
Hi @prunyan ,
Right now you have to disable registration methods both in the MFA settings and in the SSPR settings. User do not have an option to register for MFA using email, but they can do SSPR with email. To disable email as a method for SSPR, you just need to go to Azure Active Directory > Password reset > uncheck email as an option.
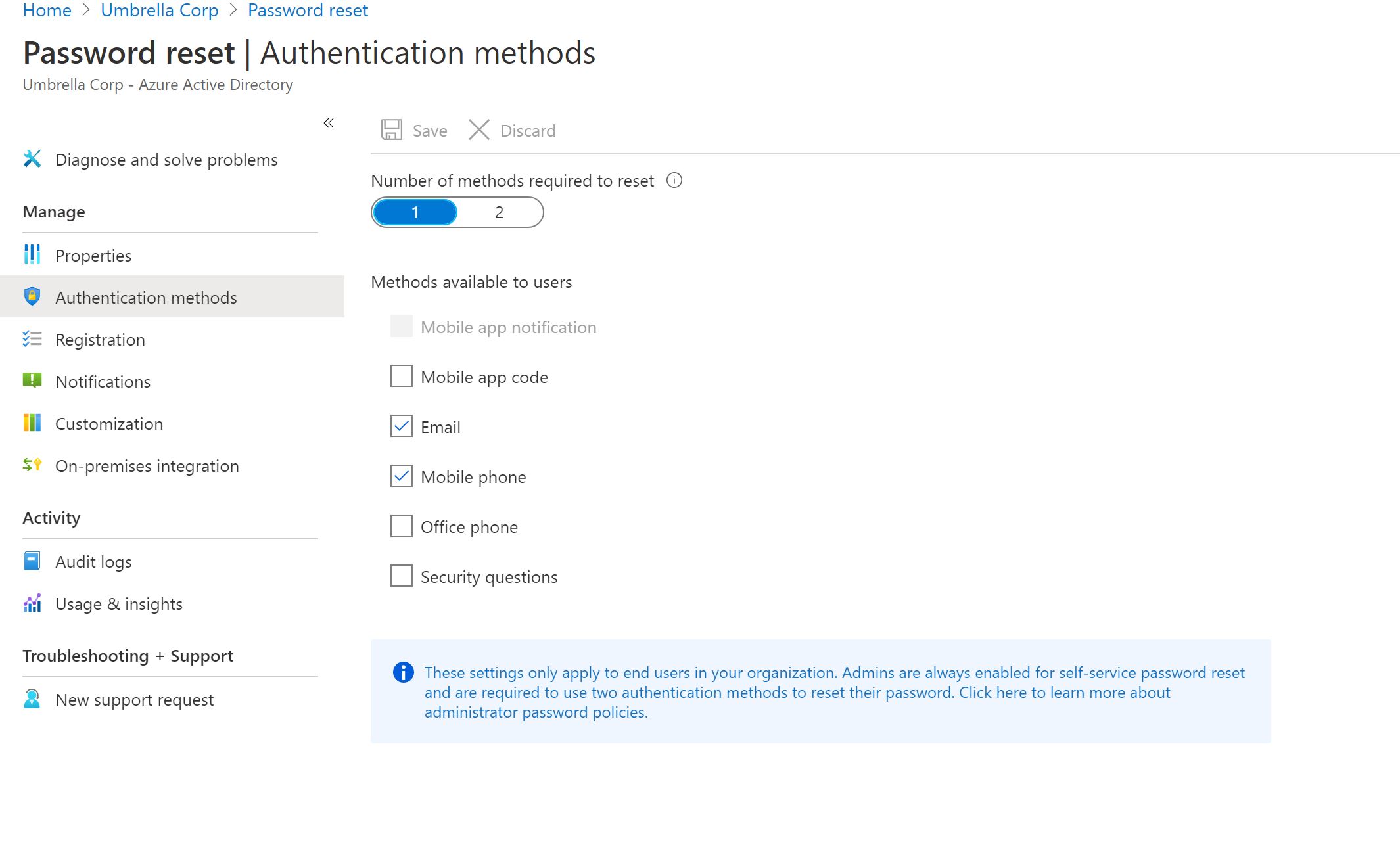
If you are using B2B you can manage users' MFA methods in the MFA settings.
To enable or disable verification methods, complete the following steps:
In the Azure portal, search for and select Azure Active Directory, then choose Users.
Select Multi-Factor Authentication.
Under Multi-Factor Authentication, select service settings.
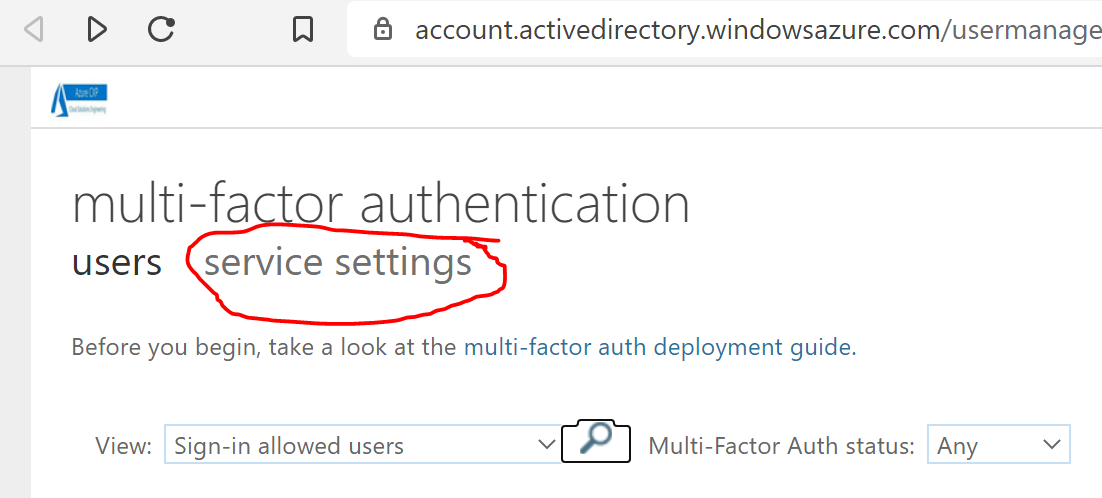
On the Service Settings page, under verification options, select/unselect the methods to provide to your users.

Click Save.
https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userdevicesettings
Right now there is no option to disable office phone registration, but this is something the product team is aware of and working on. There will be an option for this released soon, and you can track the feature request here: https://feedback.azure.com/forums/169401-azure-active-directory/suggestions/37147648-there-should-be-an-option-to-disable-office-phone
Hope this helps!
