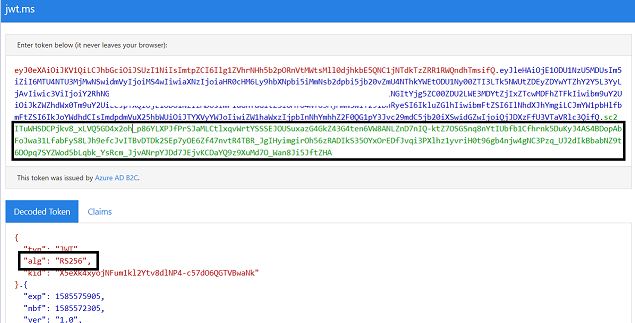
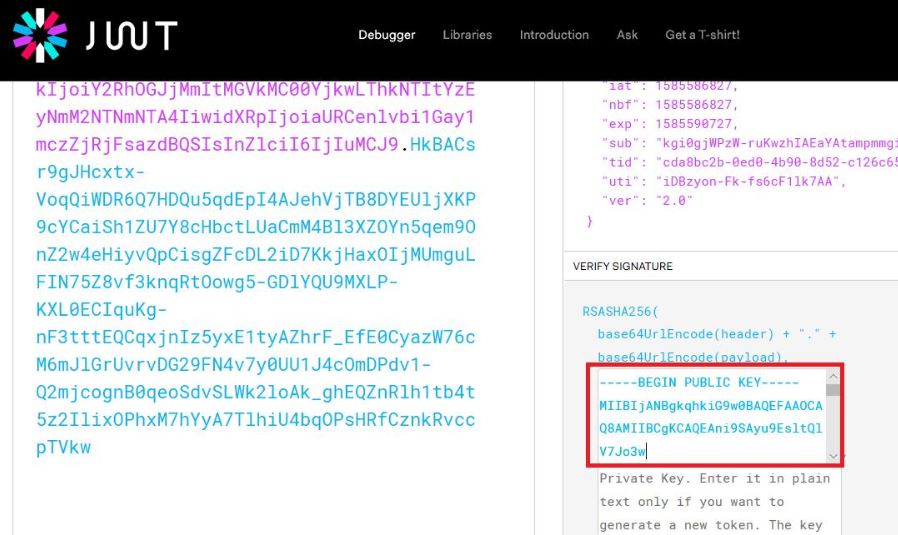
@Harjani, Ashish This is because jwt.io is not able to fetch the public key and and is unable to validate the signature. Please refer to the screenshot below which is captured with a token issued via standard AAD and not IEF. There is a slight difference in how the public key is fetched in case of token issued via IEF, which might be the reason why you don't see public key on jwt.io for token issued via IEF. You can read more about signature validation in B2C here: https://learn.microsoft.com/en-us/azure/active-directory-b2c/tokens-overview#validate-signature
-----------------------------------------------------------------------------------------------------------
Please Accept as answer wherever the information provided helps you to help others in the community.