@Somnath Shukla
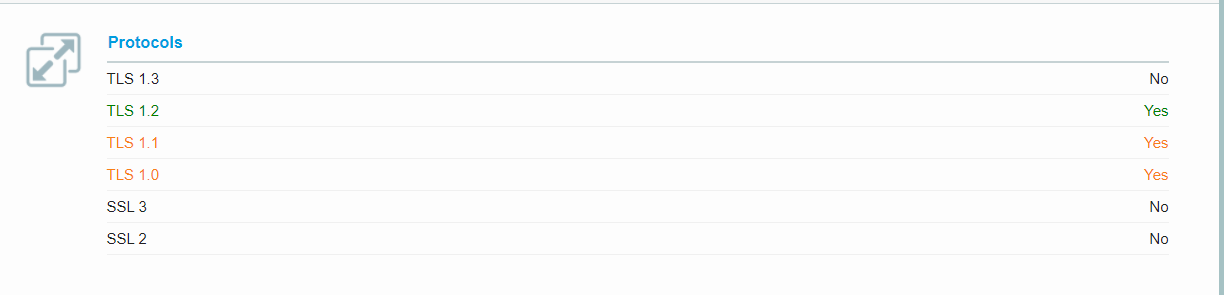
Thank you for your post! Data may be restricted to TLS 1.2 through configuration on the client side.
All traffic to Azure Key Vault for authentication, management, and data plane access, is encrypted and goes over HTTPS: port 443. However, there will occasionally be HTTP [port 80] traffic for CRL. Azure Key Vault continues to allow TLS 1.1 and TLS 1.0 data to be ingested. Data may be restricted to TLS 1.2 through configuration on the client side.
For more info:
Azure Security Baseline for Key Vault - 4.4: Encrypt all sensitive information in transit
Access Azure Key Vault behind a firewall
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.