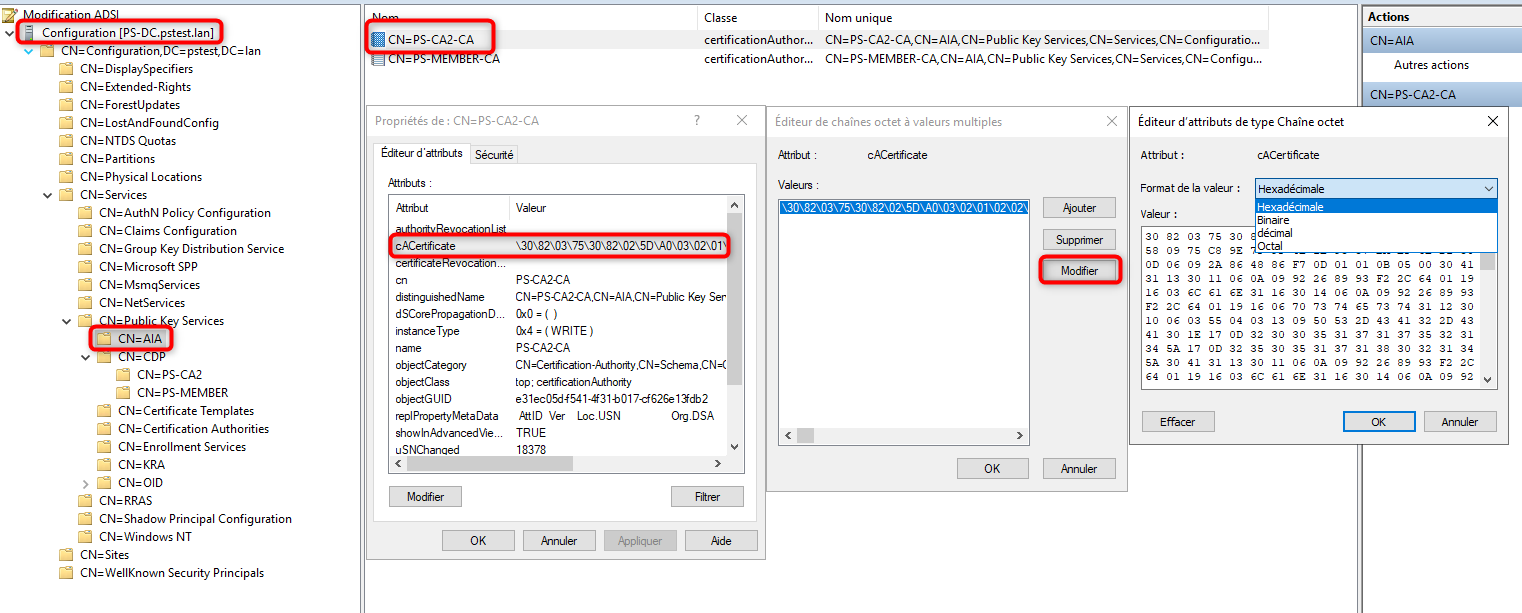
I see you already can get byte array from cACertificate DS attribute. Then you can construct X509Certificate2 object:
$dsAIA = get-item "AD:cn=ps-ca2-ca,cn=aia,cn=public key services,cn=services,$((Get-ADRootDSE).configurationNamingContext)" -properties cACertificate
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2 @(,$dsAIA.cACertificate[0])
then use $cert to access necessary certificate information.