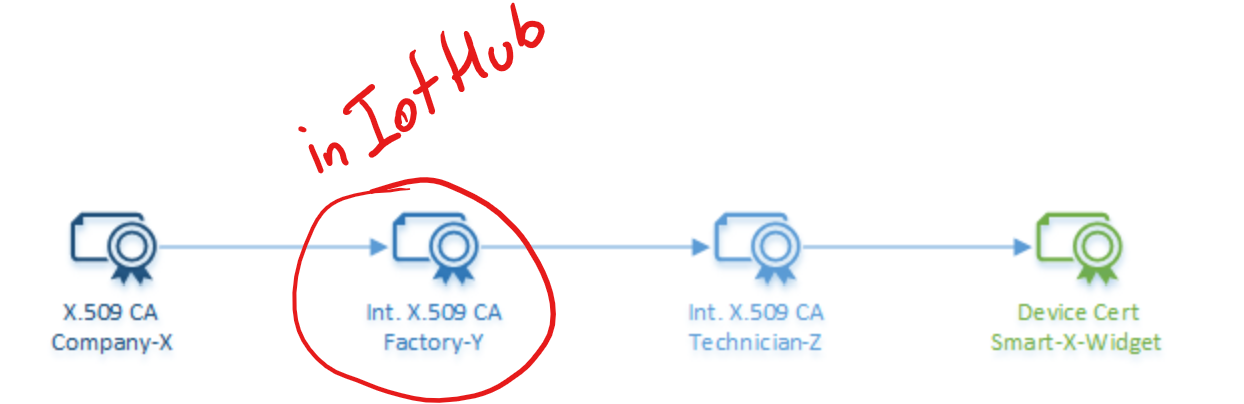
With the following steps I was able to create and validate a self-signed certificate.
Step 1. Generate 3 year X509 CA certificate with private key, see also: https://learn.microsoft.com/en-us/azure/iot-hub/iot-hub-security-x509-get-started#register-x509-ca-certificates-to-your-iot-hub
openssl req -x509 -newkey rsa:4096 -days 1095 -keyout ca-key.pem -nodes -out ca-cert.pem
Country Name (2 letter code) [AU]:<your country>
State or Province Name (full name) [Some-State]:<your state>
Locality Name (eg, city) []:<your city>
Organization Name (eg, company) [Internet Widgits Pty Ltd]:<your organisation name>
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:<e.g.Root CA>
Email Address []:<your e-mail address>
Step 2. Upload ca-cert.pem to Azure (IoT Hub)
Step 3. Generate verification code in Azure
Step 4. Generate verification key
openssl genrsa -out verification.key 2048
Step 5. Generate verification certificate request
openssl req -new -key verification.key -out verification.csr
The same information as above, except the common name must be the verification code from Azure IoT Hub!
Step 6. Generate proof of possession certificate
openssl x509 -req -in verification.csr -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out verificationCert.pem -days 1095 -sha256
Step 7. Upload verificationCert.pem to Azure (IoT Hub) and validate
Step 8. Generate device key
openssl genrsa -out <deviceID>-private.pem 2048
Replace <deviceID> with the device name from Azure IoT Hub, see also: https://learn.microsoft.com/en-us/azure/iot-hub/iot-hub-security-x509-get-started#create-an-x509-device-for-your-iot-hub
Step 9. Generate device certificate request
openssl req -new -key <deviceID>-private.pem -out <deviceID>.csr
The same information as above, except the common name must be the device name from Azure IoT Hub!
Step 10. Generate public certificate
openssl pkcs12 -export -in <deviceID>-public.pem -inkey <deviceID>-private.pem -out <deviceID>.pfx
I hope it helps others...
Michael