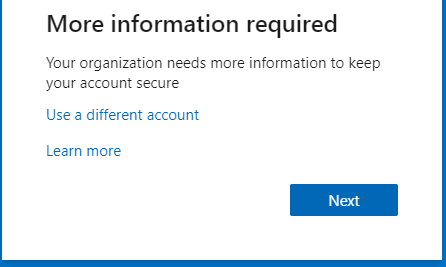
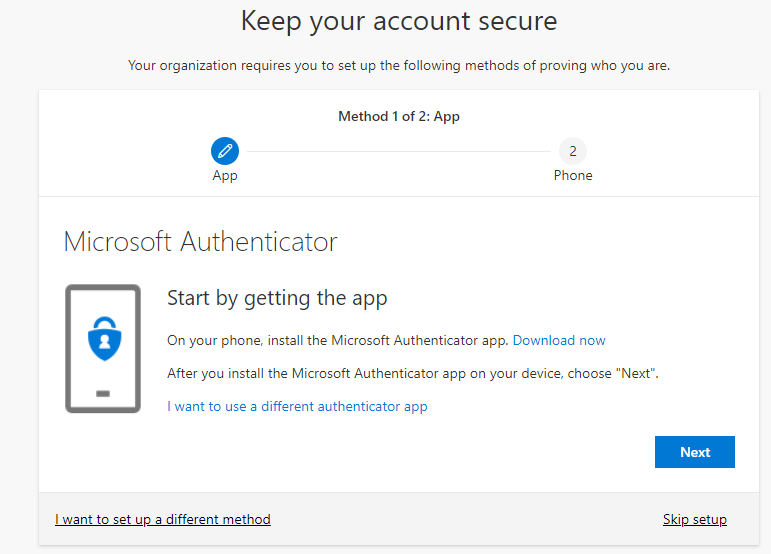
@Linda Renate Andersen
Thank you for the details! I tried to replicate your