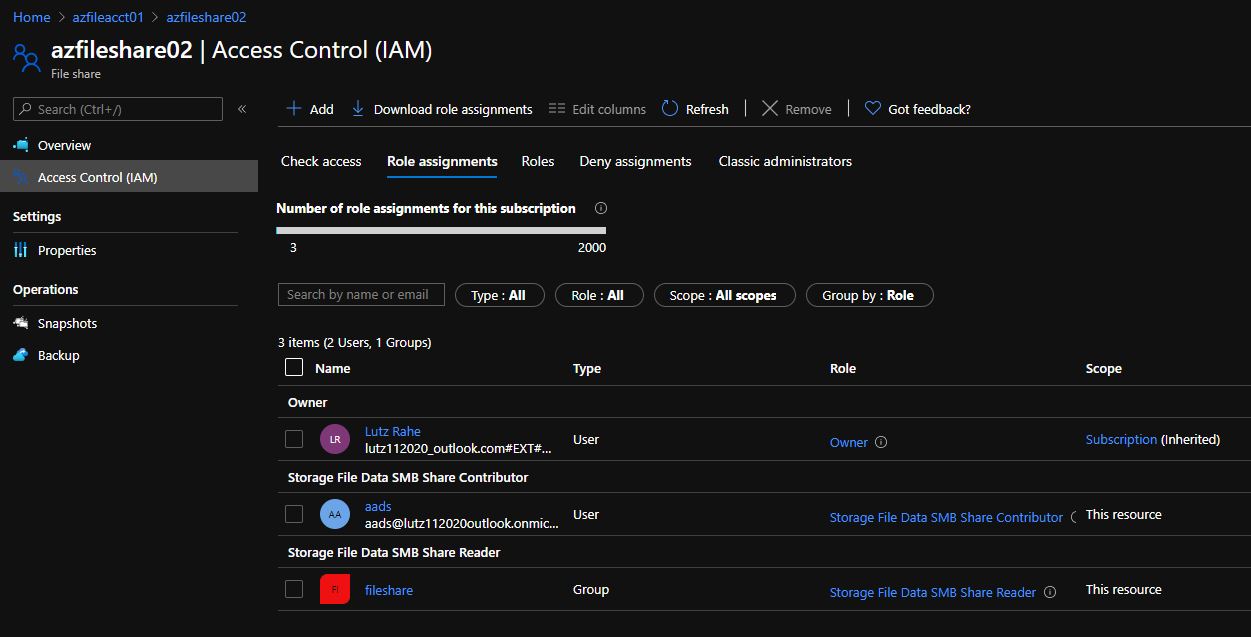
If the user for testing is member in the "fileshare" group he is only allowed to read content in the "azfileshare02" File Share.
The user is not allowed to write to the fileshare or modify the permissions of the File Share.
