Hello @Rahamim Levi ,
I once again carefully reviewed the entire post information, my understanding now is this.
1.The user PC have not connected to AD domain;
2.But when the user's password was about to expire and the user was forced to change the password via office 365 password writeback system and without line of site to the domain controllers.
3.The new password will be write back to AD domain.
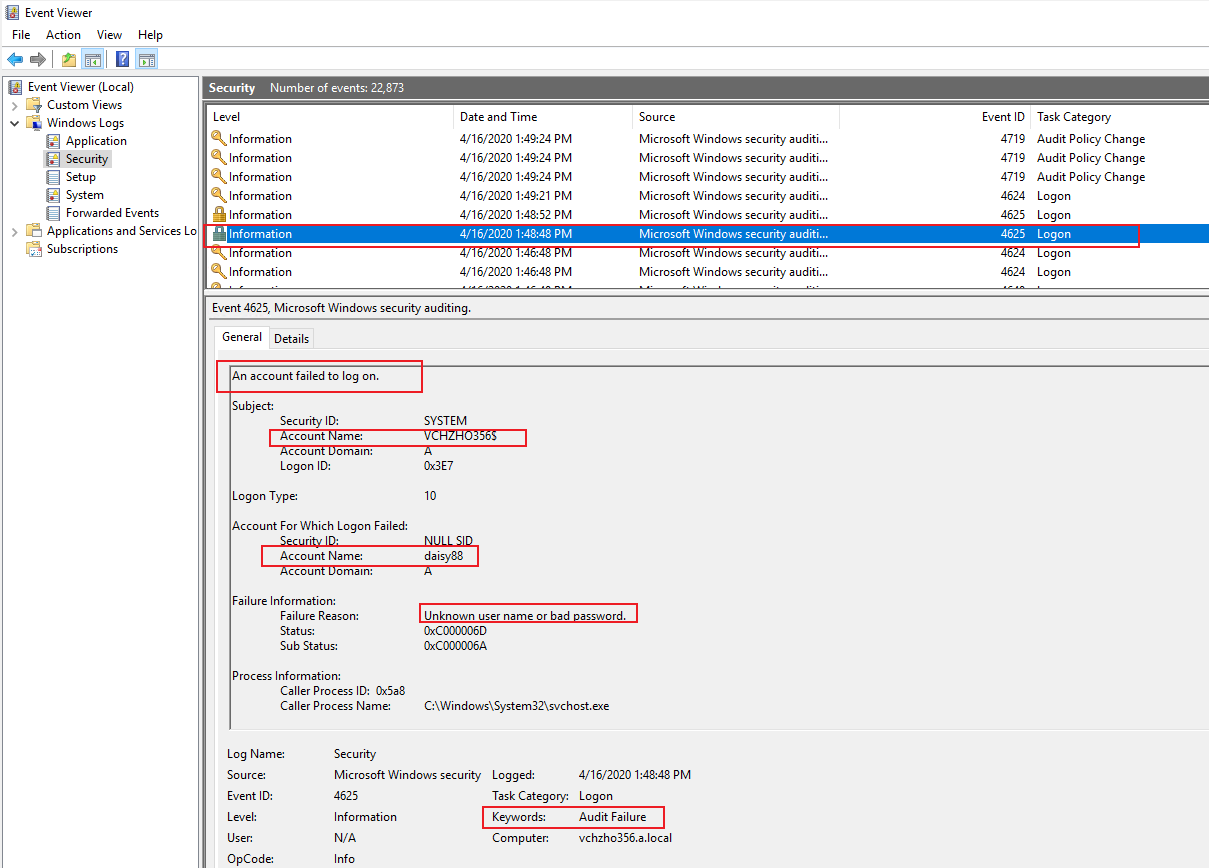
4.The users use old credential to logon their PCs (MECM clients) and the MECM client is using Integrated Windows Authentication to send messages to MECM DMZ server.