issue by creating the same CA policy you mentioned for Administrators and All Users, I'll post my steps below.
1.Created a test user with Global Admin permissions.
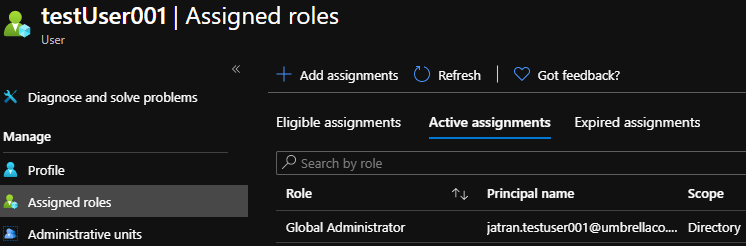
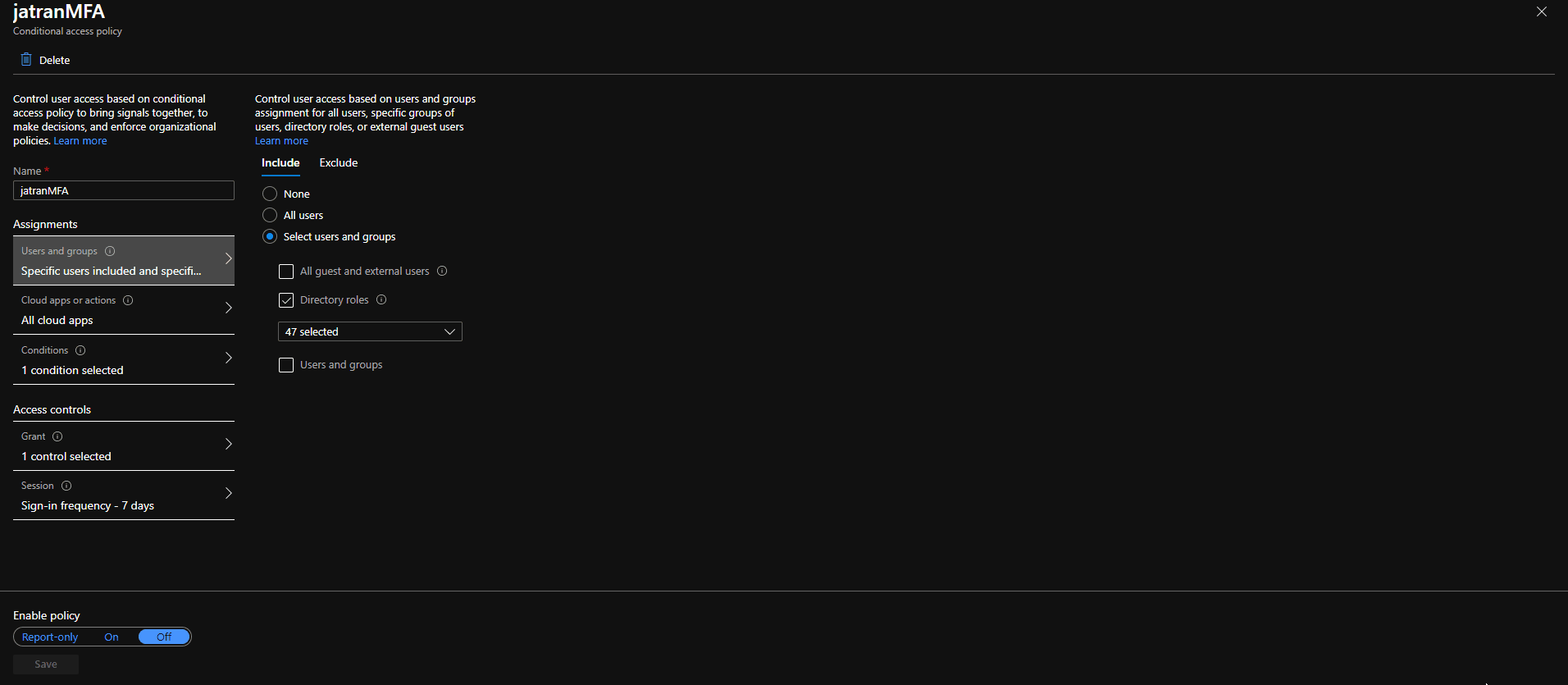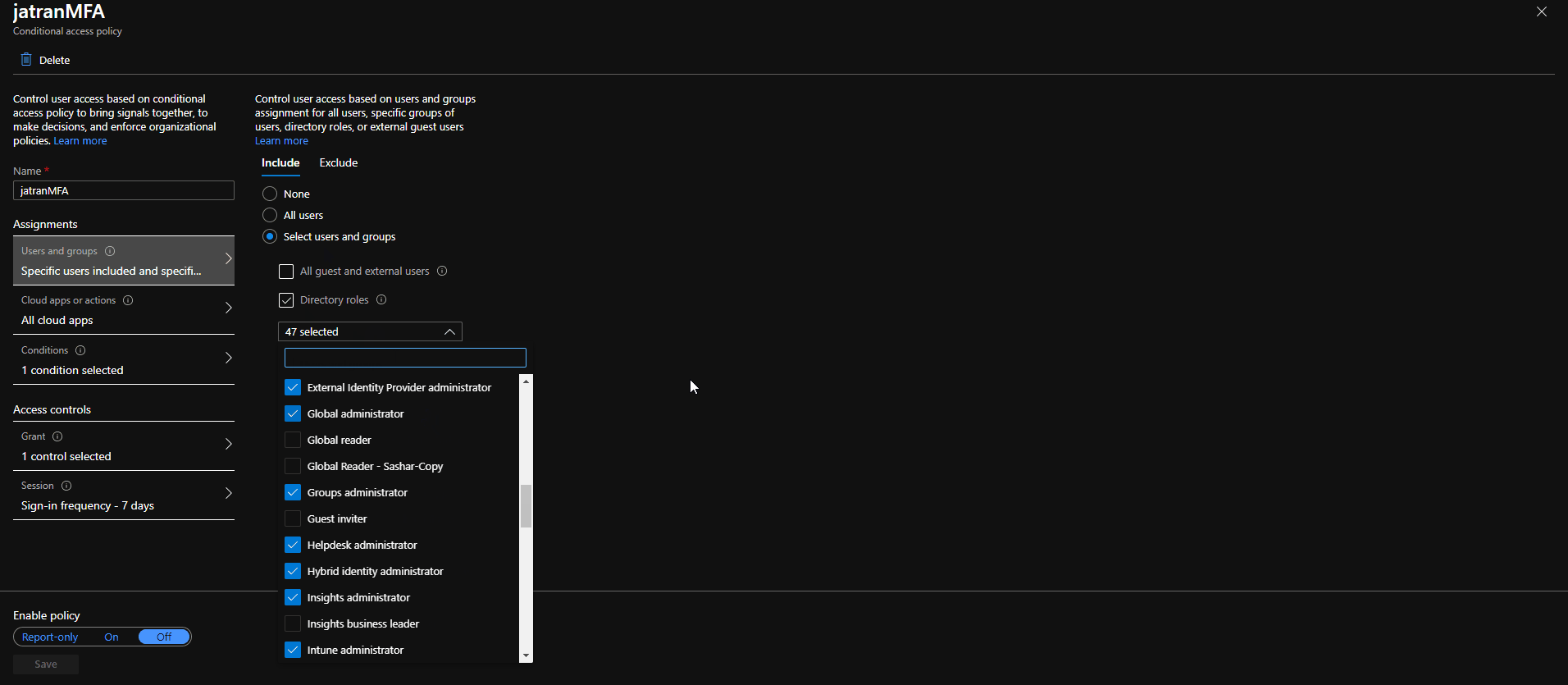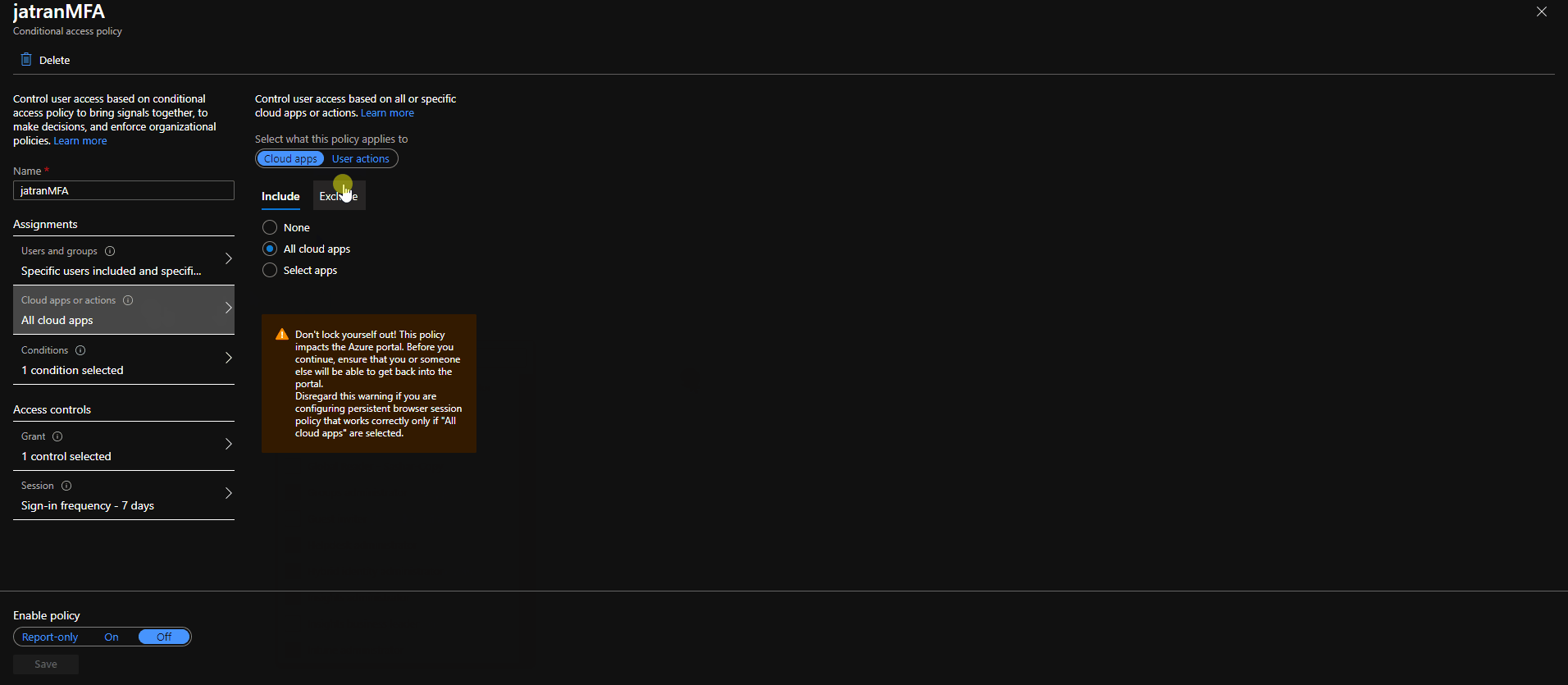