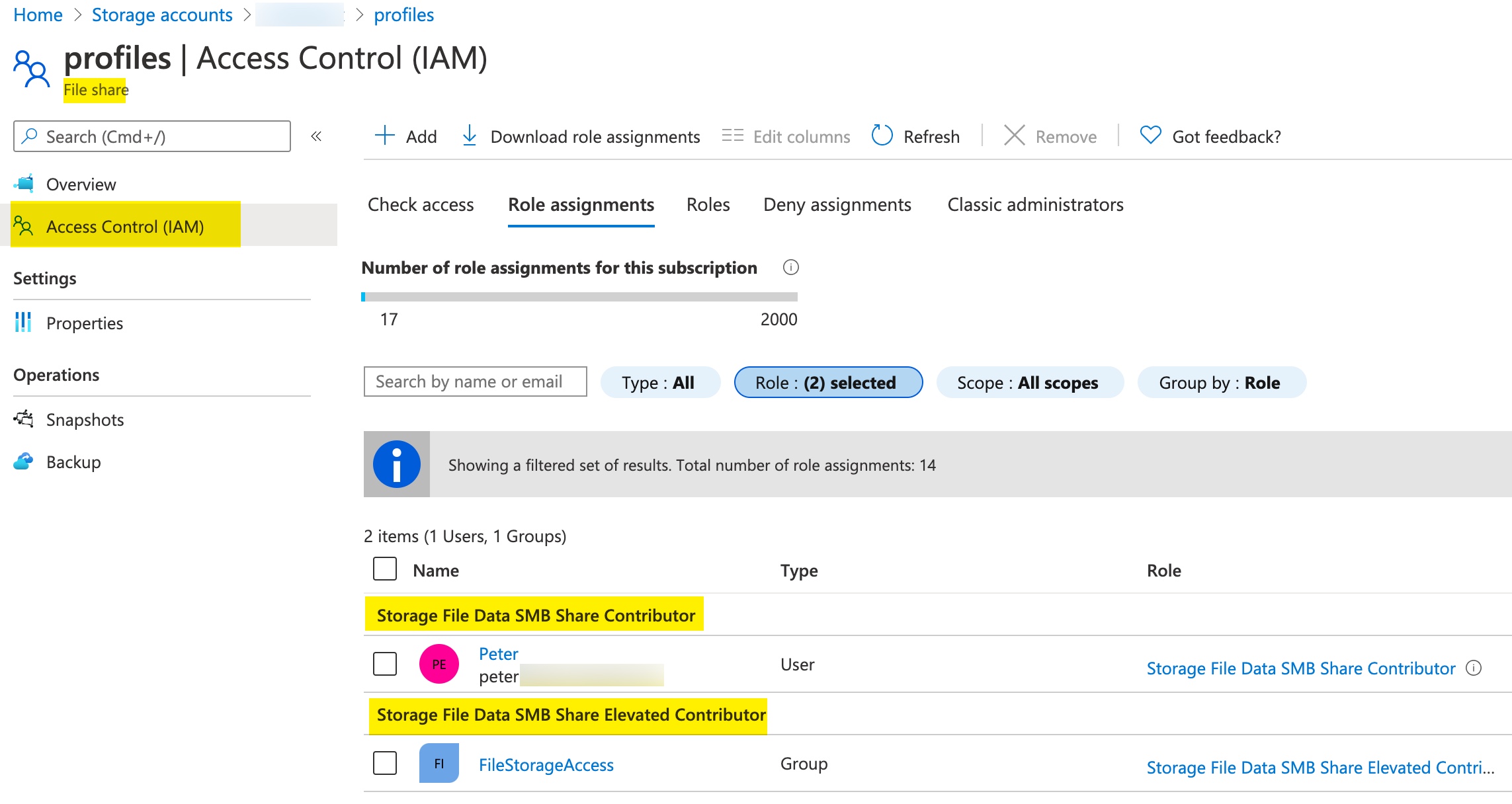
Also the "adds@...." user is not allowed to change the permisssions of the File Share. But the user is allowed to read and write to the File Share.
