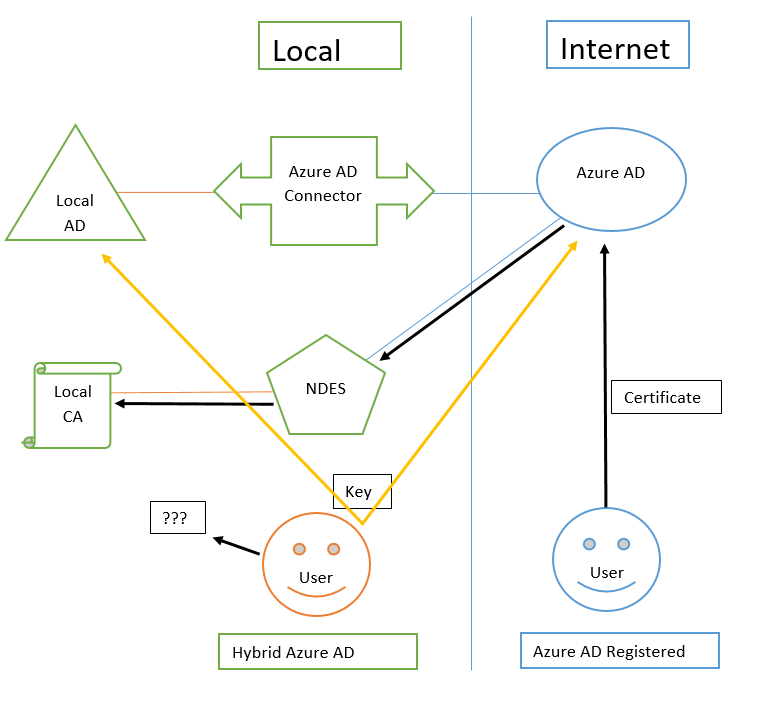
The question can probably be considered closed
Windows Hello (Hybrid) + Key + RDP = Windows Defender Remote Credential Guard
This information is modestly mentioned in the article when planning Windows Hello
hello-planning-guide
Need it on every page Windows Hello (Hybrid) Key Trust remind about Windows Defender Remote Credential Guard :)
remote-credential-guard
Many thanks to @Pierre Audonnet - MSFT for his note about assigning rights - You just need regular RDP permissions (or example by being a member of the Remote Desktop Users local group of the target)