Hi @Goeman Alex ,
Apologies for delay in response.
Yes, it is possible to add custom claim to a service principal using claim mapping policy.
Claim mapping policies are not user centric flow, we can add custom claim to application (service principal and get the claim in the token using client credential flow.
I have two App Registrations with APIs exposed by one and consumed by the other - call them "App1" and "App2" app registrations.
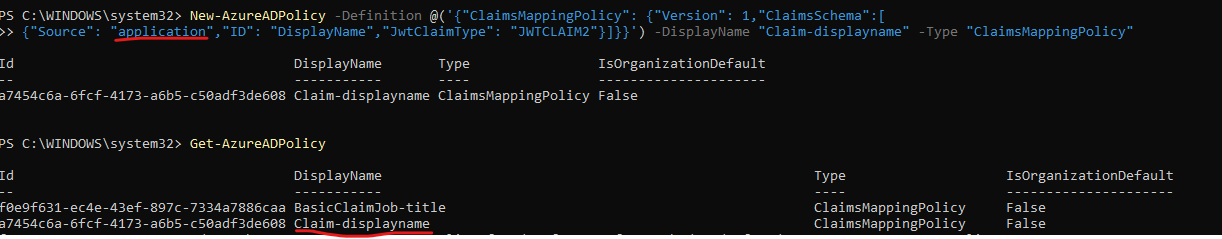
I added new custom policy as below:
1.New-AzureADPolicy -Definition @('{"ClaimsMappingPolicy": {"Version": 1,"ClaimsSchema":[
New-AzureADPolicy -Definition @('{"ClaimsMappingPolicy": {"Version": 1,"ClaimsSchema":[
{"Source": "application","ID": "DisplayName","JwtClaimType": "JWTCLAIM2"}]}}') -DisplayName "Claim-displayname" -Type "ClaimsMappingPolicy"
2.Get the Azure AD policy
3.Assign the custom claim to the object id of service principal of app2 to retrieve the custom data.
Add-AzureADServicePrincipalPolicy -Id <ObjectId of the ServicePrincipal> -RefObjectId <ObjectId of the Policy>
Make sure to set the acceptedMappedClaims to true in the manifest of your application.
You can get the token using client credential flow and can see your custom claim as
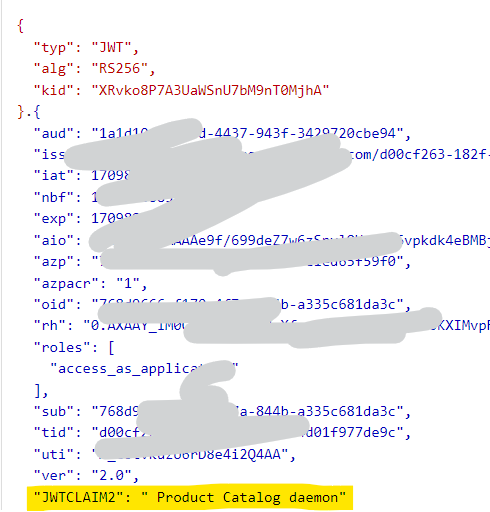
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.