It's almost the same like in the on-premises world:
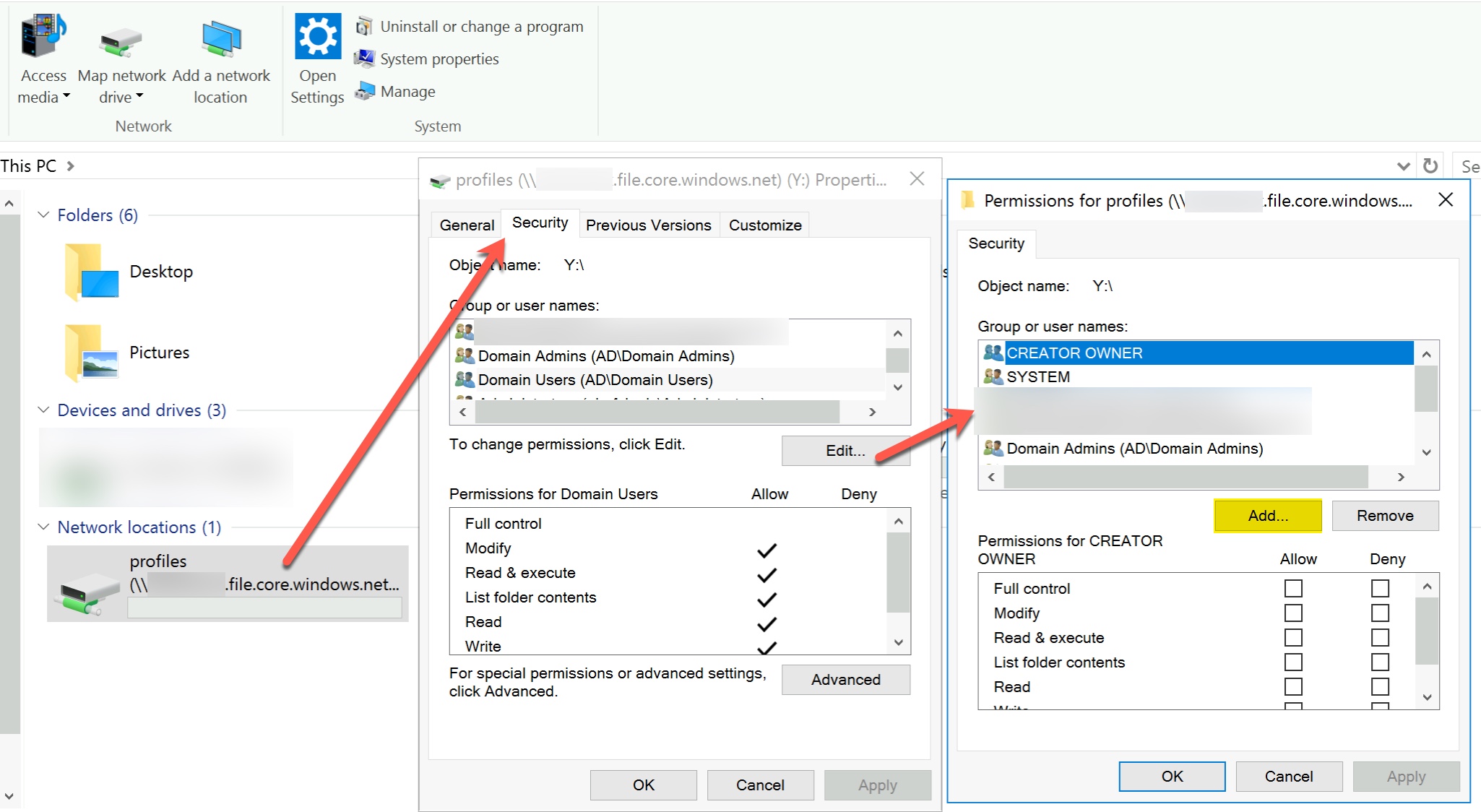
The permissions you see in your screenshot you can compare with the "Share Level Permissions" on a Windows Server with file shares:
- Storage File Data SMB Share Reader -> Only read access on the share and containing folders and files (Read)
- Storage File Data SMB Share Contributor -> Read/Write access on the share and containing folders and files (Modify)
- Storage File Data SMB Share Elevated Contributor -> Full access on the share and containing folders and files (Full)
The permissions you can see in the explorer in my screenshot above are the NTFS Permissions.
In combination of the "Share Level Permissions" and "NTFS Permissions" the most restrictive permission "wins".
This means the "adds@...." is not allowed to change the NTFS permissions, because he is in the "Storage File Data SMB Share Contributor" role. To allow this user to change NTFS permissions he needs to be in the "Storage File Data SMB Share Elevated Contributor" role as well.
More details here: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-ad-ds-assign-permissions
----------
(If the reply was helpful please don't forget to upvote and/or accept as answer, thank you)
Regards
Andreas Baumgarten