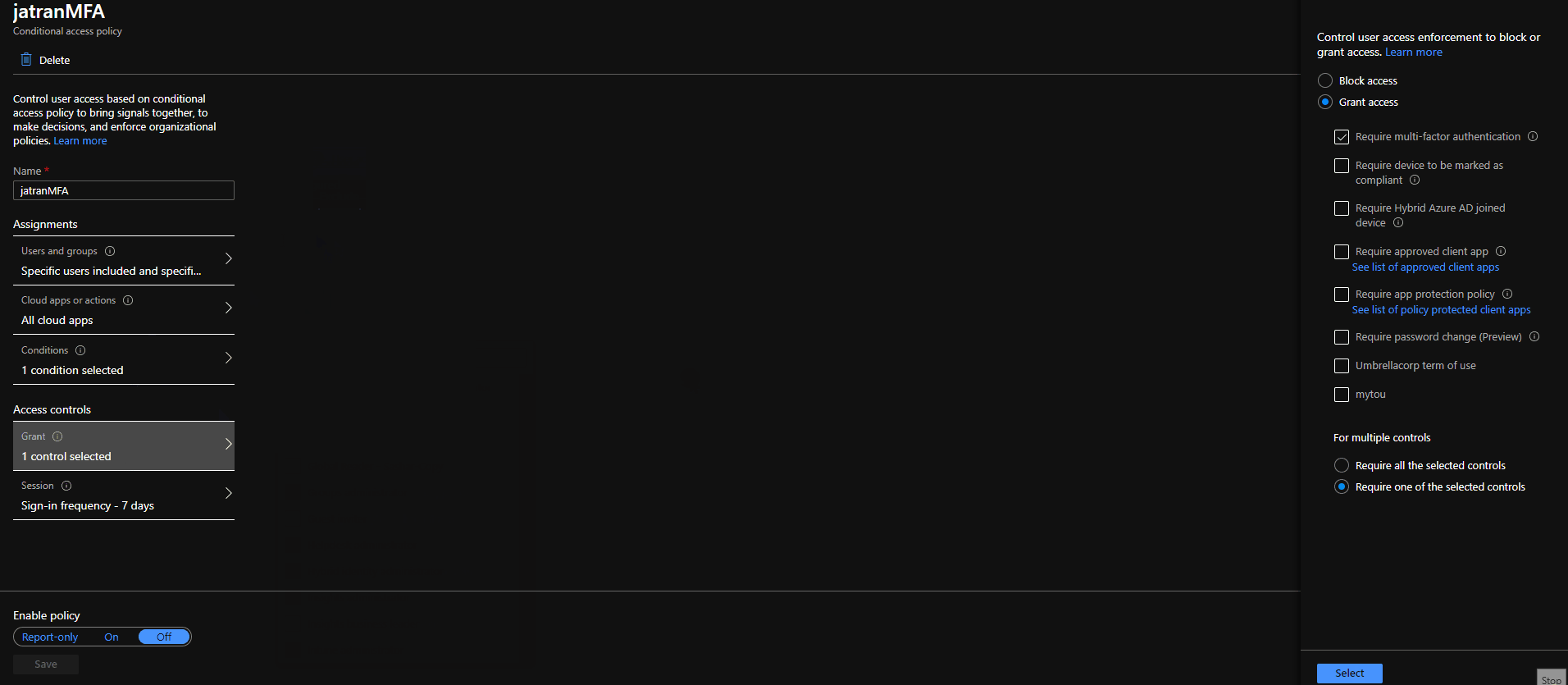
2.Created a CA policy with the same exact specifications as you mentioned except I included all Admin directory roles.
