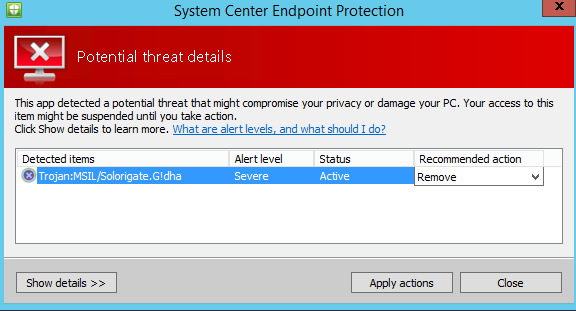
It finds it, we had it.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Can Microsoft confirm if SCEP 2012 protects against the SolarWinds hack:
=====================================================================================================
Process Information
file_operation_closed
file-path*: “c:\windows\syswow64\netsetupsvc.dll
actor-process:
pid: 17900
Window’s defender Exploit Guard log entries: (Microsoft-Windows-Security-Mitigations/KernelMode event ID 12)
Process”\Device\HarddiskVolume2\Windows\System32\svchost.exe” (PID XXXXX) would have been blocked from loading the non-Microsoft-signed binary
‘\Windows\SysWOW64\NetSetupSvc.dll’
It finds it, we had it.


Hi @Joel Heideman ,
Maybe this blog will help you: https://blogs.microsoft.com/on-the-issues/2020/12/13/customers-protect-nation-state-cyberattacks/
Regards,
Youssef Saad | New blog: https://youssef-saad.blogspot.com
Please remember to ** “Accept answer” ** for useful answers, thank you!
Thanks, but I already have all of that data.
There is no confirmation if SCEP 2012 protects against this that I have found.