@Martinez, Ernie
@Martinez, Ernie
Thank you for posting your query on Microsoft Q&A, from above description I could understand that you are looking for advice on logging onto Azure VM with On-prem account.
Please do correct me if this is not the ask by responding in the comments section:
PFB steps to access your VM with on-prem credentials:
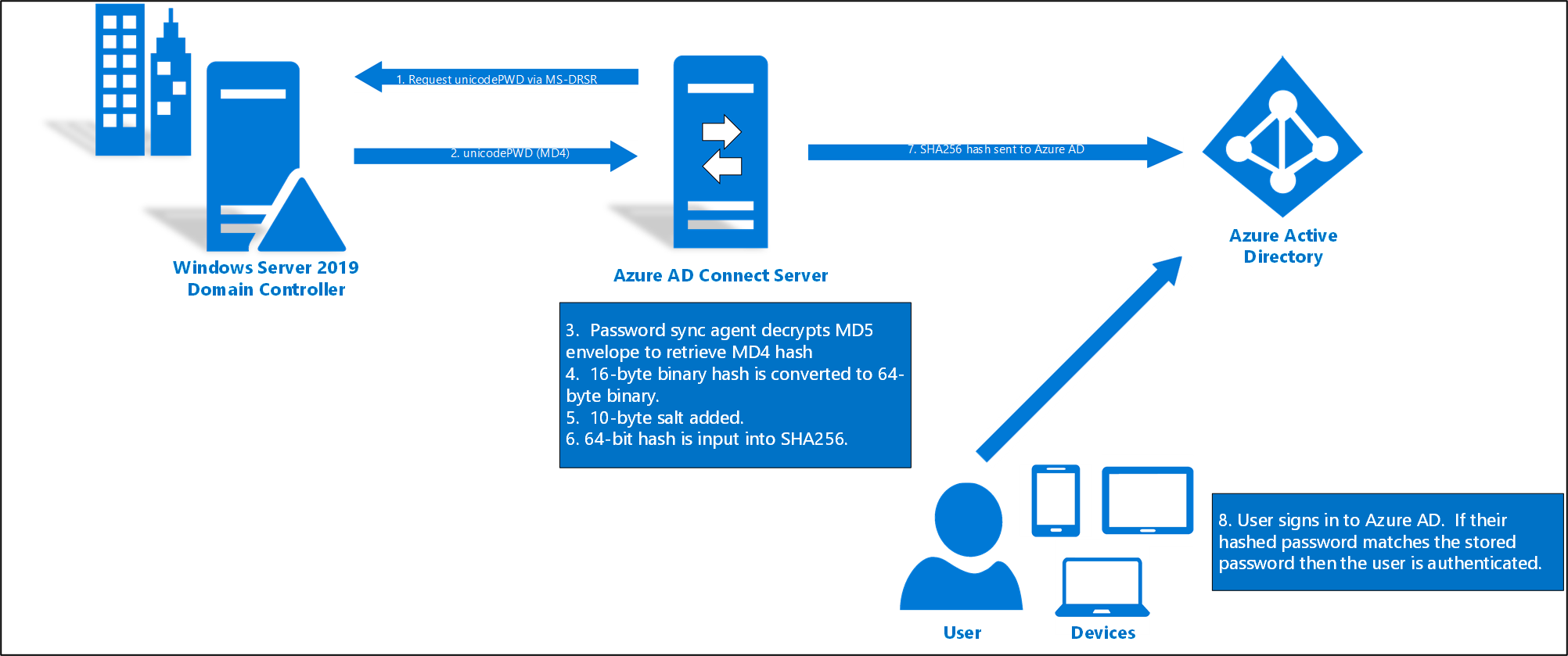
- Every two minutes, the password hash synchronization agent on the AD Connect server requests stored password hashes (the unicodePwd attribute) from a DC. This request is via the standard MS-DRSR replication protocol used to synchronize data between DCs. The service account must have Replicate Directory Changes and Replicate Directory Changes All AD permissions (granted by default on installation) to obtain the password hashes.
- Before sending, the DC encrypts the MD4 password hash by using a key that is a MD5 hash of the RPC session key and a salt. It then sends the result to the password hash synchronization agent over RPC. The DC also passes the salt to the synchronization agent by using the DC replication protocol, so the agent will be able to decrypt the envelope.
- After the password hash synchronization agent has the encrypted envelope, it uses MD5CryptoServiceProvider and the salt to generate a key to decrypt the received data back to its original MD4 format. The password hash synchronization agent never has access to the clear text password. The password hash synchronization agent’s use of MD5 is strictly for replication protocol compatibility with the DC, and it is only used on-premises between the DC and the password hash synchronization agent.
- The password hash synchronization agent expands the 16-byte binary password hash to 64 bytes by first converting the hash to a 32-byte hexadecimal string, then converting this string back into binary with UTF-16 encoding.
- The password hash synchronization agent adds a per user salt, consisting of a 10-byte length salt, to the 64-byte binary to further protect the original hash.
- The password hash synchronization agent then combines the MD4 hash plus the per user salt, and inputs it into the PBKDF2 function. 1000 iterations of the HMAC-SHA256 keyed hashing algorithm are used. For additional details, refer to the Microsoft Entra Whitepaper.
- The password hash synchronization agent takes the resulting 32-byte hash, concatenates both the per user salt and the number of SHA256 iterations to it (for use by Microsoft Entra ID), then transmits the string from Microsoft Entra Connect to Microsoft Entra ID over TLS.