3.Signed in with a user that was excluded from my CA policy and one that wasn't.
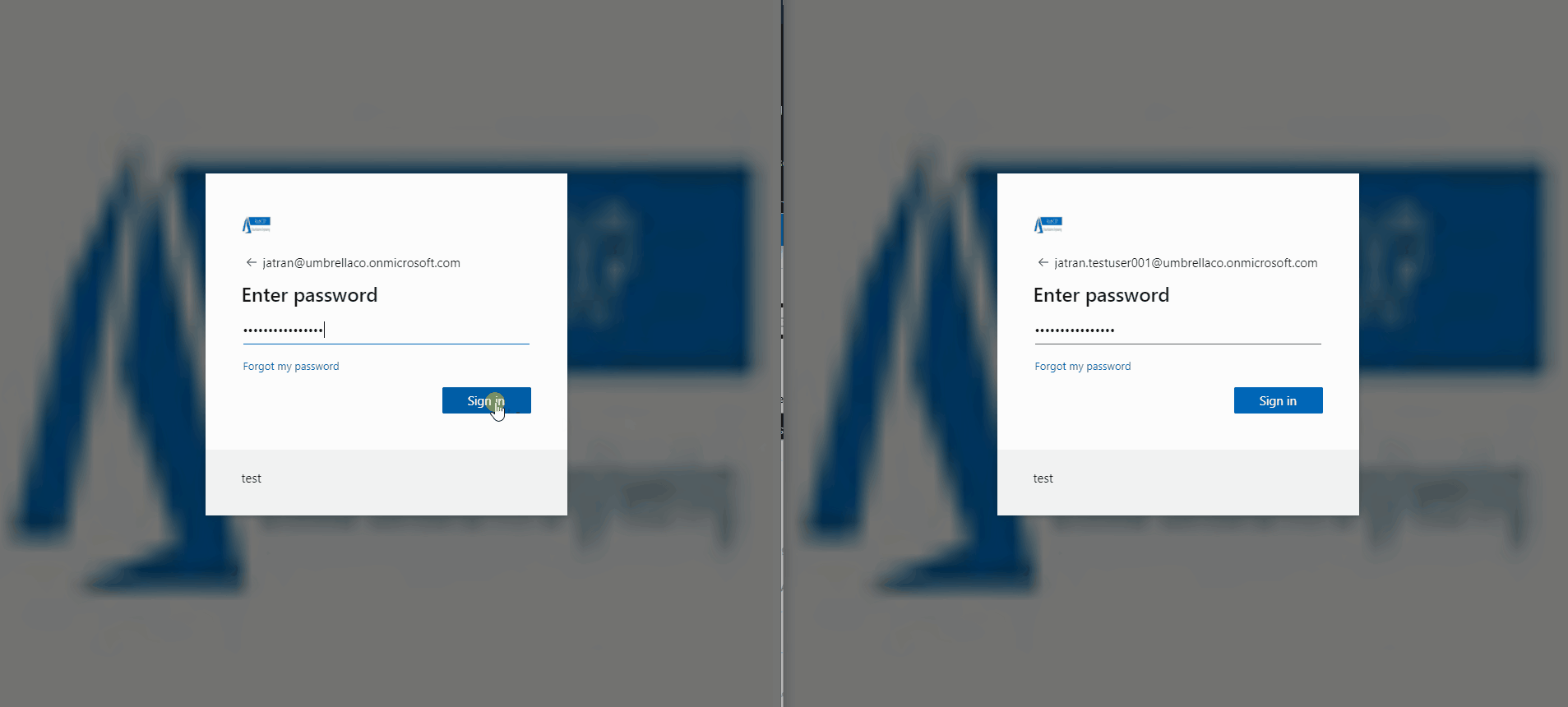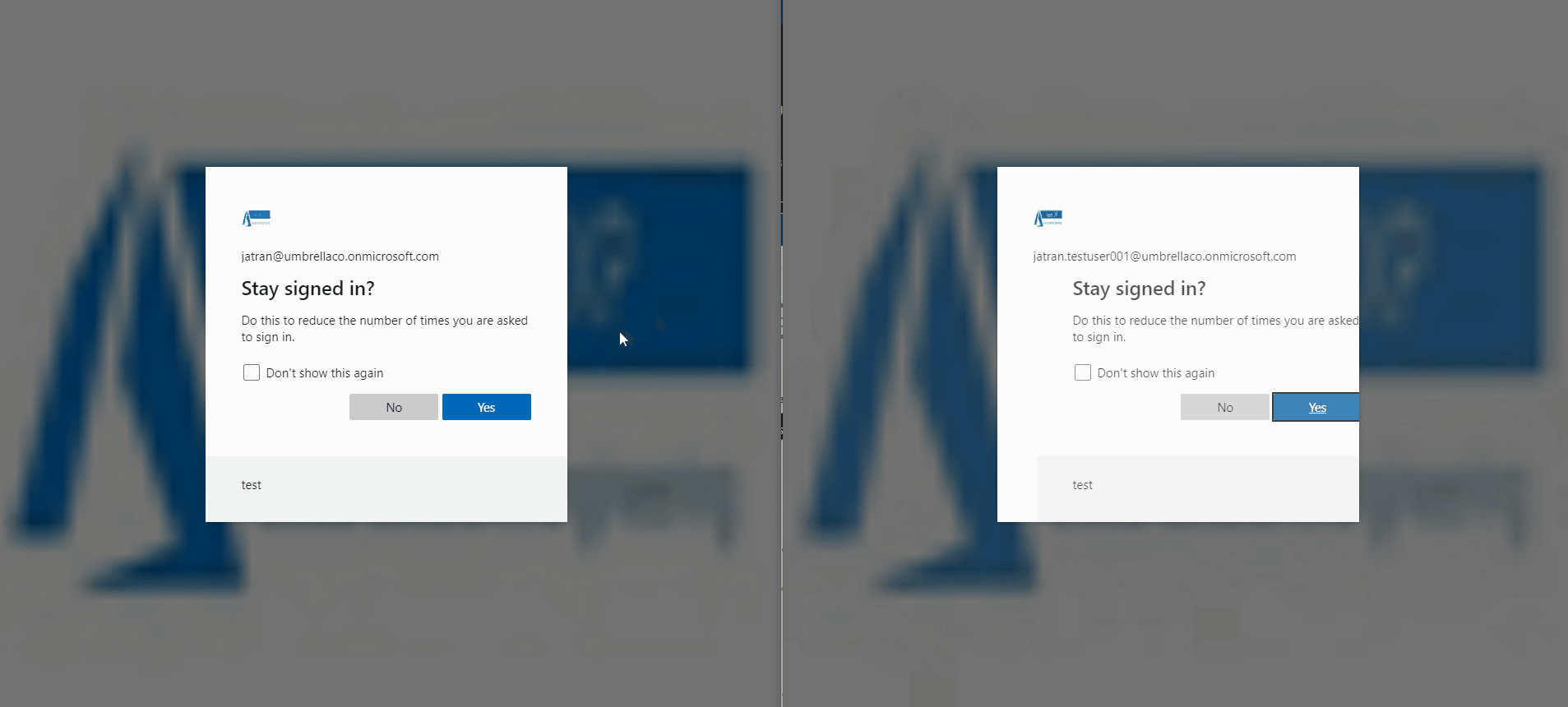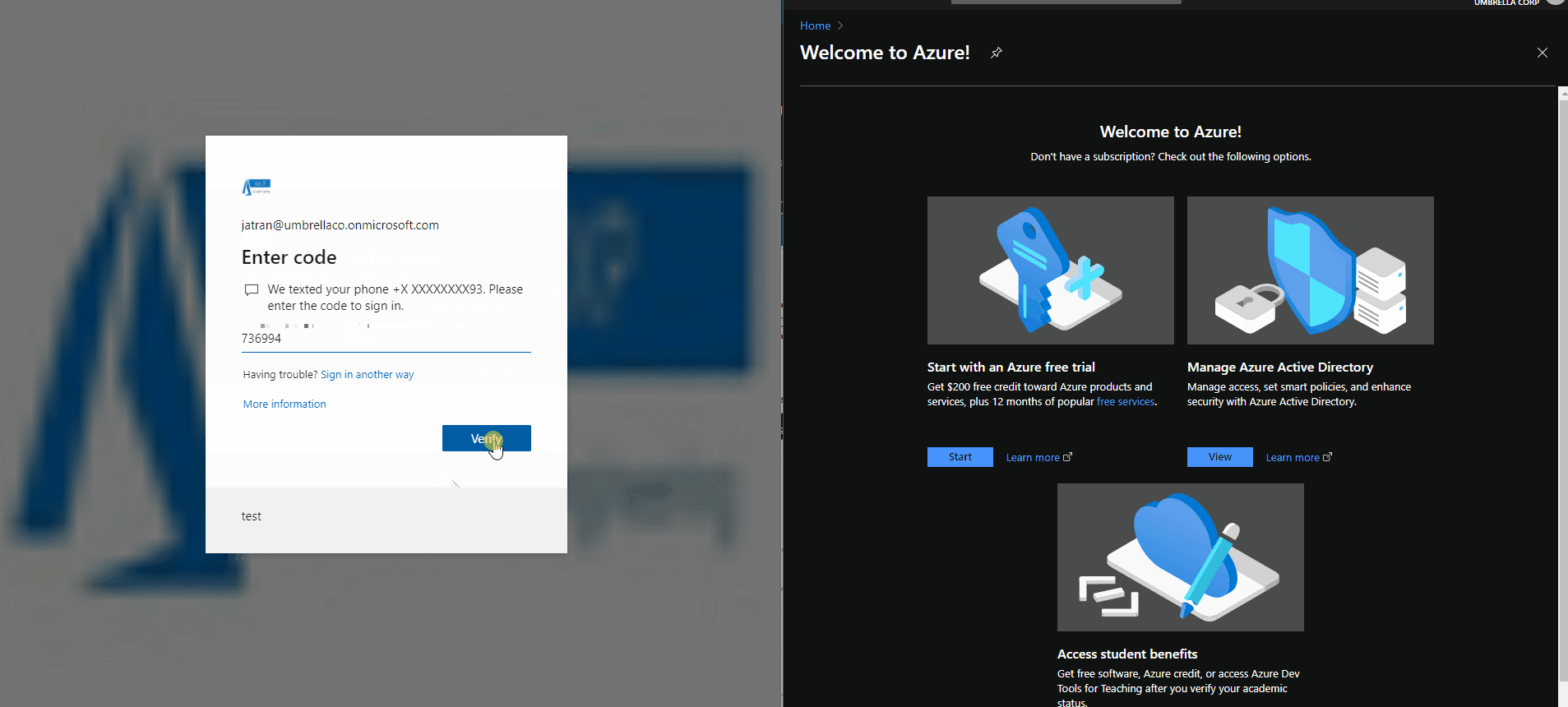