
Hi,
As you mentioned above, it is required to provide a file if you use the Hash Rule on the Software Restriction Policies .
Here is a test in my environment:
I new a path role on the n the Software Restriction Policies and put the name only into the path as following:
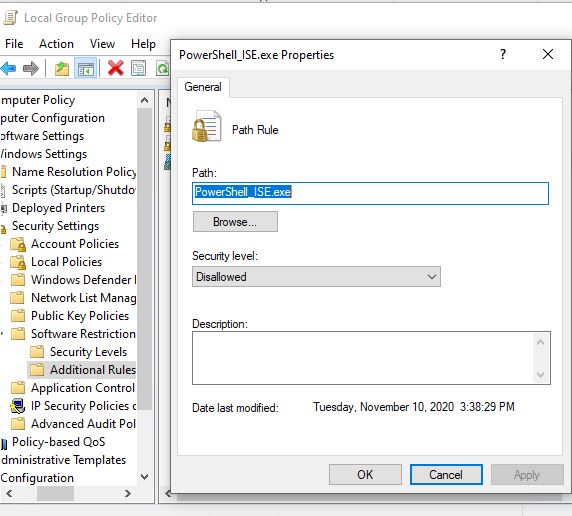
After i updated the policy with command :gpupdate /force , it worked.
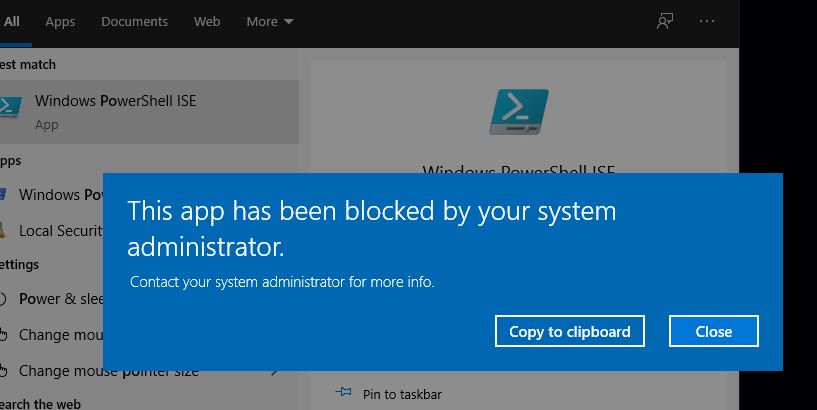
If you know the name and the file type of the malicious file, it may worth a try.
Best Regards,