- When a user attempts to sign in to Microsoft Entra ID and enters their password, the password is run through the same MD4+salt+PBKDF2+HMAC-SHA256 process. If the resulting hash matches the hash stored in Microsoft Entra ID, the user has entered the correct password and is authenticated.
To use Microsoft Entra login for a Windows VM in Azure, you must:
- Enable the Microsoft Entra login option for the VM.
- Configure Azure role assignments for users who are authorized to log in to the VM.
There are two ways to enable Microsoft Entra login for your Windows VM:
- The Azure portal, when you're creating a Windows VM.
- Azure Cloud Shell, when you're creating a Windows VM or using an existing Windows VM.
You can enable Microsoft Entra login for VM images in Windows Server 2019 Datacenter or Windows 10 1809 and later.
- To create a Windows Server 2019 Datacenter VM in Azure with Microsoft Entra login:
- Sign in to the Azure portal by using an account that has access to create VMs, and select + Create a resource.
- In the Search the Marketplace search bar, type Windows Server.
- Select Windows Server, and then choose Windows Server 2019 Datacenter from the Select a software plan dropdown list.
- Select Create.
- On the Management tab, select the Login with Microsoft Entra ID checkbox in the Microsoft Entra ID section.
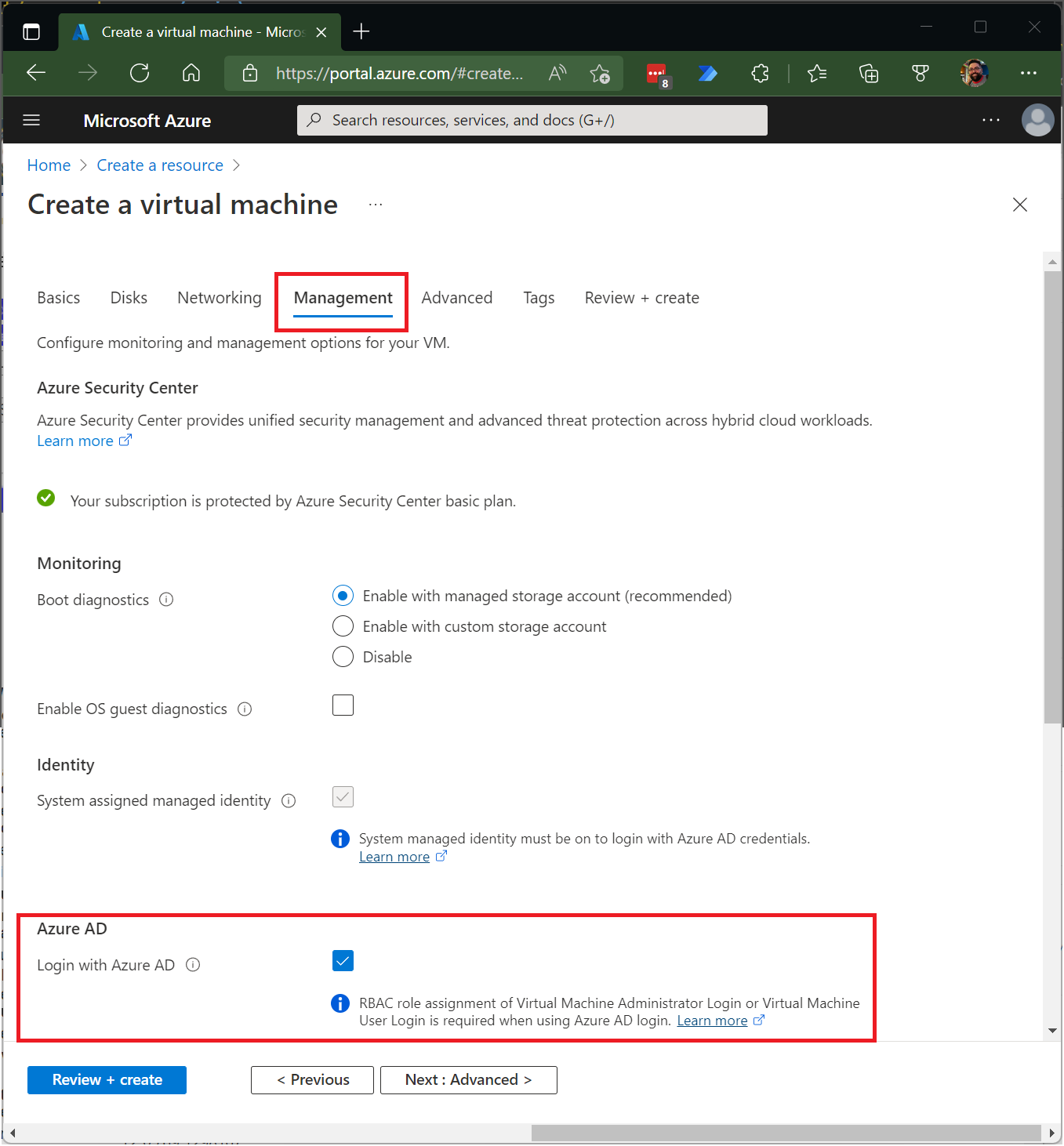
- Screenshot that shows the Management tab on the Azure portal page for creating a virtual machine.
- Make sure that System assigned managed identity in the Identity section is selected. This action should happen automatically after you enable login with Microsoft Entra ID.
- Go through the rest of the experience of creating a virtual machine. You have to create an administrator username and password for the VM.
Please "Accept the answer (Yes)" and "share your feedback ". This will help us and others in the community as well.
Thanks,
Akshay Kaushik