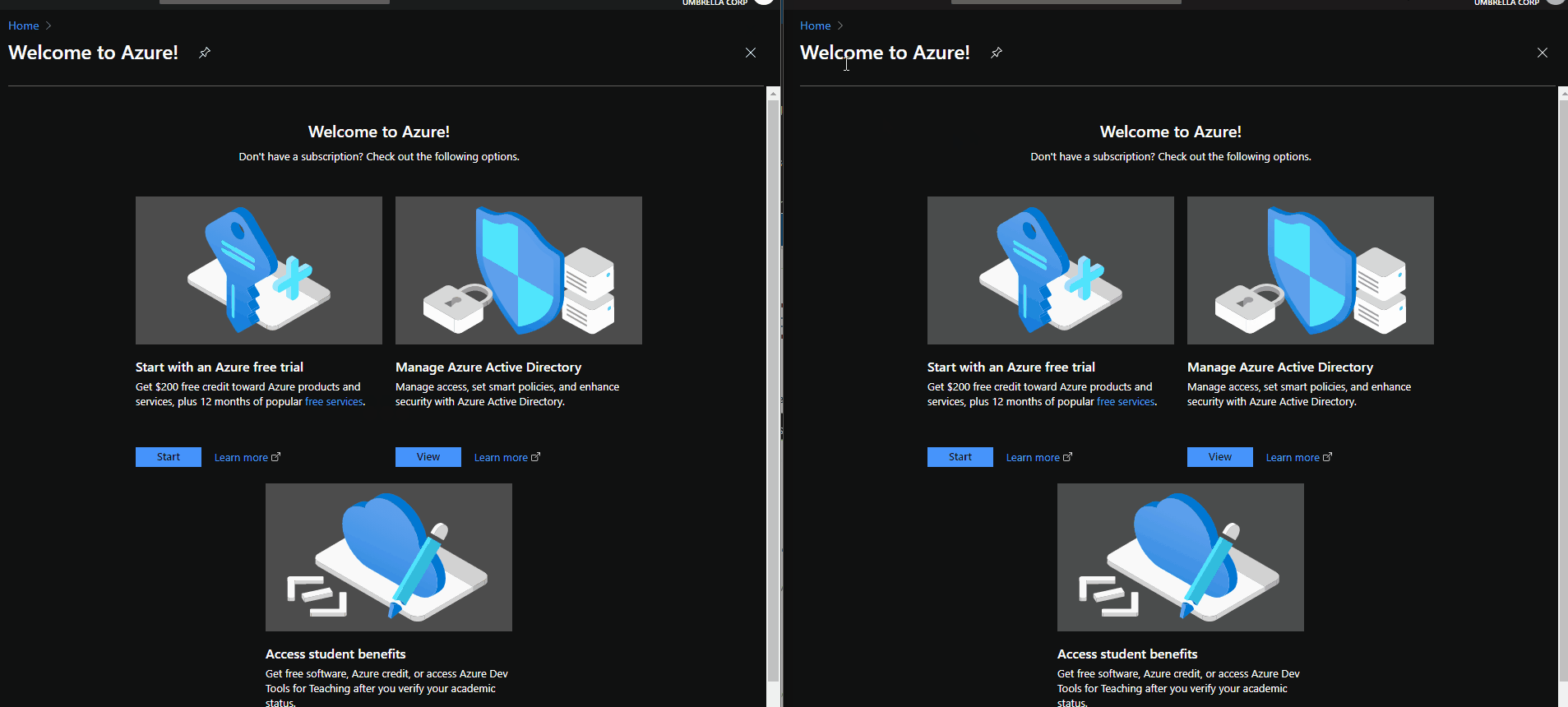
I also noticed that I forgot to add "device platform: Any device", which I selected at the end and was able to log in without MFA for my one excluded user. Additionally, I removed Global Admin permissions and selected "all users" within my CA and was still able to log in.
If you'd like our Support Engineers to take a close look into your environment, please let me know.
Thank you for your time and patience throughout this issue.
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.