@Gert Vloo
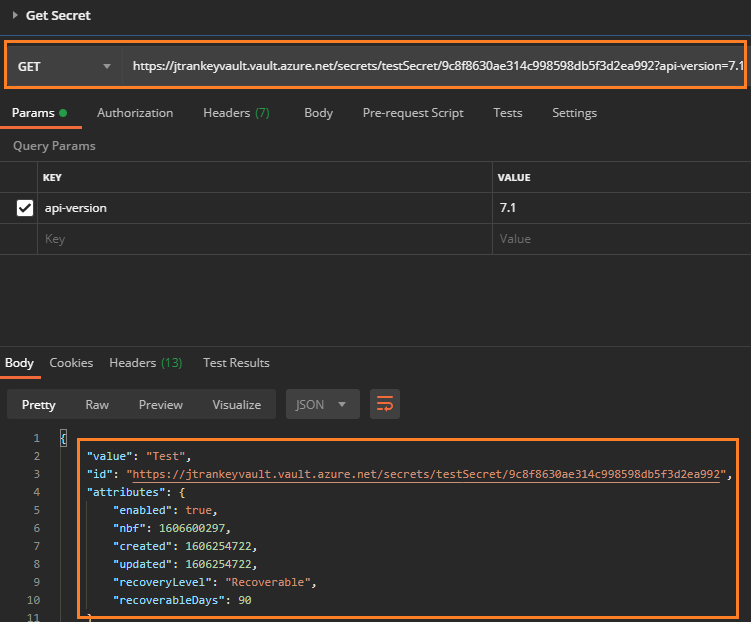
Thank you for your post! This is by design when using the Get Secret API, if the version isn't in the REST call then the latest version of the secret is returned.
If your secret isn't active until a certain date, but you enabled your secret, it'll have a "current version".
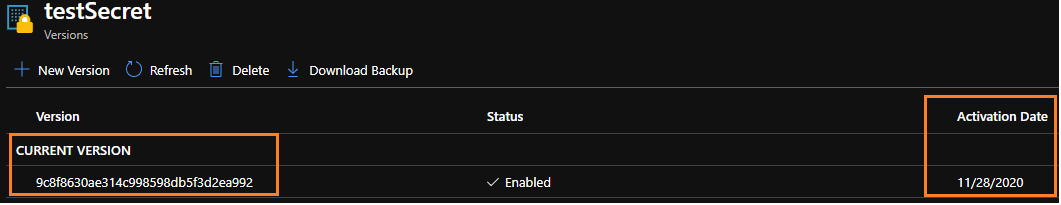
If your secret isn't enabled there won't be a current version since the API won't be able to retrieve the secret.
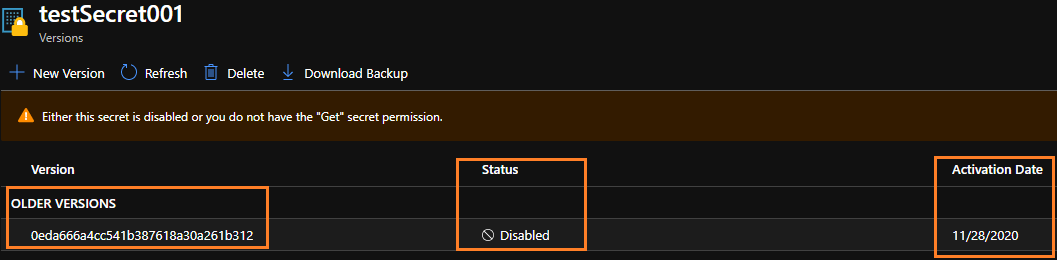
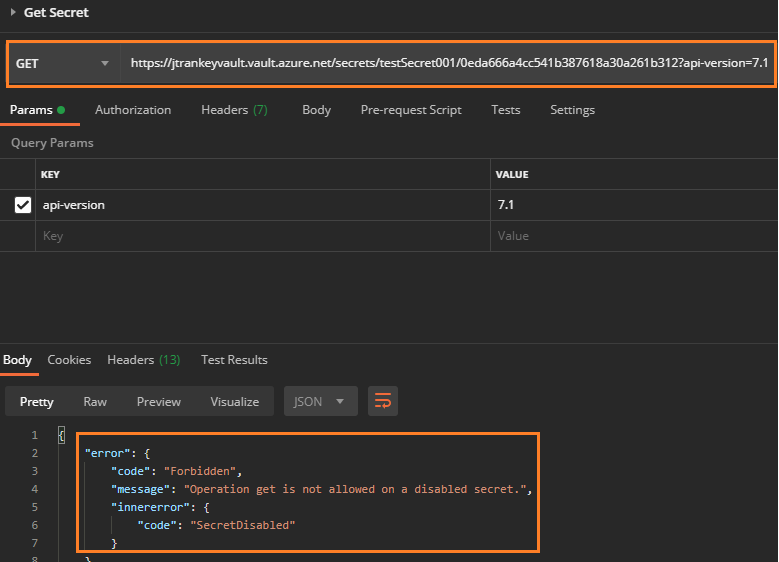
Unfortunately, none of the Secret REST APIs allow you to use the ActivationDate when getting your secrets. If you'd like this feature to be implemented, please feel free to leverage our User Voice forum.
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.


