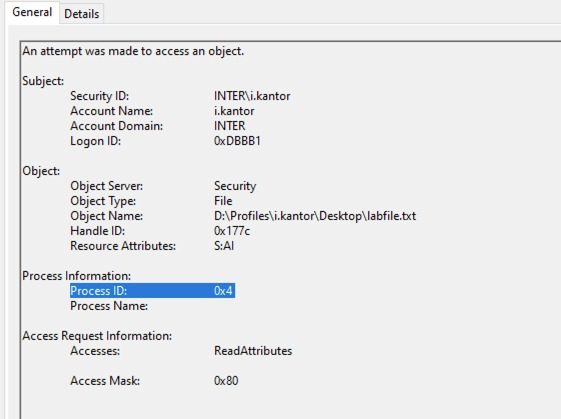
We have observed a consistent occurrence of process ID 0x4 in the event logs, particularly associated with Event ID 4663 (file and folder access auditing). Notably, this issue seems to occur exclusively with Active Directory accounts. Despite efforts to configure the system to run all programs as user-level processes, the process IDs in the event logs remain at 0x4, indicating system-level processes.
It doesn't depend which program was launched (administrator/user permissions) - in every log there is 0x4 instead of real process ID.
There should be real process ID as in Task Manager or in the 4689 event (Process Termination).
In local users it appears how it's supposed to.
Steps Taken: We have undertaken the following steps in an attempt to resolve the issue:
- Modified the "User Account Control: Run all administrators in Admin Approval Mode" policy to "Disabled" to ensure that administrators run with the full administrative token.
- Checked and adjusted service accounts, scheduled tasks, and programs to run under specific user accounts rather than system accounts.
- Verified audit settings and logon types to ensure proper configuration for capturing user-level process information.
- Reviewed other security policies that might affect process identification and access auditing.
- Considered enabling Advanced Auditing features to provide more granular control over auditing settings.
These configurations were applied through Group Policy Objects (GPOs) to ensure consistency across the domain.
Version of the Windows: Windows Server 2022, latest updates.
Please tell me how to fix it to receive real process ID instead of 0x4 with Event ID 4663 on domain users