Hi Team,
We have added Mail.Send application permission in the app registraton and followed the below code to send email without using the sign in token from user. (its the code shared from MS team itself)
using Microsoft.Graph;
using Azure.Identity;
using Microsoft.Graph.Models;
using Microsoft.Graph.Users.Item.SendMail;
var scopes = new[] { "https://graph.microsoft.com/.default" };
var tenantId = "xxxxxxxxxxxxxxxxxxxxxxxxx";
// Values from app registration
var clientId = "xxxxxxxxxxxxxxxxxxxxxxxxxxx";
var clientSecret = "xxxxxxxxxxxxxxxxxxxxxxxxxx";
// using Azure.Identity;
var options = new TokenCredentialOptions
{
AuthorityHost = AzureAuthorityHosts.AzurePublicCloud
};
// https://learn.microsoft.com/dotnet/api/azure.identity.clientsecretcredential
var clientSecretCredential = new ClientSecretCredential(
tenantId, clientId, clientSecret, options);
var graphClient = new GraphServiceClient(clientSecretCredential, scopes);
var requestBody = new SendMailPostRequestBody
{
Message = new Message
{
Subject = "Meet for lunch?",
Body = new ItemBody
{
ContentType = BodyType.Text,
Content = "The new cafeteria is open.",
},
ToRecipients = new List<Recipient>
{
new Recipient
{
EmailAddress = new EmailAddress
{
Address = "xxxxxxxxxxxxxx",
},
},
},
CcRecipients = new List<Recipient>
{
new Recipient
{
EmailAddress = new EmailAddress
{
Address = "xxxxxxxxxxxxxxxx",
},
},
},
},
SaveToSentItems = false,
};
await graphClient.Users["xxxxxxxxxxxxxxxx"].SendMail.PostAsync(requestBody);
But I am not able to send email using the above code. We have upgraded the graph client package to the latest version.
Below are the error and exceptions i got when trying the above code,
I have tried with the object ID in the Entra for that specific user and got the below exception
One or more parameters of the operation 'sendMail' are missing from the request payload. The missing parameters are: Message.
Attached the permission that we have in the app registration we tried. We have added Mail.Send application permission and grant admin consent also . Still we are getting credentials invalid exceptions (Insufficient privileges to complete the operation) when we create client credentials in the above format (using the default scope).
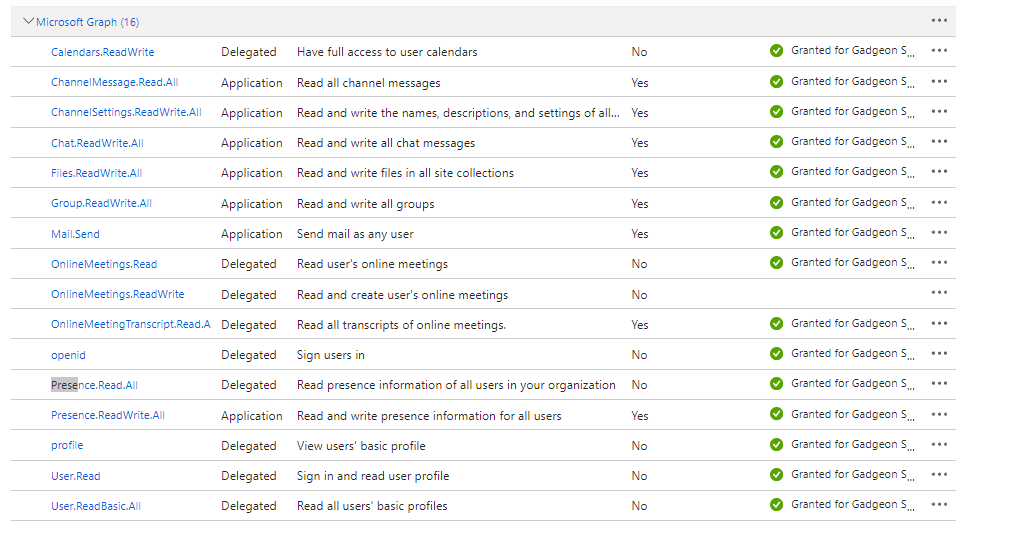
Also got the below error message while updating the scope as "Send.Mail,
ClientSecretCredential authentication failed: AADSTS1002012: The provided value for scope Mail.Send is not valid. Client credential flows must have a scope value with /.default suffixed to the resource identifier (application ID URI).
Can anyone help on this