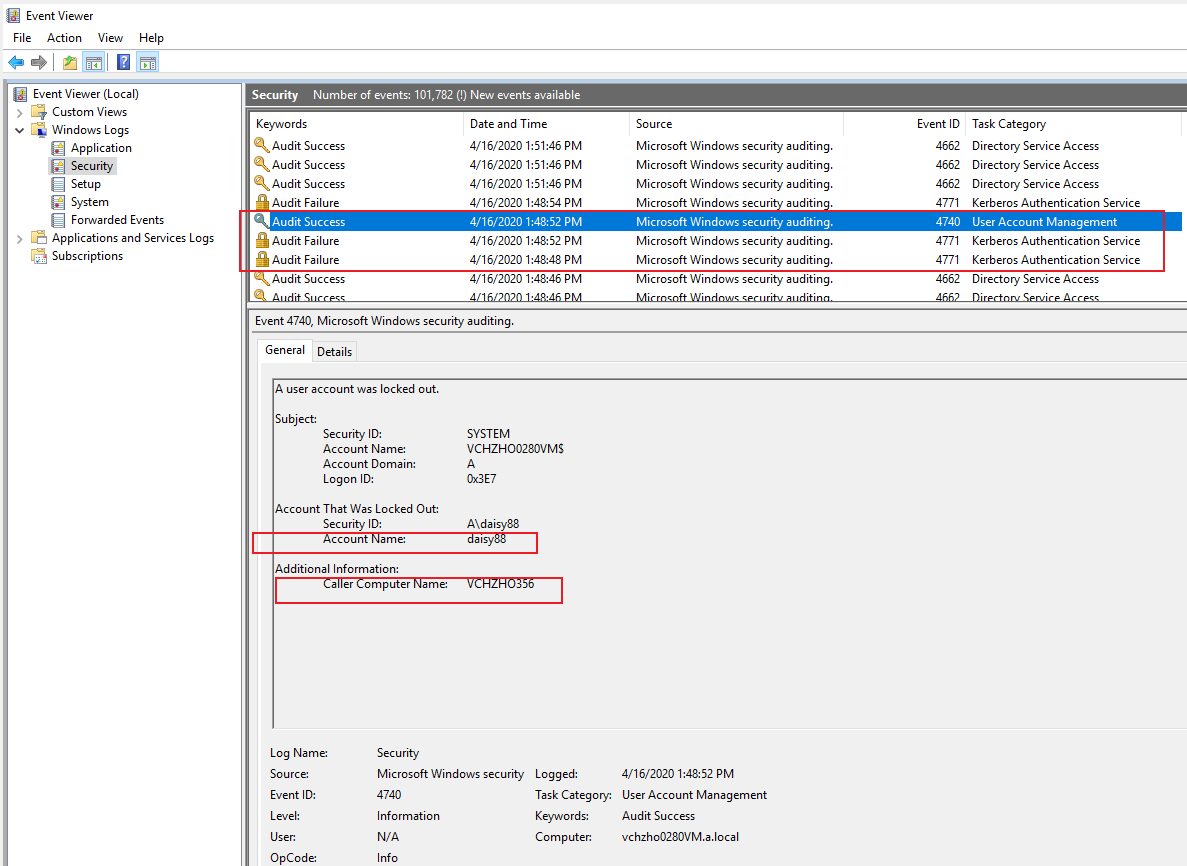
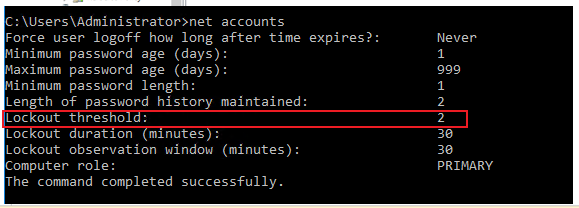
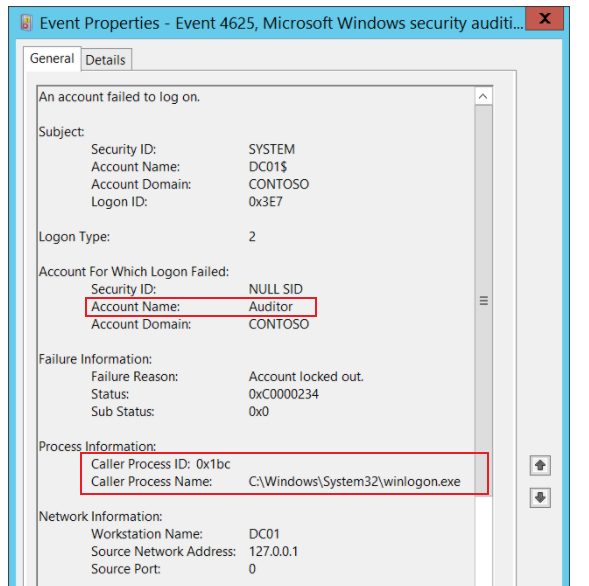
5.Because there is no such user credentials on MECM DMZ server, the MECM DMZ server can not authenticate those user account and password, then MECM DMZ server will pass the credentials (there are user accounts and old passwords on DCs) to the domain controller (there are user accounts and new passwords on DCs) for authentication. At last, the authentication will fail, so the account will be locked out.
If anything I misunderstood, please correct me.
If my understanding is correct, here is my suggest for your reference.
1.Prevent MECM clients from communicating with MECM server.
2.Or make MECM clients connect to AD one time via VPN, after the user logon MECM clients using new credentials, we can stop using VPN again.
Hope the information above is helpful.
Best Regards,
Daisy Zhou