I'm building a SPA that's using the oidc-client JavaScript library to authenticate to Azure AD using the OAuth 2.0 authorization code flow with PKCE to obtain an access token to use a custom (Java) API.
In order to be able to validate the access token I created a custom scope as explained under the Problem 1: Azure AD returns invalid JWT access token section at Making Azure AD OIDC Compliant and provided it to the oidc-client library so it is included when authorizing. I got authorizing and requesting initial access and refresh tokens all working as expected.
However when refreshing an access token using the /{tenant}/oauth2/v2.0/token resource I received a 400 Bad Request response containing this error message:
AADSTS90009: Application 'redacted-client-id'(redacted-client-id) is requesting a token for itself. This scenario is supported only if resource is specified using the GUID based App Identifier.
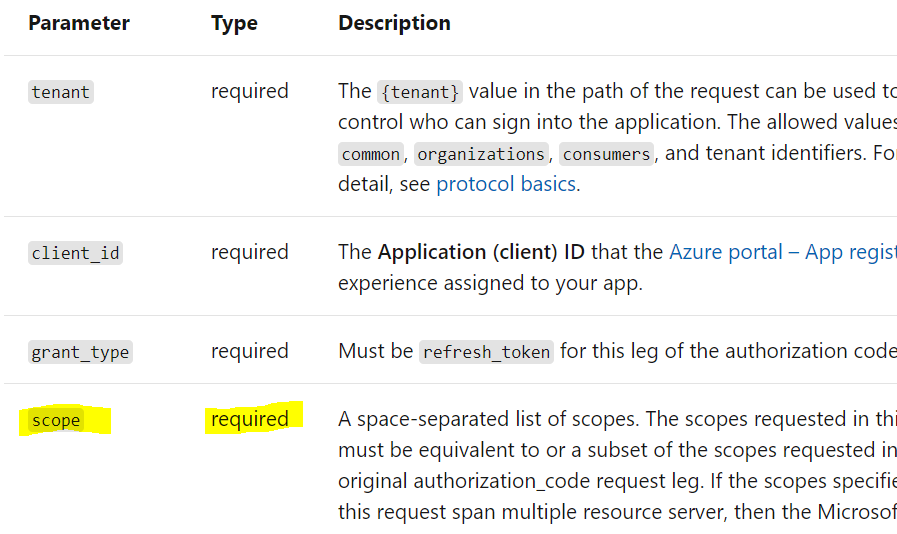
Eventually I found I could successfully refresh the access token by supplying a scope parameter with my custom scope based on it being marked as required for /{tenant}/oauth2/v2.0/token requests to refresh the access token. Is this is what would be expected to fix the problem? I've been confused because the error message talks about specifying a resource, and doesn't make any mention of a scope.